Hello,
Recently got myself a Dahua / IMOU camera, and since I got so much fine information from here I figured i'd give some back.
model: IPC-G42P-IMOU
fw : Eng_P_V2.680.0000000.24.R.20210309
So here's how you can get into a busybox shell on these.
# Step 1
Attach to serial hardware, thanks to the FCC for providing these photos. You open the camera by popping off the front black bezel around the lense.

# Step 2
Smash '*' during boot to get to u-boot console
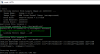
# Step 3 run these commands (to enable single user mode)
# Step 4 (might be a smarter way to do this)
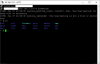
Smash the HWID environment variable
Note, this is just something i stumbled on, not sure what you actually need to put on the end for it to crash.
NOTE : There's a space after the last chars \&\"
Boot procedure uses the HWID to lookup bootargs, if HWID isnt found it will default to using u-boot bootargs.
The default bootargs can be found in partition-x.cramfs\bootargsParameters.txt
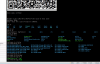
You will be dropped into a nice signed securebooted busybox shell. (I cant get it to run any unsigned binaries)
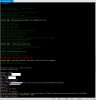
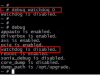
To stop the watchdog from resetting the device you can go through the boot process with these commands:
Running Sonia with parameters seems to allow it to boot properly
Once Sonia has booted, you can exit it with Ctrl+C
And thats it, root, and you wont get reset automaticly.
Notes :
dd has been removed from busybox
Mount SDCard:
Mount NFS share:
Read all U-boot environment variables:
Now from here, I can't really see any options to get further. Bootloader and Kernel seem impenetrable.
Recently got myself a Dahua / IMOU camera, and since I got so much fine information from here I figured i'd give some back.
model: IPC-G42P-IMOU
fw : Eng_P_V2.680.0000000.24.R.20210309
So here's how you can get into a busybox shell on these.
# Step 1
Attach to serial hardware, thanks to the FCC for providing these photos. You open the camera by popping off the front black bezel around the lense.

# Step 2
Smash '*' during boot to get to u-boot console
# Step 3 run these commands (to enable single user mode)
Code:
printenv (you should save this output in a safe place)
setenv appauto 0
setenv dh_keyboard 0
setenv bootargs mem=256M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=106M single
saveenv# Step 4 (might be a smarter way to do this)
Smash the HWID environment variable
Note, this is just something i stumbled on, not sure what you actually need to put on the end for it to crash.
NOTE : There's a space after the last chars \&\"
Code:
setenv HWID IPC-G42P-IMOU:01:02:03:73:30:00:01:10:01:00:04:320:00:02:00:00:00:00:00:00:100\"\& ls \&\"
bootBoot procedure uses the HWID to lookup bootargs, if HWID isnt found it will default to using u-boot bootargs.
The default bootargs can be found in partition-x.cramfs\bootargsParameters.txt
Code:
#每行参数以\结束 每行以回车结束
#bootargs参数放在""中
#hwid bootargs参数
IPC-TF26-S2:01:02:0F:60:2B:00:01:10:01:00:04:320:00:02:00:00:00:00:00:00:80\ "mem=128M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=50M"
IPC-TD26-S2:01:02:0F:60:2B:00:01:10:01:00:04:320:00:02:00:00:00:00:00:00:80\ "mem=128M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=50M"
IPC-TG26E:01:02:02:60:2B:00:01:10:01:01:04:320:00:02:00:00:00:00:00:00:80\ "mem=128M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=50M"
IPC-D1B20P-W:01:02:05:7F:2B:00:01:00:00:00:04:320:00:02:00:00:00:00:00:00:80\ "mem=128M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=50M"
IPC-B1B20P-W:01:02:03:7F:2B:00:01:10:01:00:04:320:00:02:00:00:00:00:00:00:80\ "mem=128M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=50M"
IPC-TG26C:01:02:03:7F:2B:00:01:10:01:00:04:320:00:02:00:00:00:00:00:00:80\ "mem=128M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=50M"
IPC-D1B40P-W:01:02:05:73:30:00:01:00:00:00:04:320:00:02:00:00:00:00:00:00:100\ "mem=256M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=106M"
IPC-B1B40P-W:01:02:03:73:30:00:01:10:01:00:04:320:00:02:00:00:00:00:00:00:100\ "mem=256M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=106M"
IPC-TG46C:01:02:03:73:30:00:01:10:01:00:04:320:00:02:00:00:00:00:00:00:100\ "mem=256M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=106M"
IPC-G22N-IMOU:01:02:03:7F:2B:00:01:10:01:00:04:320:00:02:00:00:00:00:00:00:80\ "mem=128M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=50M"
IPC-D22P-IMOU:01:02:05:7F:2B:00:01:00:00:00:04:320:00:02:00:00:00:00:00:00:80\ "mem=128M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=50M"
