I believe this email is support and from v380, my cameras are v360 pro, I tried the cashi.ini file and it didn't work either, my intention is to include them in the NVR, I scanned it and found the following ports open, but not I made sure to manually include it in the NVR. Attached is a scan image of the IP camera.have you try the ceshi.ini and contact the email support on this post
Cannot connect Chinese 360 IP cam through ONVIF
- Thread starter a29psx
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
yes, this is the port, when testing VLC using this protocol it asks for username and password, I have already tried everything possible, if anyone has been through this situation please help me.it's ceshi.ini not cashi.ini, make sure you got it right
and I also think port 8554 is your camera RTSP port
rtsp:/10.0.0.133:8554/live/ch0
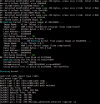
Starting Nmap 7.94 ( Nmap: the Network Mapper - Free Security Scanner ) at 2024-04-04 04:11 Hora Padrão de Caracas
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 04:11
Completed NSE at 04:11, 0.00s elapsed
Initiating NSE at 04:11
Completed NSE at 04:11, 0.00s elapsed
Initiating NSE at 04:11
Completed NSE at 04:11, 0.00s elapsed
Initiating ARP Ping Scan at 04:11
Scanning 10.0.0.162 [1 port]
Completed ARP Ping Scan at 04:11, 0.20s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 04:11
Completed Parallel DNS resolution of 1 host. at 04:11, 0.01s elapsed
Initiating SYN Stealth Scan at 04:11
Scanning 10.0.0.162 [65535 ports]
Discovered open port 23/tcp on 10.0.0.162
Increasing send delay for 10.0.0.162 from 0 to 5 due to 127 out of 317 dropped probes since last increase.
Increasing send delay for 10.0.0.162 from 5 to 10 due to 13 out of 31 dropped probes since last increase.
SYN Stealth Scan Timing: About 2.85% done; ETC: 04:29 (0:17:36 remaining)
SYN Stealth Scan Timing: About 5.89% done; ETC: 04:28 (0:16:15 remaining)
SYN Stealth Scan Timing: About 9.81% done; ETC: 04:28 (0:15:19 remaining)
SYN Stealth Scan Timing: About 13.84% done; ETC: 04:28 (0:14:25 remaining)
SYN Stealth Scan Timing: About 18.43% done; ETC: 04:28 (0:13:34 remaining)
SYN Stealth Scan Timing: About 23.57% done; ETC: 04:28 (0:12:42 remaining)
SYN Stealth Scan Timing: About 28.89% done; ETC: 04:28 (0:11:51 remaining)
SYN Stealth Scan Timing: About 33.83% done; ETC: 04:28 (0:10:59 remaining)
SYN Stealth Scan Timing: About 38.97% done; ETC: 04:28 (0:10:08 remaining)
SYN Stealth Scan Timing: About 44.09% done; ETC: 04:28 (0:09:17 remaining)
SYN Stealth Scan Timing: About 49.25% done; ETC: 04:28 (0:08:25 remaining)
Discovered open port 8699/tcp on 10.0.0.162
SYN Stealth Scan Timing: About 54.21% done; ETC: 04:28 (0:07:34 remaining)
Discovered open port 1300/tcp on 10.0.0.162
SYN Stealth Scan Timing: About 59.38% done; ETC: 04:28 (0:06:43 remaining)
SYN Stealth Scan Timing: About 64.33% done; ETC: 04:27 (0:05:53 remaining)
SYN Stealth Scan Timing: About 69.48% done; ETC: 04:27 (0:05:02 remaining)
SYN Stealth Scan Timing: About 74.72% done; ETC: 04:27 (0:04:10 remaining)
Discovered open port 8554/tcp on 10.0.0.162
SYN Stealth Scan Timing: About 79.90% done; ETC: 04:27 (0:03:19 remaining)
Discovered open port 843/tcp on 10.0.0.162
SYN Stealth Scan Timing: About 85.14% done; ETC: 04:27 (0:02:27 remaining)
SYN Stealth Scan Timing: About 90.33% done; ETC: 04:27 (0:01:36 remaining)
SYN Stealth Scan Timing: About 95.59% done; ETC: 04:27 (0:00:44 remaining)
Completed SYN Stealth Scan at 04:27, 990.81s elapsed (65535 total ports)
Initiating Service scan at 04:27
Scanning 5 services on 10.0.0.162
Service scan Timing: About 40.00% done; ETC: 04:29 (0:00:54 remaining)
Completed Service scan at 04:30, 157.63s elapsed (5 services on 1 host)
Initiating OS detection (try #1) against 10.0.0.162
NSE: Script scanning 10.0.0.162.
