SecuritySeeker
Pulling my weight
You mean the version I uploaded here? I have no reason to doubt that it is for the SD-M5.Not sure if that firmware is definitely for the SD-M5?
You mean the version I uploaded here? I have no reason to doubt that it is for the SD-M5.Not sure if that firmware is definitely for the SD-M5?
I can confirm that 13.01.01.30 works with SD-M5... Now if its meant for it... might be another story. I downloaded it from YooSee and force updated it with the IPCTest Tool. But in the end it didn't do anything but give me 1fps more half of the time. Now it just bounces back and forth between 5 & 6fps. FML... But in B&W Im able to maintain 10-11fps now where with 13.01.01.34 I was only able to achieve 5.Not sure if that firmware is definitely for the SD-M5?
create_pipe
dhcp.script
,8"k\iMq_;K
Jtd`+;0 &$
d7{^5{i)d*
_8x^|WolSU
a_f]v\5v,=
]x"<["kx&\
:.vE\^004c
Y$a)d$$(5w--\
29NCwUHwuH
M)"U}b9/dF
O'{<x^|WolS
A-Hx^lValSU
(rg@>7D,':
@,@=2@5&@1
&rS7--RQeU
$Grg<zNsQ?z
/e)hf(X:Fg`_
^7c?q%+w@W
Nm'l-h#;Mmn
t/"G2/J>ud^
yr";OvEyoJ
K ;SJt%hnv
<e,)@sSe}S
dfKCOzw"Q_
.!mS)j7J~U}
w>XJ3xV<DT~
gD )=''}*H
FHx^lW{pTW
<Px^\T]h[e
zdY~3r^5Gd<o
N'g^"/'unY!
BjHp&3PpvCd
??.+`h4hd
x8Sn?Y*==A
0SO_.crc~8
'-vzx^\WmpTW
hvgreg7@KL
BEO:|aQ^BJ
{9ag^&y.v:
TOa>"<o)z8
X;?B?)'|&E
Oo9OM[i]G]
HvHiLj46>&
9oi'oM'oM'
|pWD}'\@x^|
@jFgIjFWyj
lWK'+*}}es
3}LMpFeM`lXGz
J872W2?272G
5XA.xL=Ut=
tg&7ub$"H%
Q'>=*5<FvR
)BV*"l9B.("]
%oK!/XS #S
ehy* <p~#|
'~<.5q.Gux
+sH5LfM`+b/t
d/kCfO8DOl
:DHComputeSharedSecretKey
RTMP_TLS_Accept
HandleMetadata
RTMPSockBuf_Fill
RTMP_SendChunk
RTMP_SendPacket
i>q.i n\p=
4uiJJJrrRR
>"C334E#33Q2S3
8<;neY/8*e
v2w2v2yrw2z
4HwwwwwwIwH+%
ay|_8Z9wS?
UP`pX`o?wc
2qt\]PoH!T
IEEhEEqII0XI
&pP }3f!A@
!qv\QT~ryDN
`NL O H@L,
=>p>*r]R{w
97EOuw_~^d`
TW:\:Ij!]$]/
]4J1~a\cbb
`- /shell_debug
upgfile_ok
version.txt
XiRNf2L$(5'5
S-arj<\>uz
Authentication.xml
]CreateProfile.xml
DeleteProfile.xml
Device.xml
GetAudioEncoderConfiguration.xml
GetAudioEncoderConfigurationOptions.xml
\GetCapabilities.xml
GetDeviceInformation.xml
GetNetworkInterfaces.xml
GetProfile.xml
]GetProfiles.xml
C%GetServices.xml
GetSnapshotUri.xml
~GetStreamUri.xml
GetSystemDateAndTime.xml
GetVideoEncoderConfiguration.xml
GetVideoEncoderConfigurationOptions.xml
xGetVideoEncoderConfigurations.xml
GetVideoSourceConfiguration.xml
GetVideoSourceConfigurations.xml
'GetVideoSources.xml
NetworkVideo.xml
OnvifSetTimeTempFile.xml
SetSystemDateAndTime.xml
jjrSetTimeTempFile.xml
SetVideoEncoderConfiguration.xml
tptz_ContinuousMove.xml
tptz_GetConfigurationOptions.xml
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
OiCCPPhotoshop ICC profile
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
Gar^Km@IDJ
tEXtSoftware
Adobe ImageReadyq
,y5uU5.png
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
OiCCPPhotoshop ICC profile
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
VpGHFpFhFHGHW
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
OiCCPPhotoshop ICC profile
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
.kP>Fww.png
