I am wanting to move away from my SmartThings mesh hubs for Wi-Fi and automation. The hubs are no longer available and I am wanting to increase my wireless coverage. They have also become a little less reliable for my automations since ST no longer supports WebCore.
This is my current network scheme:
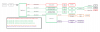
One nice feature of the ST hubs was with one SSID I could assign different passwords for varying levels of access. If you entered PW1 when attempting to log on to My_Wifi it would give you full access, PW2 would treat you as a guest, and if you entered PW3 it would allow only internet access. Presently all of my IOT devices are on the main network, whether it be wired or wireless, with a few recently migrated to PW3 for only internet access. I also just started working from home and wanted my work PC to be segregated. I followed the steps in the video below to put rulesets in place to give the .10.XX subnet access to only the internet and nothing else on the network.
Going forward, and my question:
I am looking to go with Ubiquiti Unifi 6 Lite APs (no other Ubiquiti/Unifi equipment other than the ER-X) . During this change over process I am also wanting to segregate my IOT devices to internet only. For wired devices I plan to replace the desktop switch with a larger rack mount switch and patch the devices over to the .10.XX subnet. For the wireless devices, I am not sure how to accomplish what I am thinking. Ideally I would like to create an IOT SSID and point it to .10.XX and be done, but how possible is this with what I have already created/setup in the ER-X (from the video)? The APs would be on the Eth-2 and Eth-3 ports.
This is my current network scheme:
One nice feature of the ST hubs was with one SSID I could assign different passwords for varying levels of access. If you entered PW1 when attempting to log on to My_Wifi it would give you full access, PW2 would treat you as a guest, and if you entered PW3 it would allow only internet access. Presently all of my IOT devices are on the main network, whether it be wired or wireless, with a few recently migrated to PW3 for only internet access. I also just started working from home and wanted my work PC to be segregated. I followed the steps in the video below to put rulesets in place to give the .10.XX subnet access to only the internet and nothing else on the network.
Going forward, and my question:
I am looking to go with Ubiquiti Unifi 6 Lite APs (no other Ubiquiti/Unifi equipment other than the ER-X) . During this change over process I am also wanting to segregate my IOT devices to internet only. For wired devices I plan to replace the desktop switch with a larger rack mount switch and patch the devices over to the .10.XX subnet. For the wireless devices, I am not sure how to accomplish what I am thinking. Ideally I would like to create an IOT SSID and point it to .10.XX and be done, but how possible is this with what I have already created/setup in the ER-X (from the video)? The APs would be on the Eth-2 and Eth-3 ports.
Attachments
Last edited:
