pc1
n3wb
- Joined
- May 7, 2018
- Messages
- 15
- Reaction score
- 5
I recently bought this camera from Amazon, new condition and sold by "EmpireTech-Andy".
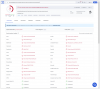
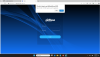
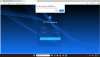
I setup the camera in an isolated environment, and during setup the camera prompts you to download (from the cameras embedded firmware) the webplugin.exe file to enable viewing imaging in a browser. After download, I ran webplugin.exe through Virustotal.com, and it lit up with malware warnings from 28 different analyses.
The virustotal identifier is 469705fb3df80c89c67927f4d07e0b3a22ce19811272e86789c18e26e35a8add , here's the report: VirusTotal
I setup the camera in an isolated environment, and during setup the camera prompts you to download (from the cameras embedded firmware) the webplugin.exe file to enable viewing imaging in a browser. After download, I ran webplugin.exe through Virustotal.com, and it lit up with malware warnings from 28 different analyses.
The virustotal identifier is 469705fb3df80c89c67927f4d07e0b3a22ce19811272e86789c18e26e35a8add , here's the report: VirusTotal
Attachments
-
164.3 KB Views: 74