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
aa=s(12.png
MiCCPPhotoshop ICC profile
tEXtSoftware
Adobe ImageReadyq
021u5qtu3quq350
tEXtSoftware
Adobe ImageReadyq
KjqrQfAIf~
_in.\uqIP*
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
icgy5uU5.png
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
a=s(12.png
ia=s(12.png
MiCCPPhotoshop ICC profile
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
tEXtSoftware
Adobe ImageReadyq
OiCCPPhotoshop ICC profile
KjqrQfAIf~
_in.\uqIP*
~^.^:x^|S[h
'PushMesg.txt
'PushMesg.txt
LowPower, string, "
OneButtonCall, string, "
'PushMesg.txt
gpioi2c.ko
gpioi2c1.ko
fgpioi2c1_U2.ko
hi3518_isp.ko
92VpkmDwctH
DoorBell.amr
o5?LGReset_ch.amr
t4,un:J*MWmbA
Reset_en.amr
6Unlock.amr
VoiceControl
WifiLink_ch
/WifiLink_en
:beingcalled.amr
calling.amr
u3zw*/6=z}
key_press.amr
numbers_ch
set_fail.amr
set_ok.amr
O^test_passed.amr
Qwaiting.amr
BonVoyage.amr
"0OClickly.amr
Goodnight.amr
HelloMaster.amr
NeedTFCard.amr
S+%+#k8Q\O
Recording.amr
}Welcome.amr
sok_ding.amr
ConnFailRetryLater_ch.amr
ConnFail_ch.amr
9L,DevOnline_ch.amr
Linking_ch.amr
s!SuggestApConn_ch.amr
`<%z78#$ A
?SuggestSmartlink_ch.amr
WaitLink_ch.amr
ConnFailRetryLater_en.amr
ConnFail_en.amr
2&RwPP<(Et@
/UuDevOnline_en.amr
Linking_en.amr
jxSuggestApConn_en.amr
fSuggestSmartlink_en.amr
T@^0<HEvxg
*o>oY1<`<$
WaitLink_en.amr
upgrade_ch.amr
EzDZ0< 7k1
Eupgrade_en.amr
/lib/ld-uClibc.so.0
__errno_location
__uClibc_main
__bss_start
__bss_start__
__bss_end__
__deregister_frame_info
__register_frame_info
%s(): ioctl failed! <%d:%s>
%s(): open failed! <%d:%s>
%s(): statfs failed! <%d:%s>
FileName="%s", opt = [%d]
%s(): open "%s" failed! <%d:%s>
I'm going to erase:%dbytes, and write(new_app):%dbytes
%s(): New APP size too large!!!
mtd_debug erase /dev/mtd4 0 0x%x
-->> system("%s");
mtd_debug write /dev/mtd4 0 %d %s
#%s: argc is err! (argc=%d)
Usage: %s <filename> [option]
fgUpdateApp Fail!
upgdev pross over!
getSizeForm_mtd_debug
getSizeForm_statfs
fgUpdateApp
GCC: (GNU) 3.3.2 20031005 (Debian prerelease)
GCC: (Hisilicon_v300) 4.8.3 20131202 (prerelease)
.init_array
.fini_array
.ARM.attributesIndeed. I haven't opened mine yet as it was in focus out of the box but I would not be entirely surprised if it has a jtag or uart port exposed. And in any case the microcontroller must have those pins (according to the datasheet it has 3 UARTS, doesn't mention jtag though) so with a bit of soldering...Its running a Linux OS, so it can be hacked. Its not like its running some proprietary OS. I have copies of the firmware now so maybe something can be done with that. I'm sure its encrypted, but there's ways around it. I also read that some of these cheap Chinese cams have a debugging port on the pcb that will allow you to get into the Linux OS so I haven't thrown it the towel just yet. I've realized though that the onvif2 stream doesn't degrade fps. So I in theory if the right lines of code for sub stream were applied to primary stream it wouldn't drop fps, unless the data's just being straight up throttled some how which is also a possibility.