Initiating NSE at 04:30
Completed NSE at 04:30, 14.29s elapsed
Initiating NSE at 04:30
Completed NSE at 04:30, 1.06s elapsed
Initiating NSE at 04:30
Completed NSE at 04:30, 0.00s elapsed
Nmap scan report for 10.0.0.162
Host is up (0.020s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
23/tcp open telnet
| fingerprint-strings:
| GenericLines:
| (none) login:
| (none) login: (none) login:
| GetRequest:
| HTTP/1.0
| (none) login:
| Help:
| HELP
| (none) login:
| NCP:
| DmdT^@^@^@
| ^@^@^@^A^@^@^@^@
| NULL:
| (none) login:
| SIPOptions:
| OPTIONS sip:nm SIP/2.0
| Via: SIP/2.0/TCP nm;branch=foo
| From: <sip:nm@nm>;tag=root
| <sip:nm2@nm2>
| Call-ID: 50000
| CSeq: 42 OPTIONS
| Max-Forwards: 70
| Content-Length: 0
| Contact: <sip:nm@nm>
| Accept: application/sdp
| (none) login:
| tn3270:
|_ ^@IBM-3279-4-E(none) login:
843/tcp open unknown
1300/tcp open h323hostcallsc?
8554/tcp open rtsp
| fingerprint-strings:
| SIPOptions:
| RTSP/1.0 200 OK
| Server: YGTek RTSP Server 2.0
| CSeq: 42
| Date: Thu Apr 4 08:29:50 2024
|_ Public: DESCRIBE, SETUP, PLAY, PAUSE, OPTIONS, TEARDOWN,GET_PARAMETER,SET_PARAMETER
|_rtsp-methods: DESCRIBE, SETUP, PLAY, PAUSE, OPTIONS, TEARDOWN,GET_PARAMETER,SET_PARAMETER
8699/tcp open arcserve ARCserve Discovery
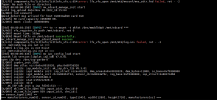
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at Nmap Fingerprint Submitter 2.0 :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port23-TCP:V=7.94%I=7%D=4/4%Time=660E6495%P=i686-pc-windows-windows%r(N
SF:ULL,1A,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03\(none\)\x20log
SF:in:\x20")%r(GenericLines,3A,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\x
SF:fb\x03\(none\)\x20login:\x20\r\n\r\n\(none\)\x20login:\x20\(none\)\x20l
SF
SF:03\^@IBM-3279-4-E\(none\)\x20login:\x20")%r(GetRequest,2C,"\xff\xfd\x01
SF:\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03GET\x20/\x20HTTP/1\.0\r\n\r\n\(none
SF:\)\x20login:\x20")%r(RPCCheck,C,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\x
SF:ff\xfb\x03")%r(Help,20,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x0
SF:3HELP\r\n\(none\)\x20login:\x20")%r(SIPOptions,F9,"\xff\xfd\x01\xff\xfd
SF:\x1f\xff\xfb\x01\xff\xfb\x03OPTIONS\x20sip:nm\x20SIP/2\.0\r\nVia:\x20SI
SF
SF:<sip:nm2@nm2>\r\nCall-ID:\x2050000\r\nCSeq:\x2042\x20OPTIONS\r\nMax-For
SF:wards:\x2070\r\nContent-Length:\x200\r\nContact:\x20<sip:nm@nm>\r\nAcce
SF
SF:fd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03DmdT\^@\^@\^@\x08\x20\x08\x08
SF:\x20\x08\x08\x20\x08\x08\x20\x08\x08\x20\x08\x08\x20\x08\x08\x20\x08\x0
SF:8\x20\x08\x08\x20\x08\x08\x20\x08\^@\^@\^@\^A\^@\^@\^@\^@");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8554-TCP:V=7.94%I=7%D=4/4%Time=660E64F0%P=i686-pc-windows-windows%r
SF
SF:erver\x202\.0\r\nCSeq:\x2042\r\nDate:\x20Thu\x20Apr\x20\x204\x2008:29:5
SF:0\x202024\r\nPublic:\x20DESCRIBE,\x20SETUP,\x20PLAY,\x20PAUSE,\x20OPTIO
SF:NS,\x20TEARDOWN,GET_PARAMETER,SET_PARAMETER\r\n\r\n");
MAC Address: 68:8F:C9:F0:05:B3 (Zhuolian (Shenzhen) Communication)
Device type: phone
Running: Google Android 4.1.X
OS CPE: cpe:/o:google:android:4.1.2
OS details: Android 4.1.2
Uptime guess: 0.011 days (since Thu Apr 4 04:14:38 2024)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=260 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Host: FAIL
TRACEROUTE
HOP RTT ADDRESS
1 20.28 ms 10.0.0.162
NSE: Script Post-scanning.
