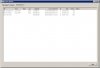
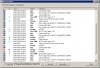
I run my BI on a Proliant server at home, and periodically check the status page for port scanning. As with most people, I get IP addresses occasionally appearing.
Recently, I have noticed the same IP appearing over the last few weeks, perhaps a couple of times a week. There has been no access to my server.
However, when I checked last night, this IP had 12 connections and some 200 frames viewed in one night!
I only have 1 admin account and 1 user account set up, both with strong passwords. The connection does not show a user on the status page.
I am now paranoid that they can access the web viewer, view old clips, alter setting etc., as I do not know what privilages they logged on with.
I am nowhere near an expert on networking, so how can this happen?
I have disabled the web server until I can find out what happened, and use RDC to view at the moment. Any help/advice gratefully received.
Thanks.
Recently, I have noticed the same IP appearing over the last few weeks, perhaps a couple of times a week. There has been no access to my server.
However, when I checked last night, this IP had 12 connections and some 200 frames viewed in one night!
I only have 1 admin account and 1 user account set up, both with strong passwords. The connection does not show a user on the status page.
I am now paranoid that they can access the web viewer, view old clips, alter setting etc., as I do not know what privilages they logged on with.
I am nowhere near an expert on networking, so how can this happen?
I have disabled the web server until I can find out what happened, and use RDC to view at the moment. Any help/advice gratefully received.
Thanks.