root@kali:~/Downloads# binwalk npcupg13.01.01.30.bin
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
32 0x20 JFFS2 filesystem, little endian
2630636 0x2823EC ELF, 32-bit LSB executable, ARM, version 1 (SYSV)
root@kali:~/Downloads# dd if=npcupg13.01.01.30.bin of=executable.so bs=1 skip=2630636
5652+0 records in
5652+0 records out
5652 bytes (5.7 kB, 5.5 KiB) copied, 0.0338289 s, 167 kB/sI've been meaning to check for that for some time and yesterday I finally had the time to crack this thing open and take a look. Unfortunately I cannot find any exposed JTAG or UART pins. Whatsmore the CPU and its pins are entirely covered by a glued-on heatsink. Here are some hi-res pictures that I took (click image then click on magnifier icon to view in full size):I also read that some of these cheap Chinese cams have a debugging port on the pcb that will allow you to get into the Linux OS so I haven't thrown it the towel just yet.
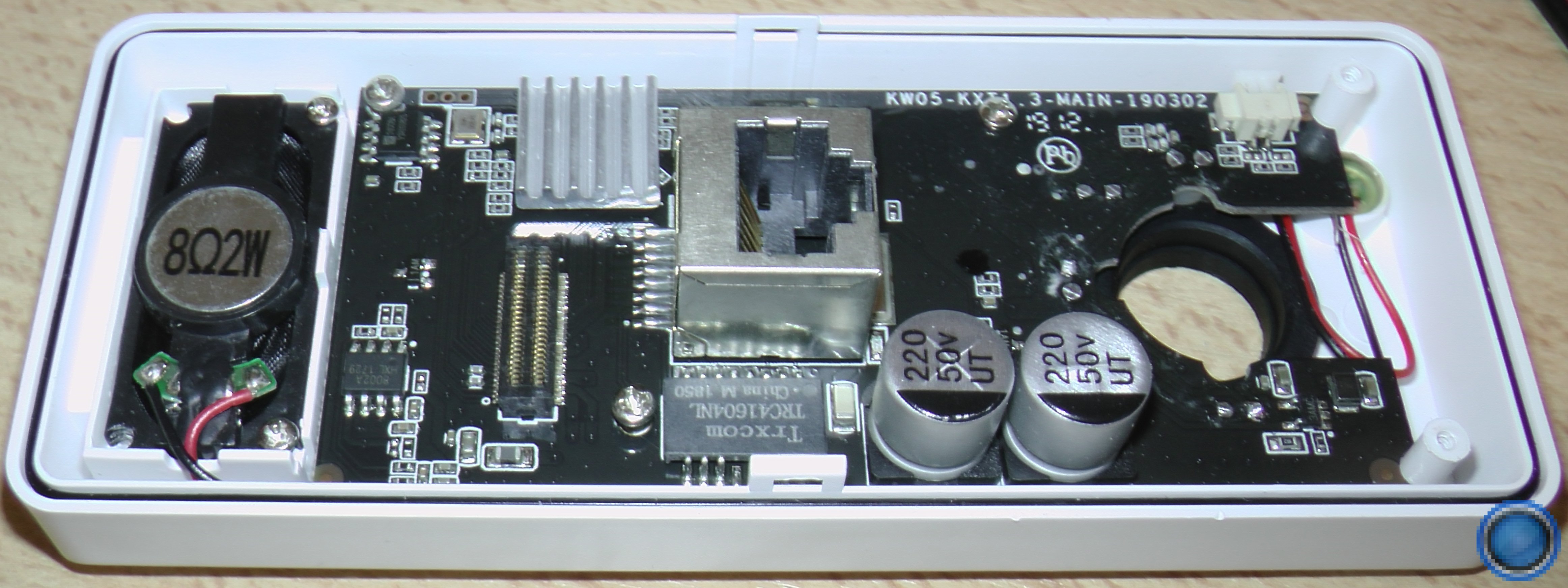



Ah yes, you're right, that's probably the UART connection. Don't know why I didn't spot that.I'd guess that the serial console connection is the 3 pads at the top left corner in the image of the board, just along from the heatsink.

It almost is - the linked firmware consists of an updater executable, as you have surmised, and a JFFS2 file system image that holds presumably the app partition.At first I though that the .bin file might be an image to be copied 1:1 onto the device flash memory but since it only contains the one ELF executable that seems unlikely.

