- Feb 17, 2018
- 25
- 11
I have 3 IPC-HDW5231R-Z cameras and 1 newer IPC-HDW5231R-ZE.
All working well, and all on their own VLAN after reading a lot about security on this forum. This morning I was playing with my router and decided to use the services of papertrailapp.com to send my router logs to them for easier browsing etc.
It only took a few minutes before I saw this:
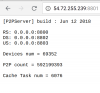
Every few seconds, my IPC-HDW5231R-ZE camera (192.168.20.14) keeps trying to contact 54.69.152.187.
Having looked it up, it appears to be an Amazon IP address.
I've had a look at all the services on the camera and nothing else appears to be enabled, so I don't know why or what it is trying to connect to.
And just to be clear, the older IPC-HDW5231R-Z cameras do NOT do this.
Does anyone have any idea?
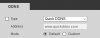
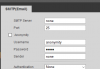
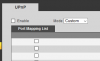
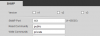

All working well, and all on their own VLAN after reading a lot about security on this forum. This morning I was playing with my router and decided to use the services of papertrailapp.com to send my router logs to them for easier browsing etc.
It only took a few minutes before I saw this:
Code:
Jul 26 14:29:34 ubnt kernel: [VLAN20_IN-default-D]IN=eth1.20 OUT=eth0 MAC=<snip> SRC=192.168.20.14 DST=54.69.152.187 LEN=60 TOS=0x00 PREC=0x00 TTL=63 ID=53177 DF PROTO=TCP SPT=52536 DPT=2195 WINDOW=14600 RES=0x00 SYN URGP=0
Jul 26 14:29:36 ubnt kernel: [VLAN20_IN-default-D]IN=eth1.20 OUT=eth0 MAC=<snip> SRC=192.168.20.14 DST=54.69.152.187 LEN=60 TOS=0x00 PREC=0x00 TTL=63 ID=46932 DF PROTO=TCP SPT=52538 DPT=2195 WINDOW=14600 RES=0x00 SYN URGP=0
Jul 26 14:29:37 ubnt kernel: [VLAN20_IN-default-D]IN=eth1.20 OUT=eth0 MAC=<snip> SRC=192.168.20.14 DST=54.69.152.187 LEN=60 TOS=0x00 PREC=0x00 TTL=63 ID=46933 DF PROTO=TCP SPT=52538 DPT=2195 WINDOW=14600 RES=0x00 SYN URGP=0Every few seconds, my IPC-HDW5231R-ZE camera (192.168.20.14) keeps trying to contact 54.69.152.187.
Having looked it up, it appears to be an Amazon IP address.
I've had a look at all the services on the camera and nothing else appears to be enabled, so I don't know why or what it is trying to connect to.
And just to be clear, the older IPC-HDW5231R-Z cameras do NOT do this.
Does anyone have any idea?