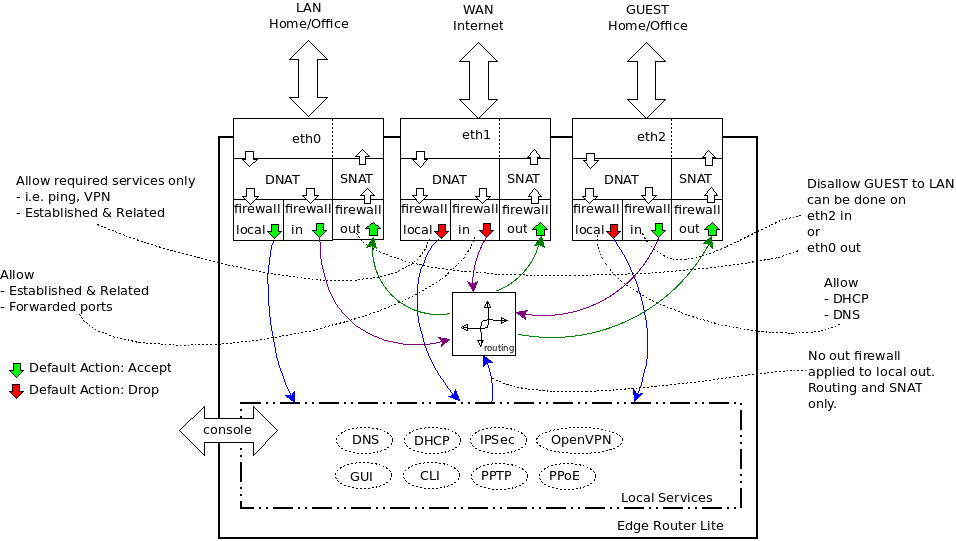
Spent this entire Saturday learning about creating subnets & VLANs through my Ubiquiti UDM router and Ubiquiti 48 port managed switch and Ubiquiti AP. Had to watch lots of YouTube vids (mostly of EdgeRouters since not much UDM vids out there yet) and websites.
Finally. So far, I have 4 subnets & VLANS:
1.) 192.168.1.1 for personal use
2.) 192.168.2.1 for future Radius VPN (gotta wait til my Pixel 4XL arrives for that)
3.) 192.168.3.1 VLAN 3 for general IOT (Denon smart amp, robot vacuum, Roku's, etc)
4.) 192.168.4.1 VLAN 4 for 15 IP cameras & Blue Iris Server
Gots all IP's of cameras blocked via firewall WAN OUT (before, I only had MAC address's blocked which I learned was not wise in itself).
Had to setup additional firewall rules to allow UI3 to connect from 192.168.4.1 to my personal 192.168.1.1 network.
Somehow (by luck) Remote Desktop Protocol now works too. Something I didn't know. If a user is logged in and and running Blue Iris program itself (not the service), any other user that logs in with a new desktop for that new user is unable to open the Blue Iris program since the program is still running on other user. So I guess I will make good practice to use Blue Iris and shut it down before leaving (still will run as a service).
Tested everything out. All 3 Roku's (2 hardwired, 1 wifi) work 100%. Blue Iris server sees all IP cam's and still gets to the internet (will research more about this if good or bad). And very happy to report... my Ecovacs DEEBOT 711 is fully functional for the first time! Is it ok to say that I bought all these IP cameras just to watch my robo-vacuum work?
Finally. So far, I have 4 subnets & VLANS:
1.) 192.168.1.1 for personal use
2.) 192.168.2.1 for future Radius VPN (gotta wait til my Pixel 4XL arrives for that)
3.) 192.168.3.1 VLAN 3 for general IOT (Denon smart amp, robot vacuum, Roku's, etc)
4.) 192.168.4.1 VLAN 4 for 15 IP cameras & Blue Iris Server
Gots all IP's of cameras blocked via firewall WAN OUT (before, I only had MAC address's blocked which I learned was not wise in itself).
Had to setup additional firewall rules to allow UI3 to connect from 192.168.4.1 to my personal 192.168.1.1 network.
Somehow (by luck) Remote Desktop Protocol now works too. Something I didn't know. If a user is logged in and and running Blue Iris program itself (not the service), any other user that logs in with a new desktop for that new user is unable to open the Blue Iris program since the program is still running on other user. So I guess I will make good practice to use Blue Iris and shut it down before leaving (still will run as a service).
Tested everything out. All 3 Roku's (2 hardwired, 1 wifi) work 100%. Blue Iris server sees all IP cam's and still gets to the internet (will research more about this if good or bad). And very happy to report... my Ecovacs DEEBOT 711 is fully functional for the first time! Is it ok to say that I bought all these IP cameras just to watch my robo-vacuum work?