Yes, it does. Good find!The firmware looks like the same format.
apt install python-pip to install one of the dependencies. /_npcupg13.01.01.30.bin.extracted.root@kali:~/Downloads# binwalk -Me npcupg13.01.01.30.bin
Scan Time: 2019-11-21 17:38:40
Target File: /root/Downloads/npcupg13.01.01.30.bin
MD5 Checksum: 3853cfd59864fe5eea2b76260fcf25eb
Signatures: 386
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
32 0x20 JFFS2 filesystem, little endian
2630636 0x2823EC ELF, 32-bit LSB executable, ARM, version 1 (SYSV)
root@kali:~/Downloads# ls
npcupg13.01.01.30.bin _npcupg13.01.01.30.bin.extracted
root@kali:~/Downloads/_npcupg13.01.01.30.bin.extracted/jffs2-root/fs_1# ls
create_pipe dhcp.script img language npc OnvifFile patch shell_debug sound upgfile_ok version.txt wpiperoot@kali:~/Downloads# jefferson npcupg13.01.01.30.bin -d outdir
dumping fs #1 to /root/Downloads/outdir/fs_1
Jffs2_raw_dirent count: 267
Jffs2_raw_inode count: 1362
Jffs2_raw_summary count: 0
Jffs2_raw_xattr count: 0
Jffs2_raw_xref count: 0
Endianness: Little
writing S_ISDIR OnvifFile
writing S_ISREG create_pipe
writing S_ISREG dhcp.script
writing S_ISDIR img
writing S_ISDIR language
writing S_ISREG npc
writing S_ISDIR patch
writing S_ISREG shell_debug
writing S_ISDIR sound
writing S_ISREG upgfile_ok
writing S_ISREG version.txt
writing S_ISREG wpipe
writing S_ISREG OnvifFile/Authentication.xml
writing S_ISREG OnvifFile/CreateProfile.xml
writing S_ISREG OnvifFile/DeleteProfile.xml
writing S_ISREG OnvifFile/Device.xml
writing S_ISREG OnvifFile/Fault.xml
writing S_ISREG OnvifFile/GetAudioEncoderConfiguration.xml
writing S_ISREG OnvifFile/GetAudioEncoderConfigurationOptions.xml
writing S_ISREG OnvifFile/GetCapabilities.xml
writing S_ISREG OnvifFile/GetDeviceInformation.xml
writing S_ISREG OnvifFile/GetNetworkInterfaces.xml
writing S_ISREG OnvifFile/GetProfile.xml
writing S_ISREG OnvifFile/GetProfiles.xml
writing S_ISREG OnvifFile/GetServices.xml
writing S_ISREG OnvifFile/GetSnapshotUri.xml
writing S_ISREG OnvifFile/GetStreamUri.xml
writing S_ISREG OnvifFile/GetSystemDateAndTime.xml
writing S_ISREG OnvifFile/GetVideoEncoderConfiguration.xml
writing S_ISREG OnvifFile/GetVideoEncoderConfigurationOptions.xml
writing S_ISREG OnvifFile/GetVideoEncoderConfigurations.xml
writing S_ISREG OnvifFile/GetVideoSourceConfiguration.xml
writing S_ISREG OnvifFile/GetVideoSourceConfigurations.xml
writing S_ISREG OnvifFile/GetVideoSources.xml
writing S_ISREG OnvifFile/NetworkVideo.xml
writing S_ISREG OnvifFile/OnvifSetTimeTempFile.xml
writing S_ISREG OnvifFile/SetSystemDateAndTime.xml
writing S_ISREG OnvifFile/SetTimeTempFile.xml
writing S_ISREG OnvifFile/SetVideoEncoderConfiguration.xml
writing S_ISREG OnvifFile/tptz_ContinuousMove.xml
writing S_ISREG OnvifFile/tptz_GetConfigurationOptions.xml
writing S_ISDIR img/s
writing S_ISDIR img/ss
writing S_ISDIR img/s/abc
writing S_ISDIR img/s/num
writing S_ISDIR img/s/pun
writing S_ISDIR img/s/upper
writing S_ISREG img/s/abc/a.png
writing S_ISREG img/s/abc/b.png
writing S_ISREG img/s/abc/c.png
writing S_ISREG img/s/abc/d.png
writing S_ISREG img/s/abc/e.png
writing S_ISREG img/s/abc/f.png
writing S_ISREG img/s/abc/g.png
writing S_ISREG img/s/abc/h.png
writing S_ISREG img/s/abc/i.png
writing S_ISREG img/s/abc/j.png
writing S_ISREG img/s/abc/k.png
writing S_ISREG img/s/abc/l.png
writing S_ISREG img/s/abc/m.png
writing S_ISREG img/s/abc/n.png
writing S_ISREG img/s/abc/o.png
writing S_ISREG img/s/abc/p.png
writing S_ISREG img/s/abc/q.png
writing S_ISREG img/s/abc/r.png
writing S_ISREG img/s/abc/s.png
writing S_ISREG img/s/abc/t.png
writing S_ISREG img/s/abc/u.png
writing S_ISREG img/s/abc/v.png
writing S_ISREG img/s/abc/w.png
writing S_ISREG img/s/abc/x.png
writing S_ISREG img/s/abc/y.png
writing S_ISREG img/s/abc/z.png
writing S_ISREG img/s/num/0.png
writing S_ISREG img/s/num/1.png
writing S_ISREG img/s/num/2.png
writing S_ISREG img/s/num/3.png
writing S_ISREG img/s/num/4.png
writing S_ISREG img/s/num/5.png
writing S_ISREG img/s/num/6.png
writing S_ISREG img/s/num/7.png
writing S_ISREG img/s/num/8.png
writing S_ISREG img/s/num/9.png
writing S_ISREG img/s/pun/#.png
writing S_ISREG img/s/pun/,.png
writing S_ISREG img/s/pun/-.png
writing S_ISREG img/s/pun/@.png
writing S_ISREG img/s/pun/_.png
writing S_ISREG img/s/pun/dp.png
writing S_ISREG img/s/pun/point.png
writing S_ISREG img/s/pun/space.png
writing S_ISREG img/s/pun/star.png
writing S_ISREG img/s/pun/xline.png
writing S_ISREG img/s/upper/a.png
writing S_ISREG img/s/upper/b.png
writing S_ISREG img/s/upper/c.png
writing S_ISREG img/s/upper/d.png
writing S_ISREG img/s/upper/e.png
writing S_ISREG img/s/upper/f.png
writing S_ISREG img/s/upper/g.png
writing S_ISREG img/s/upper/h.png
writing S_ISREG img/s/upper/i.png
writing S_ISREG img/s/upper/j.png
writing S_ISREG img/s/upper/k.png
writing S_ISREG img/s/upper/l.png
writing S_ISREG img/s/upper/m.png
writing S_ISREG img/s/upper/n.png
writing S_ISREG img/s/upper/o.png
writing S_ISREG img/s/upper/p.png
writing S_ISREG img/s/upper/q.png
writing S_ISREG img/s/upper/r.png
writing S_ISREG img/s/upper/s.png
writing S_ISREG img/s/upper/t.png
writing S_ISREG img/s/upper/u.png
writing S_ISREG img/s/upper/v.png
writing S_ISREG img/s/upper/w.png
writing S_ISREG img/s/upper/x.png
writing S_ISREG img/s/upper/y.png
writing S_ISREG img/s/upper/z.png
writing S_ISDIR img/ss/num
writing S_ISDIR img/ss/numFL
writing S_ISDIR img/ss/numHD
writing S_ISREG img/ss/num/0.png
writing S_ISREG img/ss/num/1.png
writing S_ISREG img/ss/num/10.png
writing S_ISREG img/ss/num/11.png
writing S_ISREG img/ss/num/12.png
writing S_ISREG img/ss/num/13.png
writing S_ISREG img/ss/num/14.png
writing S_ISREG img/ss/num/15.png
writing S_ISREG img/ss/num/16.png
writing S_ISREG img/ss/num/17.png
writing S_ISREG img/ss/num/18.png
writing S_ISREG img/ss/num/19.png
writing S_ISREG img/ss/num/2.png
writing S_ISREG img/ss/num/20.png
writing S_ISREG img/ss/num/21.png
writing S_ISREG img/ss/num/22.png
writing S_ISREG img/ss/num/23.png
writing S_ISREG img/ss/num/3.png
writing S_ISREG img/ss/num/4.png
writing S_ISREG img/ss/num/5.png
