I have installed an additional gigabit NIC, but I have not set it up yet. It's working with the defaults at present.
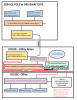
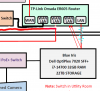
I am trying to wrap my head around the proper way to run the cameras thru the network. Below is my current network diagram.
There are TWO cameras coming in thru the fiber that is run to the service pole at the gate. Will be adding a third PTZ camera soon. I plan on replacing the TP-Link SS108GP switch at the service pole with a managed switch simply to have control over the switch.
There will be several more cameras with Ethernet cables already running from their location to the office/room where the Blue Iris computer is located. I have dual NIC in this computer and two Ethernet cables ran from the utility room.
Looking for advice on how to set it up and run it all. Do I need to run any new wires, add any other switches or is it all done with software?
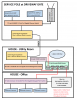
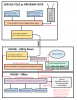
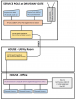
I am trying to wrap my head around the proper way to run the cameras thru the network. Below is my current network diagram.
There are TWO cameras coming in thru the fiber that is run to the service pole at the gate. Will be adding a third PTZ camera soon. I plan on replacing the TP-Link SS108GP switch at the service pole with a managed switch simply to have control over the switch.
There will be several more cameras with Ethernet cables already running from their location to the office/room where the Blue Iris computer is located. I have dual NIC in this computer and two Ethernet cables ran from the utility room.
Looking for advice on how to set it up and run it all. Do I need to run any new wires, add any other switches or is it all done with software?