Initiating NSE at 04:30
Completed NSE at 04:30, 0.00s elapsed
Initiating NSE at 04:30
Completed NSE at 04:30, 0.00s elapsed
Initiating NSE at 04:30
Completed NSE at 04:30, 0.00s elapsed
Read data files from: C:\Program Files (x86)\Nmap
OS and Service detection performed. Please report any incorrect results at Nmap OS/Service Fingerprint and Correction Submission Page .
Nmap done: 1 IP address (1 host up) scanned in 1168.63 seconds
Raw packets sent: 66854 (2.943MB) | Rcvd: 66412 (2.687MB)
Last edited:
Exactly the same model, after studying a lot I ended up discovering the open RTSP number 8554, and I asked for a password when manually adding it to the NVR, I discovered that the username is admin and the password is admin123456, even so it has some blocking that I was unable to connect to the NVR.Looks, that I have same camera and same problem...
Without username and password it is possible to connect the camera only to V360 PRO application.
View attachment 192023
On the camera is only small QR code: CFET-525553-HPMWZ
View attachment 192024
@danzimmer
Thank you
But it looks that they set different password for each camera
admin / admin123456 does not work for me, maybe credentials are correct, but port is missing. I tried to connect with:
Agent DVR
Synology Surveillance Station (NAS)
VLC Media Player -> rtsp:/192.168.0.10:8554/live/ch0 ... it asked for login, but admin / admin123456 does not work :-/ probably, because the port 8554 is not openned
And it looks that I have not openned port 8554. Or you openned it somehow?
Starting Nmap 7.94 ( Nmap: the Network Mapper - Free Security Scanner ) at 2024-04-17 18:40 Střední Evropa (letní čas)
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 18:41
Completed NSE at 18:41, 0.00s elapsed
Initiating NSE at 18:41
Completed NSE at 18:41, 0.00s elapsed
Initiating NSE at 18:41
Completed NSE at 18:41, 0.00s elapsed
Initiating ARP Ping Scan at 18:41
Scanning 192.168.0.10 [1 port]
Completed ARP Ping Scan at 18:41, 0.09s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 18:41
Completed Parallel DNS resolution of 1 host. at 18:41, 0.02s elapsed
Initiating SYN Stealth Scan at 18:41
Scanning 192.168.0.10 [1000 ports]
Discovered open port 23/tcp on 192.168.0.10
Discovered open port 843/tcp on 192.168.0.10
Discovered open port 1300/tcp on 192.168.0.10
Completed SYN Stealth Scan at 18:41, 2.19s elapsed (1000 total ports)
Initiating Service scan at 18:41
Scanning 3 services on 192.168.0.10
Completed Service scan at 18:43, 157.28s elapsed (3 services on 1 host)
Initiating OS detection (try #1) against 192.168.0.10
NSE: Script scanning 192.168.0.10.
Initiating NSE at 18:43
Completed NSE at 18:43, 14.14s elapsed
Initiating NSE at 18:43
Completed NSE at 18:43, 1.03s elapsed
Initiating NSE at 18:43
Completed NSE at 18:43, 0.00s elapsed
Nmap scan report for 192.168.0.10
Host is up (0.044s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
23/tcp open telnet
| fingerprint-strings:
| GenericLines:
| (none) login:
| (none) login: (none) login:
| GetRequest:
| HTTP/1.0
| (none) login:
| Help:
| HELP
| (none) login:
| NCP:
| DmdT^@^@^@
| ^@^@^@^A^@^@^@^@
| NULL:
| (none) login:
| SIPOptions:
| OPTIONS sip:nm SIP/2.0
| Via: SIP/2.0/TCP nm;branch=foo
| From: <sip:nm@nm>;tag=root
| <sip:nm2@nm2>
| Call-ID: 50000
| CSeq: 42 OPTIONS
| Max-Forwards: 70
| Content-Length: 0
| Contact: <sip:nm@nm>
| Accept: application/sdp
| (none) login:
| tn3270:
|_ (none) login: ^@IBM-3279-4-E
843/tcp open unknown
1300/tcp open h323hostcallsc?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at Nmap Fingerprint Submitter 2.0 :
SF-Port23-TCP:V=7.94%I=7%D=4/17%Time=661FFBA4%P=i686-pc-windows-windows%r(