writing S_ISREG img/ss/num/6.png
writing S_ISREG img/ss/num/7.png
writing S_ISREG img/ss/num/8.png
writing S_ISREG img/ss/num/9.png
writing S_ISREG img/ss/numFL/0.png
writing S_ISREG img/ss/numFL/1.png
writing S_ISREG img/ss/numFL/10.png
writing S_ISREG img/ss/numFL/11.png
writing S_ISREG img/ss/numFL/12.png
writing S_ISREG img/ss/numFL/13.png
writing S_ISREG img/ss/numFL/14.png
writing S_ISREG img/ss/numFL/15.png
writing S_ISREG img/ss/numFL/16.png
writing S_ISREG img/ss/numFL/17.png
writing S_ISREG img/ss/numFL/18.png
writing S_ISREG img/ss/numFL/19.png
writing S_ISREG img/ss/numFL/2.png
writing S_ISREG img/ss/numFL/20.png
writing S_ISREG img/ss/numFL/21.png
writing S_ISREG img/ss/numFL/22.png
writing S_ISREG img/ss/numFL/23.png
writing S_ISREG img/ss/numFL/3.png
writing S_ISREG img/ss/numFL/4.png
writing S_ISREG img/ss/numFL/5.png
writing S_ISREG img/ss/numFL/6.png
writing S_ISREG img/ss/numFL/7.png
writing S_ISREG img/ss/numFL/8.png
writing S_ISREG img/ss/numFL/9.png
writing S_ISREG img/ss/numHD/0.png
writing S_ISREG img/ss/numHD/1.png
writing S_ISREG img/ss/numHD/10.png
writing S_ISREG img/ss/numHD/11.png
writing S_ISREG img/ss/numHD/12.png
writing S_ISREG img/ss/numHD/13.png
writing S_ISREG img/ss/numHD/14.png
writing S_ISREG img/ss/numHD/15.png
writing S_ISREG img/ss/numHD/16.png
writing S_ISREG img/ss/numHD/17.png
writing S_ISREG img/ss/numHD/18.png
writing S_ISREG img/ss/numHD/19.png
writing S_ISREG img/ss/numHD/2.png
writing S_ISREG img/ss/numHD/20.png
writing S_ISREG img/ss/numHD/21.png
writing S_ISREG img/ss/numHD/22.png
writing S_ISREG img/ss/numHD/23.png
writing S_ISREG img/ss/numHD/3.png
writing S_ISREG img/ss/numHD/4.png
writing S_ISREG img/ss/numHD/5.png
writing S_ISREG img/ss/numHD/6.png
writing S_ISREG img/ss/numHD/7.png
writing S_ISREG img/ss/numHD/8.png
writing S_ISREG img/ss/numHD/9.png
writing S_ISDIR language/cf
writing S_ISDIR language/ch
writing S_ISDIR language/en
writing S_ISREG language/cf/PushMesg.txt
writing S_ISREG language/ch/PushMesg.txt
writing S_ISREG language/en/PushMesg.txt
writing S_ISREG patch/adc.ko
writing S_ISREG patch/gpioi2c.ko
writing S_ISREG patch/gpioi2c1.ko
writing S_ISREG patch/gpioi2c1_U2.ko
writing S_ISREG patch/hi3518_isp.ko
writing S_ISREG patch/key.ko
writing S_ISREG patch/motor.ko
writing S_ISREG patch/rtc.ko
writing S_ISREG patch/uart1.ko
writing S_ISREG patch/wdt.ko
writing S_ISREG sound/DoorBell.amr
writing S_ISREG sound/Reset_ch.amr
writing S_ISREG sound/Reset_en.amr
writing S_ISREG sound/Unlock.amr
writing S_ISDIR sound/VoiceControl
writing S_ISDIR sound/WifiLink_ch
writing S_ISDIR sound/WifiLink_en
writing S_ISREG sound/alarm.amr
writing S_ISREG sound/beingcalled.amr
writing S_ISREG sound/calling.amr
writing S_ISDIR sound/ch
writing S_ISREG sound/clear.amr
writing S_ISREG sound/di.amr
writing S_ISREG sound/di.pcm
writing S_ISDIR sound/en
writing S_ISREG sound/key_press.amr
writing S_ISDIR sound/numbers_ch
writing S_ISREG sound/set.amr
writing S_ISREG sound/set_fail.amr
writing S_ISREG sound/set_ok.amr
writing S_ISREG sound/test_passed.amr
