- Aug 11, 2017
- 17
- 0
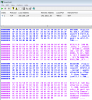
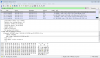
I'm writing some code to set up cameras via RTSC. Both of the cameras I have are pretty crappy software wise: Reolink and SV3C. I can get VLC to log the access to both of the cameras OK and I duplicate the OPTIONS transaction exactly as VLC does it. With my code, the SV3C works, the Reolink just hangs after receiving the following:
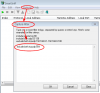
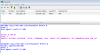
OPTIONS rtsp://192.168.1.147:554/h264Preview_01_main RTSP/1.0
CSeq: 1
I have compared this to the VLC log eleventy-seven times. It's exact. No different with/without the User-Agent: <blah> line. The CSeq value doesn't seem to matter.
Are there variations on opening sockets? The VLC log doesn't show any of that.
I don't think the Reolink is disconnecting after receiving a command (why would it?) or the recv call would .
.
Any thoughts?
OPTIONS rtsp://192.168.1.147:554/h264Preview_01_main RTSP/1.0
CSeq: 1
I have compared this to the VLC log eleventy-seven times. It's exact. No different with/without the User-Agent: <blah> line. The CSeq value doesn't seem to matter.
Are there variations on opening sockets? The VLC log doesn't show any of that.
I don't think the Reolink is disconnecting after receiving a command (why would it?) or the recv call would
 .
.Any thoughts?