SF:NULL,1A,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03\(none\)\x20lo
SF:gin:\x20")%r(GenericLines,3A,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\
SF:xfb\x03\(none\)\x20login:\x20\r\n\r\n\(none\)\x20login:\x20\(none\)\x20
SF:login:\x20")%r(tn3270,28,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\
SF:x03\(none\)\x20login:\x20\^@IBM-3279-4-E")%r(GetRequest,2C,"\xff\xfd\x0
SF:1\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03GET\x20/\x20HTTP/1\.0\r\n\r\n\(non
SF:e\)\x20login:\x20")%r(RPCCheck,C,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\
SF:xff\xfb\x03")%r(Help,20,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x
SF:03HELP\r\n\(none\)\x20login:\x20")%r(SIPOptions,F9,"\xff\xfd\x01\xff\xf
SF:d\x1f\xff\xfb\x01\xff\xfb\x03OPTIONS\x20sip:nm\x20SIP/2\.0\r\nVia:\x20S
SF:IP/2\.0/TCP\x20nm;branch=foo\r\nFrom:\x20<sip:nm@nm>;tag=root\r\nTo:\x2
SF:0<sip:nm2@nm2>\r\nCall-ID:\x2050000\r\nCSeq:\x2042\x20OPTIONS\r\nMax-Fo
SF:rwards:\x2070\r\nContent-Length:\x200\r\nContact:\x20<sip:nm@nm>\r\nAcc
SF:ept:\x20application/sdp\r\n\r\n\(none\)\x20login:\x20")%r(NCP,44,"\xff\
SF:xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03DmdT\^@\^@\^@\x08\x20\x08\x0
SF:8\x20\x08\x08\x20\x08\x08\x20\x08\x08\x20\x08\x08\x20\x08\x08\x20\x08\x
SF:08\x20\x08\x08\x20\x08\x08\x20\x08\^@\^@\^@\^A\^@\^@\^@\^@");
MAC Address: 00:37:6D:4A:0F:84 (Murata Manufacturing)
Device type: phone
Running: Google Android 4.1.X
OS CPE: cpe:/o:google:android:4.1.2
OS details: Android 4.1.2
Uptime guess: 0.047 days (since Wed Apr 17 17:35:49 2024)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE
HOP RTT ADDRESS
1 43.65 ms 192.168.0.10
NSE: Script Post-scanning.
Initiating NSE at 18:43
Completed NSE at 18:43, 0.00s elapsed
Initiating NSE at 18:43
Completed NSE at 18:43, 0.00s elapsed
Initiating NSE at 18:43
Completed NSE at 18:43, 0.00s elapsed
Read data files from: C:\Program Files (x86)\Nmap
OS and Service detection performed. Please report any incorrect results at Nmap OS/Service Fingerprint and Correction Submission Page .
Nmap done: 1 IP address (1 host up) scanned in 177.50 seconds
Raw packets sent: 1023 (45.806KB) | Rcvd: 1016 (41.330KB)
Thank you
But it looks that they set different password for each camera
admin / admin123456 does not work for me, maybe credentials are correct, but port is missing. I tried to connect with:
Agent DVR
Synology Surveillance Station (NAS)
VLC Media Player -> rtsp:/192.168.0.10:8554/live/ch0 ... it asked for login, but admin / admin123456 does not work :-/ probably, because the port 8554 is not openned
And it looks that I have not openned port 8554. Or you openned it somehow?
Starting Nmap 7.94 ( Nmap: the Network Mapper - Free Security Scanner ) at 2024-04-17 18:40 Střední Evropa (letní čas)
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 18:41
Completed NSE at 18:41, 0.00s elapsed
Initiating NSE at 18:41
Completed NSE at 18:41, 0.00s elapsed
Initiating NSE at 18:41
Completed NSE at 18:41, 0.00s elapsed
Initiating ARP Ping Scan at 18:41
Scanning 192.168.0.10 [1 port]
Completed ARP Ping Scan at 18:41, 0.09s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 18:41
Completed Parallel DNS resolution of 1 host. at 18:41, 0.02s elapsed
Initiating SYN Stealth Scan at 18:41
Scanning 192.168.0.10 [1000 ports]
Discovered open port 23/tcp on 192.168.0.10
Discovered open port 843/tcp on 192.168.0.10
Discovered open port 1300/tcp on 192.168.0.10
Completed SYN Stealth Scan at 18:41, 2.19s elapsed (1000 total ports)
Initiating Service scan at 18:41
Scanning 3 services on 192.168.0.10
Completed Service scan at 18:43, 157.28s elapsed (3 services on 1 host)
Initiating OS detection (try #1) against 192.168.0.10
NSE: Script scanning 192.168.0.10.