writing S_ISREG sound/waiting.amr
writing S_ISREG sound/VoiceControl/BonVoyage.amr
writing S_ISREG sound/VoiceControl/Clickly.amr
writing S_ISREG sound/VoiceControl/Goodnight.amr
writing S_ISREG sound/VoiceControl/HelloMaster.amr
writing S_ISREG sound/VoiceControl/NeedTFCard.amr
writing S_ISREG sound/VoiceControl/Recording.amr
writing S_ISREG sound/VoiceControl/Sleep.amr
writing S_ISREG sound/VoiceControl/Welcome.amr
writing S_ISREG sound/VoiceControl/ok_ding.amr
writing S_ISREG sound/WifiLink_ch/ConnFailRetryLater_ch.amr
writing S_ISREG sound/WifiLink_ch/ConnFail_ch.amr
writing S_ISREG sound/WifiLink_ch/DevOnline_ch.amr
writing S_ISREG sound/WifiLink_ch/Linking_ch.amr
writing S_ISREG sound/WifiLink_ch/SuggestApConn_ch.amr
writing S_ISREG sound/WifiLink_ch/SuggestSmartlink_ch.amr
writing S_ISREG sound/WifiLink_ch/WaitLink_ch.amr
writing S_ISREG sound/WifiLink_en/ConnFailRetryLater_en.amr
writing S_ISREG sound/WifiLink_en/ConnFail_en.amr
writing S_ISREG sound/WifiLink_en/DevOnline_en.amr
writing S_ISREG sound/WifiLink_en/Linking_en.amr
writing S_ISREG sound/WifiLink_en/SuggestApConn_en.amr
writing S_ISREG sound/WifiLink_en/SuggestSmartlink_en.amr
writing S_ISREG sound/WifiLink_en/WaitLink_en.amr
writing S_ISREG sound/ch/upgrade_ch.amr
writing S_ISREG sound/en/upgrade_en.amr
writing S_ISREG sound/numbers_ch/0.amr
writing S_ISREG sound/numbers_ch/1.amr
writing S_ISREG sound/numbers_ch/2.amr
writing S_ISREG sound/numbers_ch/3.amr
writing S_ISREG sound/numbers_ch/4.amr
writing S_ISREG sound/numbers_ch/5.amr
writing S_ISREG sound/numbers_ch/6.amr
writing S_ISREG sound/numbers_ch/7.amr
writing S_ISREG sound/numbers_ch/8.amr
writing S_ISREG sound/numbers_ch/9.amr
----------root@kali:~/Downloads/outdir/fs_1# ls
create_pipe dhcp.script img language npc OnvifFile patch shell_debug sound upgfile_ok version.txt wpipeIt looks like the main app is built to handle different image sensors, so the frame rate will depend on what's installed.I dont see anywhere in there the settings for 1080p frame rate.
alastair@PC-I5 ~/cctv/other/Yoosee $ grep "sensor " strings_npc.txt | grep fps
SC1135 960p 30fps sensor init OK!
===111 sc1145 sensor 720P30fps(Parallel port) init success!=====
===sc2135 sensor 1080P25fps(Parallel port) init success311111111!=====
===sc2135 sensor 1080P6fps(Parallel port) init success321=====
===sc2135 sensor 960P25fps(Parallel port) init success321=====
===sc2135 sensor 720P30fps(Parallel port) init success321=====
===sc2135 sensor 1080P16fps(Parallel port) init success321=====
===sc2135 sensor 1080P30fps(Parallel port) init success321=====
`SC3035 sensor 1536x1536 12.5fps init start!
SC3035 sensor 2048x1536 12.5fps init success!
SC3035 sensor 2048x1536 30fps init success! 7410852093
===soi_f23 sensor DVP 1080P30fps linear mode init success!=====
alastair@PC-I5 ~/cctv/other/Yoosee $[%s, %d]:something is moving, frame rate is normal
[%s, %d]:nothing is moving, frame rate is down
VENC_autoDownFrameRate
vNightModeDownFrameRate




nothing is moving, frame rate is down.