Glad to help. I am by no means an expert, but have managed to learn quite a bit over the years through trial and error, and help from others.
This might be more information than you wanted, but just to be as thorough as I can in case others may want to follow along. So here it goes....
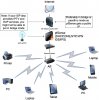
In general, opening ports on a firewall to access cameras or other services is a recipe for disaster. The best approach is to host your own VPN service, so you can access your entire network, including embedded devices which you cannot install a VPN client. This is different than the so called "privacy" VPNs services which claim to protect your privacy, which is not really true. All you are doing in that case is handing over all you data to a third party, potentially off shore, who may be subjected to subpoenas. There certainly are use cases for privacy VPNs, e.g. if you live a country which bans access or monitors activity. I simply ignore all the YouTube shills who promote privacy VPNs in exchange for a kickback.
Ideally you put your ISPs kit in bridge mode so pfSense gets a public IP. The only caveat is if your ISP also provides IPTV or VoIP services.
Remote VPN access can still be made to work without a public IP address using Tailscale, but it is not ideal.
Tailscale MESH VPN is a data plane on top of Wiregaurd VPN, which uses a coordination server to establish P2P communication. Tailscale uses WG GO, so there is a slight performance hit over a straight WG implementation, but nothing that I notice when remotely viewing cameras or accessing my network. The advantages of Tailscale are , it uses any number of existing identity manager mechanisms (Google, Apple, Github, etc.). Tailscale will traverse any levels of NAT and CGNAT, thus it does not necessarily need a public IP, unlike a straight WG VPN which requires at least one node to have a public IP and your WG VPN will be inaccessible if that node is down.
Tailscale has clients for every OS platform on the planet, has a free tier for up to 100 nodes, allows you to select exit nodes to obfuscate your IP address when accessing content remotely. If you go the pfSense route, I recommend Christian McDonald tutorial for Trailscale.
As far as pfSense performance, it all depends on the bandwidth you are paying for and the kit you run it on. In my case, I pay for 300mbps symmetric (actual results are 375mbps). There is really no discernible difference when a run a
speed test directly from the ISPs modem vs from a wired client on my home network behind pfSense.
As mentioned, there is a slight performance hit when using Tailscale to access you home network remotely over other self hosted VPN implementations.
View attachment 178604
Links:
pfSense:
pfSense® - World's Most Trusted Open Source Firewall
Tailscale:
Tailscale
Christian McDonald Tailscale config tutorial:
Tailscale on pfSense Software!
How to connect a Stratum 0 GPS+PPS source to pfSense for less than $50:
GitHub - elvisimprsntr/pfsense-ntp-gps: pfSense NTP GPS Server
Protectli Vault Appliances:
Protectli: Trusted Firewall Appliances with Firmware Protection
 www.bleepingcomputer.com
www.bleepingcomputer.com


 .
.