Initiating NSE at 18:43
Completed NSE at 18:43, 14.14s elapsed
Initiating NSE at 18:43
Completed NSE at 18:43, 1.03s elapsed
Initiating NSE at 18:43
Completed NSE at 18:43, 0.00s elapsed
Nmap scan report for 192.168.0.10
Host is up (0.044s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
23/tcp open telnet
| fingerprint-strings:
| GenericLines:
| (none) login:
| (none) login: (none) login:
| GetRequest:
| HTTP/1.0
| (none) login:
| Help:
| HELP
| (none) login:
| NCP:
| DmdT^@^@^@
| ^@^@^@^A^@^@^@^@
| NULL:
| (none) login:
| SIPOptions:
| OPTIONS sip:nm SIP/2.0
| Via: SIP/2.0/TCP nm;branch=foo
| From: <sip:nm@nm>;tag=root
| <sip:nm2@nm2>
| Call-ID: 50000
| CSeq: 42 OPTIONS
| Max-Forwards: 70
| Content-Length: 0
| Contact: <sip:nm@nm>
| Accept: application/sdp
| (none) login:
| tn3270:
|_ (none) login: ^@IBM-3279-4-E
843/tcp open unknown
1300/tcp open h323hostcallsc?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at Nmap Fingerprint Submitter 2.0 :
SF-Port23-TCP:V=7.94%I=7%D=4/17%Time=661FFBA4%P=i686-pc-windows-windows%r(
SF:NULL,1A,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03\(none\)\x20lo
SF:gin:\x20")%r(GenericLines,3A,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\
SF:xfb\x03\(none\)\x20login:\x20\r\n\r\n\(none\)\x20login:\x20\(none\)\x20
SF:login:\x20")%r(tn3270,28,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\
SF:x03\(none\)\x20login:\x20\^@IBM-3279-4-E")%r(GetRequest,2C,"\xff\xfd\x0
SF:1\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03GET\x20/\x20HTTP/1\.0\r\n\r\n\(non
SF:e\)\x20login:\x20")%r(RPCCheck,C,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\
SF:xff\xfb\x03")%r(Help,20,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x
SF:03HELP\r\n\(none\)\x20login:\x20")%r(SIPOptions,F9,"\xff\xfd\x01\xff\xf
SF:d\x1f\xff\xfb\x01\xff\xfb\x03OPTIONS\x20sip:nm\x20SIP/2\.0\r\nVia:\x20S
SF:IP/2\.0/TCP\x20nm;branch=foo\r\nFrom:\x20<sip:nm@nm>;tag=root\r\nTo:\x2
SF:0<sip:nm2@nm2>\r\nCall-ID:\x2050000\r\nCSeq:\x2042\x20OPTIONS\r\nMax-Fo
SF:rwards:\x2070\r\nContent-Length:\x200\r\nContact:\x20<sip:nm@nm>\r\nAcc
SF:ept:\x20application/sdp\r\n\r\n\(none\)\x20login:\x20")%r(NCP,44,"\xff\
SF:xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03DmdT\^@\^@\^@\x08\x20\x08\x0
SF:8\x20\x08\x08\x20\x08\x08\x20\x08\x08\x20\x08\x08\x20\x08\x08\x20\x08\x
SF:08\x20\x08\x08\x20\x08\x08\x20\x08\^@\^@\^@\^A\^@\^@\^@\^@");
MAC Address: 00:37:6D:4A:0F:84 (Murata Manufacturing)
Device type: phone
Running: Google Android 4.1.X
OS CPE: cpe:/o:google:android:4.1.2
OS details: Android 4.1.2
Uptime guess: 0.047 days (since Wed Apr 17 17:35:49 2024)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE
HOP RTT ADDRESS
1 43.65 ms 192.168.0.10
NSE: Script Post-scanning.
Initiating NSE at 18:43
Completed NSE at 18:43, 0.00s elapsed
Initiating NSE at 18:43
Completed NSE at 18:43, 0.00s elapsed
Initiating NSE at 18:43
Completed NSE at 18:43, 0.00s elapsed
Read data files from: C:\Program Files (x86)\Nmap
OS and Service detection performed. Please report any incorrect results at Nmap OS/Service Fingerprint and Correction Submission Page .
Nmap done: 1 IP address (1 host up) scanned in 177.50 seconds
Raw packets sent: 1023 (45.806KB) | Rcvd: 1016 (41.330KB)
@danzimmer
Thank you
But it looks that they set different password for each camera
admin / admin123456 does not work for me, maybe credentials are correct, but port is missing. I tried to connect with:
Agent DVR
Synology Surveillance Station (NAS)
VLC Media Player -> rtsp:/192.168.0.10:8554/live/ch0 ... it asked for login, but admin / admin123456 does not work :-/ probably, because the port 8554 is not openned
And it looks that I have not openned port 8554. Or you openned it somehow?
