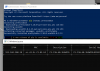
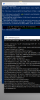
import socket
import os
import xml.etree.ElementTree as ET
from prettytable import PrettyTable
def send_udp_broadcast(packet, port, broadcast_ip, local_ip):
with socket.socket(socket.AF_INET, socket.SOCK_DGRAM, socket.IPPROTO_UDP) as sock:
sock.bind((local_ip, port))
sock.setsockopt(socket.SOL_SOCKET, socket.SO_BROADCAST, 1)
sock.sendto(packet, (broadcast_ip, port))
def listen_for_responses(port):
with socket.socket(socket.AF_INET, socket.SOCK_DGRAM, socket.IPPROTO_UDP) as sock:
sock.bind(("", port))
seen_devices = {} # To keep track of seen devices
while True:
data, _ = sock.recvfrom(24000)
root = ET.fromstring(data.decode('utf-8'))
device_info = {tag: root.find(tag).text for tag in ["MAC", "DeviceDescription", "DeviceSN", "IPv4Address", "DHCP"]}
seen_devices[device_info['MAC']] = [device_info[key] for key in ["IPv4Address", "DeviceDescription", "DeviceSN", "DHCP"]]
display_info(seen_devices)
def display_info(seen_devices):
os.system('clear' if os.name == 'posix' else 'cls') # Clear screen command for different OS
table = PrettyTable()
table.field_names = ["IPV4", "MAC", "Description", "Serial Number", "DHCP"]
for mac, info in seen_devices.items():
table.add_row([info[0], mac, info[1], info[2], info[3]])
print(table)
def get_local_ip():
with socket.socket(socket.AF_INET, socket.SOCK_DGRAM) as sock:
try:
sock.connect(('10.255.255.255', 1))
local_ip = sock.getsockname()[0]
except Exception:
local_ip = '127.0.0.1'
return local_ip
if __name__ == '__main__':
packet = bytes([0x3c, 0x3f, 0x78, 0x6d, 0x20, 0x76, 0x65, 0x72, 0x73, 0x69, 0x6f, 0x6e, 0x3d, 0x22, 0x31, 0x2e, 0x30, 0x22, 0x20, 0x65, 0x6e, 0x63, 0x6f, 0x64, 0x69, 0x6e, 0x67, 0x3d, 0x22, 0x75, 0x74, 0x66, 0x2d, 0x38, 0x22, 0x3f, 0x3e, 0x3c, 0x50, 0x72, 0x6f, 0x62, 0x65, 0x3e, 0x3c, 0x55, 0x75, 0x69, 0x64, 0x3e, 0x37, 0x34, 0x46, 0x31, 0x45, 0x44, 0x33, 0x37, 0x2d, 0x35, 0x45, 0x38, 0x32, 0x2d, 0x34, 0x33, 0x45, 0x38, 0x2d, 0x39, 0x41, 0x36, 0x31, 0x2d, 0x36, 0x36, 0x46, 0x43, 0x44, 0x33, 0x32, 0x39, 0x32, 0x36, 0x45, 0x32, 0x3c, 0x2f, 0x55, 0x75, 0x69, 0x64, 0x3e, 0x3c, 0x54, 0x79, 0x70, 0x65, 0x73, 0x3e, 0x69, 0x6e, 0x71, 0x75, 0x69, 0x72, 0x79, 0x3c, 0x2f, 0x54, 0x79, 0x70, 0x65, 0x73, 0x3e, 0x3c, 0x2f, 0x50, 0x72, 0x6f, 0x62, 0x65, 0x3e])
broadcast_ip = "239.255.255.250"
port = 37020
local_ip = get_local_ip()
send_udp_broadcast(packet, port, broadcast_ip, local_ip)
listen_for_responses(port)