I have a camera at a remote location that is being attacked. This is an ICSEE type cheap Chinese camera. I have an open port on the router and since it is remote I can't easily change the port number. I did change the password on the camera but that had no effect on the attacker. I don't really mind someone viewing the camera but the problem is that whatever this bot is trying to do causes the camera to reboot every few minutes. The camera worked fine up until a few weeks ago when it started doing all the rebooting. When I looked at the camera's log I noticed the repeating attack. A screenshot of the log with one cycle of the attack is below.
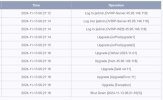
The IP address 45.95.146.118 is from the Netherlands. This changes frequently but is mostly Netherlands and Russia. I would like to know what password they are using to log in! It appears the bot is trying to upgrade the firmware which fails and causes the camera to restart. It is a PITA and since I don't have access to the router right now there isn't much I can do. Has anyone ever encountered something like this?

The IP address 45.95.146.118 is from the Netherlands. This changes frequently but is mostly Netherlands and Russia. I would like to know what password they are using to log in! It appears the bot is trying to upgrade the firmware which fails and causes the camera to restart. It is a PITA and since I don't have access to the router right now there isn't much I can do. Has anyone ever encountered something like this?