Starting Nmap 7.94 ( Nmap: the Network Mapper - Free Security Scanner ) at 2024-04-17 18:40 Střední Evropa (letní čas)
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 18:41
Completed NSE at 18:41, 0.00s elapsed
Initiating NSE at 18:41
Completed NSE at 18:41, 0.00s elapsed
Initiating NSE at 18:41
Completed NSE at 18:41, 0.00s elapsed
Initiating ARP Ping Scan at 18:41
Scanning 192.168.0.10 [1 port]
Completed ARP Ping Scan at 18:41, 0.09s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 18:41
Completed Parallel DNS resolution of 1 host. at 18:41, 0.02s elapsed
Initiating SYN Stealth Scan at 18:41
Scanning 192.168.0.10 [1000 ports]
Discovered open port 23/tcp on 192.168.0.10
Discovered open port 843/tcp on 192.168.0.10
Discovered open port 1300/tcp on 192.168.0.10
Completed SYN Stealth Scan at 18:41, 2.19s elapsed (1000 total ports)
Initiating Service scan at 18:41
Scanning 3 services on 192.168.0.10
Completed Service scan at 18:43, 157.28s elapsed (3 services on 1 host)
Initiating OS detection (try #1) against 192.168.0.10
NSE: Script scanning 192.168.0.10.
Initiating NSE at 18:43
Completed NSE at 18:43, 14.14s elapsed
Initiating NSE at 18:43
Completed NSE at 18:43, 1.03s elapsed
Initiating NSE at 18:43
Completed NSE at 18:43, 0.00s elapsed
Nmap scan report for 192.168.0.10
Host is up (0.044s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
23/tcp open telnet
| fingerprint-strings:
| GenericLines:
| (none) login:
| (none) login: (none) login:
| GetRequest:
| HTTP/1.0
| (none) login:
| Help:
| HELP
| (none) login:
| NCP:
| DmdT^@^@^@
| ^@^@^@^A^@^@^@^@
| NULL:
| (none) login:
| SIPOptions:
| OPTIONS sip:nm SIP/2.0
| Via: SIP/2.0/TCP nm;branch=foo
| From: <sip:nm@nm>;tag=root
| <sip:nm2@nm2>
| Call-ID: 50000
| CSeq: 42 OPTIONS
| Max-Forwards: 70
| Content-Length: 0
| Contact: <sip:nm@nm>
| Accept: application/sdp
| (none) login:
| tn3270:
|_ (none) login: ^@IBM-3279-4-E
843/tcp open unknown
1300/tcp open h323hostcallsc?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at Nmap Fingerprint Submitter 2.0 :
SF-Port23-TCP:V=7.94%I=7%D=4/17%Time=661FFBA4%P=i686-pc-windows-windows%r(
SF:NULL,1A,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03\(none\)\x20lo
SF:gin:\x20")%r(GenericLines,3A,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\
SF:xfb\x03\(none\)\x20login:\x20\r\n\r\n\(none\)\x20login:\x20\(none\)\x20
SF:login:\x20")%r(tn3270,28,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\
SF:x03\(none\)\x20login:\x20\^@IBM-3279-4-E")%r(GetRequest,2C,"\xff\xfd\x0
SF:1\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03GET\x20/\x20HTTP/1\.0\r\n\r\n\(non
SF:e\)\x20login:\x20")%r(RPCCheck,C,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\
SF:xff\xfb\x03")%r(Help,20,"\xff\xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x
SF:03HELP\r\n\(none\)\x20login:\x20")%r(SIPOptions,F9,"\xff\xfd\x01\xff\xf
SF:d\x1f\xff\xfb\x01\xff\xfb\x03OPTIONS\x20sip:nm\x20SIP/2\.0\r\nVia:\x20S
SF:IP/2\.0/TCP\x20nm;branch=foo\r\nFrom:\x20<sip:nm@nm>;tag=root\r\nTo:\x2
SF:0<sip:nm2@nm2>\r\nCall-ID:\x2050000\r\nCSeq:\x2042\x20OPTIONS\r\nMax-Fo
SF:rwards:\x2070\r\nContent-Length:\x200\r\nContact:\x20<sip:nm@nm>\r\nAcc
SF:ept:\x20application/sdp\r\n\r\n\(none\)\x20login:\x20")%r(NCP,44,"\xff\
SF:xfd\x01\xff\xfd\x1f\xff\xfb\x01\xff\xfb\x03DmdT\^@\^@\^@\x08\x20\x08\x0
SF:8\x20\x08\x08\x20\x08\x08\x20\x08\x08\x20\x08\x08\x20\x08\x08\x20\x08\x
SF:08\x20\x08\x08\x20\x08\x08\x20\x08\^@\^@\^@\^A\^@\^@\^@\^@");
MAC Address: 00:37:6D:4A:0F:84 (Murata Manufacturing)
Device type: phone
Running: Google Android 4.1.X
OS CPE: cpe:/o:google:android:4.1.2
OS details: Android 4.1.2
Uptime guess: 0.047 days (since Wed Apr 17 17:35:49 2024)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE
HOP RTT ADDRESS
1 43.65 ms 192.168.0.10
NSE: Script Post-scanning.
Initiating NSE at 18:43
Completed NSE at 18:43, 0.00s elapsed
Initiating NSE at 18:43
Completed NSE at 18:43, 0.00s elapsed
Initiating NSE at 18:43
Completed NSE at 18:43, 0.00s elapsed
Read data files from: C:\Program Files (x86)\Nmap
OS and Service detection performed. Please report any incorrect results at Nmap OS/Service Fingerprint and Correction Submission Page .
Nmap done: 1 IP address (1 host up) scanned in 177.50 seconds
Raw packets sent: 1023 (45.806KB) | Rcvd: 1016 (41.330KB)
try this: VLC Media Player -> rtsp:/admin:admin123456@192.168.0.10:8554/profile0
to scan ports: nmap -p 1-65535 -T4 -A -v 192.168.0.10
Last edited:
It works now!try this: VLC Media Player -> rtsp:/admin:admin123456@192.168.0.10:8554/profile0
to scan ports: nmap -p 1-65535 -T4 -A -v 192.168.0.10
Thanks for help!
phoenixhui
n3wb
Hi, I have same isuue with using V360 (not V380) camera.
Its model no is IPC-FH8852v201.
I tried to copy the ceshi.ini file to root of the SD card, file details as below:
[CONST_PARAM]
rtsp=1
rtspaudio=1
audio=1
audiorec=1
audiorecord=1
micrec=1
mic=1
micrecord=1
telnet=1
ssh=1
onvif=1
web=1
webinterface=1
webif=1
http=1
The steps I tried as mentioned by others:
1. Power off camera
2. Insert SD card with ceshi.ini copied to root
3. Power on (and I keep SD card pluged-in)
4. Wait for over 3 minutes
Finally I used nmap to scan the cam and found that all ports are closed as below:
NSE: Loaded 157 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 09:18
Completed NSE at 09:18, 0.00s elapsed
Initiating NSE at 09:18
Completed NSE at 09:18, 0.00s elapsed
Initiating NSE at 09:18
Completed NSE at 09:18, 0.00s elapsed
Initiating ARP Ping Scan at 09:18
Scanning 192.168.1.141 [1 port]
Completed ARP Ping Scan at 09:18, 0.12s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 09:18
Completed Parallel DNS resolution of 1 host. at 09:18, 0.00s elapsed
Initiating SYN Stealth Scan at 09:18
Scanning IPC (192.168.1.141) [65535 ports]
SYN Stealth Scan Timing: About 21.69% done; ETC: 09:20 (0:01:52 remaining)
SYN Stealth Scan Timing: About 45.54% done; ETC: 09:20 (0:01:13 remaining)
SYN Stealth Scan Timing: About 68.63% done; ETC: 09:20 (0:00:42 remaining)
Completed SYN Stealth Scan at 09:19, 113.99s elapsed (65535 total ports)
Initiating Service scan at 09:19
Initiating OS detection (try #1) against IPC (192.168.1.141)
Retrying OS detection (try #2) against IPC (192.168.1.141)
NSE: Script scanning 192.168.1.141.
Initiating NSE at 09:19
Completed NSE at 09:19, 0.02s elapsed
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
Nmap scan report for IPC (192.168.1.141)
Host is up (0.0065s latency).
All 65535 scanned ports on IPC (192.168.1.141) are in ignored states.
Not shown: 65535 closed tcp ports (reset)
MAC Address: 34:A6:EF:44:94:B8 (Shenzhen Phaten Tech.)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: 2N Helios IP VoIP doorbell (92%), Advanced Illumination DCS-100E lighting controller (92%), AudioControl D3400 network amplifier (92%), British Gas GS-Z3 data logger (92%), Chamberlain myQ garage door opener (92%), Daikin DKN Cloud Wi-Fi Adaptor (92%), Daysequerra M4.2SI radio (92%), Denver Electronics AC-5000W MK2 camera (92%), Eve Cam (lwIP 2.1.0 - 2.2.0) (92%), Fatek FBs-CBEH PLC Ethernet communication board (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 6.47 ms IPC (192.168.1.141)
NSE: Script Post-scanning.
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
Read data files from: C:\Program Files (x86)\Nmap
OS and Service detection performed. Please report any incorrect results at Nmap OS/Service Fingerprint and Correction Submission Page .
Nmap done: 1 IP address (1 host up) scanned in 116.12 seconds
On the other hand, I tried to use VLC and onvif device management but both can't detect the camera.
So can anyone please help me to solve it?
I just want to know its username, password and port, then I can connect it to my Synology Surveillance Station for monitoring and backup.
Thank you very very much!
Its model no is IPC-FH8852v201.
I tried to copy the ceshi.ini file to root of the SD card, file details as below:
[CONST_PARAM]
rtsp=1
rtspaudio=1
audio=1
audiorec=1
audiorecord=1
micrec=1
mic=1
micrecord=1
telnet=1
ssh=1
onvif=1
web=1
webinterface=1
webif=1
http=1
The steps I tried as mentioned by others:
1. Power off camera
2. Insert SD card with ceshi.ini copied to root
3. Power on (and I keep SD card pluged-in)
4. Wait for over 3 minutes
Finally I used nmap to scan the cam and found that all ports are closed as below:
NSE: Loaded 157 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 09:18
Completed NSE at 09:18, 0.00s elapsed
Initiating NSE at 09:18
Completed NSE at 09:18, 0.00s elapsed
Initiating NSE at 09:18
Completed NSE at 09:18, 0.00s elapsed
Initiating ARP Ping Scan at 09:18
Scanning 192.168.1.141 [1 port]
Completed ARP Ping Scan at 09:18, 0.12s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 09:18
Completed Parallel DNS resolution of 1 host. at 09:18, 0.00s elapsed
Initiating SYN Stealth Scan at 09:18
Scanning IPC (192.168.1.141) [65535 ports]
SYN Stealth Scan Timing: About 21.69% done; ETC: 09:20 (0:01:52 remaining)
SYN Stealth Scan Timing: About 45.54% done; ETC: 09:20 (0:01:13 remaining)
SYN Stealth Scan Timing: About 68.63% done; ETC: 09:20 (0:00:42 remaining)
Completed SYN Stealth Scan at 09:19, 113.99s elapsed (65535 total ports)
Initiating Service scan at 09:19
Initiating OS detection (try #1) against IPC (192.168.1.141)
Retrying OS detection (try #2) against IPC (192.168.1.141)
NSE: Script scanning 192.168.1.141.
Initiating NSE at 09:19
Completed NSE at 09:19, 0.02s elapsed
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
Nmap scan report for IPC (192.168.1.141)
Host is up (0.0065s latency).
All 65535 scanned ports on IPC (192.168.1.141) are in ignored states.
Not shown: 65535 closed tcp ports (reset)
MAC Address: 34:A6:EF:44:94:B8 (Shenzhen Phaten Tech.)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: 2N Helios IP VoIP doorbell (92%), Advanced Illumination DCS-100E lighting controller (92%), AudioControl D3400 network amplifier (92%), British Gas GS-Z3 data logger (92%), Chamberlain myQ garage door opener (92%), Daikin DKN Cloud Wi-Fi Adaptor (92%), Daysequerra M4.2SI radio (92%), Denver Electronics AC-5000W MK2 camera (92%), Eve Cam (lwIP 2.1.0 - 2.2.0) (92%), Fatek FBs-CBEH PLC Ethernet communication board (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 6.47 ms IPC (192.168.1.141)
NSE: Script Post-scanning.
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
Read data files from: C:\Program Files (x86)\Nmap
OS and Service detection performed. Please report any incorrect results at Nmap OS/Service Fingerprint and Correction Submission Page .
Nmap done: 1 IP address (1 host up) scanned in 116.12 seconds
On the other hand, I tried to use VLC and onvif device management but both can't detect the camera.
So can anyone please help me to solve it?
I just want to know its username, password and port, then I can connect it to my Synology Surveillance Station for monitoring and backup.
Thank you very very much!
Brune
n3wb
Hello all,
V360 pro is manufactured from GatoCam in china.
I also has same problem so mailed.
 www.gatocam.com
www.gatocam.com
V360 pro is manufactured from GatoCam in china.
I also has same problem so mailed.
GatoCam Smart Home WIFI Camera Factory
GatoCam is a 12 years experienced Chinese Smart Camera Factory. Main Product: 4G Camera, WIFI Camera,Solar Camera, battery Camera. V360pro app Developer.
yours is V360, mine is V380Hi, I have same isuue with using V360 (not V380) camera.
Its model no is IPC-FH8852v201.
I tried to copy the ceshi.ini file to root of the SD card, file details as below:
those apps are not from the same developer (I checked apple store) so they is not the same and might not behave same
sorry but you have to seek help elsewhere
yours is V380, but if my files and steps dont help then the only option is contact v380technical@gmail.comHi,
My Camera type: C6S2X-L
Is there a way to enable Onvif on this camera? The methods read above did not help.
View attachment 207124
The camera mounts the SD card, but I don't see it reading the ini file.
dont know if they are still around