IPC-G42P-IMOU:01:02:03:73:30:00:01:10:01:00:04:320:00:02:00:00:00:00:00:00:100\ "mem=256M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=106M"
IPC-D42P-IMOU:01:02:05:73:30:00:01:00:00:00:04:320:00:02:00:00:00:00:00:00:100\ "mem=256M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=106M"
IPC-G22MP-0280B:01:02:03:7F:2B:00:01:10:00:00:04:320:00:02:00:00:00:00:00:00:80\ "mem=128M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=50M"
IPC-G42MP-0280B:01:02:03:73:30:00:01:10:00:00:04:320:00:02:00:00:00:00:00:00:100\ "mem=256M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=106M"
IPC-G26E:01:02:02:60:2B:00:01:10:01:01:04:320:00:02:00:00:00:00:00:00:80\ "mem=128M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=50M"
IPC-HFW1235S-W:01:02:01:7F:2B:00:01:10:01:00:04:320:00:02:00:00:00:00:00:00:80\ "mem=128M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=50M"
IPC-HDBW1235E-W-S2:01:02:05:60:2B:00:01:00:00:00:04:320:00:02:00:00:00:00:00:00:80\ "mem=128M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=50M"
IPC-HDBW1435E-W-S2:01:02:05:73:30:00:01:00:00:00:04:320:00:02:00:00:00:00:00:00:100\ "mem=256M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=106M"
IPC-HFW1235S-W-S2:01:02:03:60:2B:00:01:10:00:00:04:320:00:02:00:00:00:00:00:00:80\ "mem=128M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=50M"
IPC-HFW1435S-W-S2:01:02:03:73:30:00:01:10:00:00:04:320:00:02:00:00:00:00:00:00:100\ "mem=256M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs cma=106M"You will be dropped into a nice signed securebooted busybox shell. (I cant get it to run any unsigned binaries)
To stop the watchdog from resetting the device you can go through the boot process with these commands:
Code:
/bin/mount -t proc /proc /proc
/etc/init.d/dnode
/etc/init.d/rcS
/usr/bin/sonia --helpRunning Sonia with parameters seems to allow it to boot properly
Once Sonia has booted, you can exit it with Ctrl+C
And thats it, root, and you wont get reset automaticly.
Code:
BusyBox v1.18.4 (2021-01-30 16:34:43 CST) multi-call binary.
Copyright (C) 1998-2009 Erik Andersen, Rob Landley, Denys Vlasenko
and others. Licensed under GPLv2.
See source distribution for full notice.
Usage: busybox [function] [arguments]...
or: busybox --list[-full]
or: function [arguments]...
BusyBox is a multi-call binary that combines many common Unix
utilities into a single executable. Most people will create a
link to busybox for each function they wish to use and BusyBox
will act like whatever it was invoked as.
Currently defined functions:
[, [[, arp, arping, ash, awk, bash, brctl, cat, chgrp, chmod, chown,
chroot, cp, cut, date, df, dhcprelay, dmesg, du, dumpleases, echo,
egrep, eject, env, fdisk, fgrep, find, flash_eraseall, free, fsync,
getty, grep, halt, head, ifconfig, ifenslave, inetd, init, insmod, ip,
ipaddr, iplink, iproute, iprule, iptunnel, kill, killall, killall5,
less, linuxrc, ln, login, ls, lsmod, lspci, lsusb, lzcat, lzma, mdev,
mkdir, mknod, modinfo, more, mount, mv, netstat, nice, ping, ping6,
pkill, poweroff, printenv, ps, pwd, reboot, rm, rmdir, rmmod, route,
sed, seq, sh, sleep, stat, sync, tail, tcpsvd, test, top, touch,
ubiattach, ubidetach, ubimkvol, ubirmvol, ubirsvol, ubiupdatevol,
udhcpd, udpsvd, umount, uname, unlzma, unzip, vi, who, whoami
/bin # help
Built-in commands:
------------------
. : alias bg break cd chdir continue eval exec exit export false
fg hash help jobs kill let local pwd read readonly return set
shift source times trap true type ulimit umask unalias unset
waitNotes :
dd has been removed from busybox
Mount SDCard:
Code:
insmod /usr/lib/modules/fat.ko
insmod /usr/lib/modules/vfat.ko
insmod /usr/lib/modules/sdcard.ko
mount -t vfat -o rw,nodev,noatime,nodiratime,fmask=0020,dmask=0020,allow_utime=0002,codepage=437,iocharset=iso8859-1,shortname=mixed,errors=remount-ro /dev/mmc0p1 /mnt/sdMount NFS share:
# On raspbian or other distro
# Install nfs service
sudo apt-get install nfs-kernel-server
# Configuring nfs
sudo vim /etc/exports
# Create data directory
mkdir /home/pi/rootfs
# Add the following line to export and exit the save
/home/pi/rootfs *(rw,sync,no_root_squash,no_subtree_check)
# Restart nfs service (may need to reboot first)
sudo /etc/init.d/nfs-kernel-server restart
# In camera busybox console
mount -t nfs -o nolock 192.168.1.104:/home/pi/rootfs/ /mnt/tmp
Read all U-boot environment variables:
Code:
# Read all
/usr/sbin/systools armbenv -r
# Write HWID to flash
/usr/sbin/systools armbenv -s HWID IPC-G42P-IMOU:01:02:03:73:30:00:01:10:01:00:04:320:00:02:00:00:00:00:00:00:100Now from here, I can't really see any options to get further. Bootloader and Kernel seem impenetrable.
Last edited: