sam988 asked me for help with this so posting for general benefit.
These instructions are for a Cisco WAP in autonomous mode. This applies to a dual VLAN design. One SSID will be for the home network, the other SSID will be for cameras (like a doorbell cam).
The benefit is that you don't need a separate WAP for cameras and you can still have VLAN separation.
Assumptions:
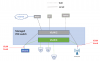
Home subnet is 192.168.29.0/24. This is VLAN 2. The SSID is homeSSID.
Camera subnet is 192.168.1.0/24. This is VLAN 4. The SSID is camSSID.
Router is connected to VLAN 2 with IP address 192.168.29.1
Managed switch IP address for VLAN 2 is 192.168.29.2.
The management IP for the WAP will be 192.168.29.3.
This is for a Cisco 3702i which can be found used on Ebay for under $40. Cisco Aironet 3700 Series Access Points Data Sheet. Similar configs for other models.
You know how to configure VLANs on your POE switch. The Cisco WAP is powered using POE.
Your cameras are only on the 2.4GHz spectrum so only the 2.4GHz radio is configured for camSSID. The home network is configured for both 2.4GHz and 5GHz.
The SSID for your home network is broadcast but the SSID for camera is hidden. You will have to explicit configure the SSID on your devices because they will not find them.
Security is using WPA2 personal (pre-shared keys). If you want to do WPA2 enterprise, ping me. You will need an external authentication server.
There is a web GUI for the WAP but it is limited. We are doing a special config for the VLAN separation so we are using CLI.
1. Make sure your AP is in autonomous mode. You can google for instructions.
2. Set the switch port connecting to the WAP to be a trunk. Set the native vlan for that port to be VLAN 2.
3. You can enter this config through the console or via remote terminal if you have that configured already. You will have to do the "crypto key generate..." to setup SSH.
4. Your configuration will look something like this. Note that some configuration left out because they were defaults.
5. You can access the web GUI and check out the config afterwards.
ip routing
ip domain name mydomain.com
!
dot11 ssid homeSSID
vlan 2
authentication open
authentication key-management wpa version 2
mbssid guest-mode
wpa-psk <this is your SSID password>
!
dot11 ssid camSSID
vlan 4
authentication open
authentication key-management wpa version 2
wpa-psk <this is your SSID password for cams>
!
!
username ADMIN privilege 15 secret <this is your admin password>
!
bridge irb
!
interface Dot11Radio0
no ip address
!
encryption vlan 2 mode ciphers aes-ccm
!
encryption vlan 4 mode ciphers aes-ccm
!
ssid homeSSID
!
ssid camSSID
!
antenna gain 0
stbc
mbssid
station-role root
!
interface Dot11Radio0.2
encapsulation dot1Q 2 native
bridge-group 2
!
interface Dot11Radio0.4
encapsulation dot1Q 4
bridge-group 4
!
!
interface Dot11Radio1
no ip address
!
encryption vlan 2 mode ciphers aes-ccm
!
ssid homeSSID
!
antenna gain 0
peakdetect
dfs band 3 block
stbc
mbssid
channel width 80
channel dfs
station-role root
!
interface Dot11Radio1.2
encapsulation dot1Q 2 native
bridge-group 2
!
interface GigabitEthernet0
no ip address
duplex auto
speed auto
!
interface BVI2
ip address 192.168.29.3 255.255.255.0
!
ip forward-protocol nd
no ip http server
ip http secure-server
ip route 0.0.0.0 0.0.0.0 192.168.29.1
!
bridge 2 route ip
!
line con 0
line vty 0 4
login local
transport input ssh
!
end
These instructions are for a Cisco WAP in autonomous mode. This applies to a dual VLAN design. One SSID will be for the home network, the other SSID will be for cameras (like a doorbell cam).
The benefit is that you don't need a separate WAP for cameras and you can still have VLAN separation.

Assumptions:
Home subnet is 192.168.29.0/24. This is VLAN 2. The SSID is homeSSID.
Camera subnet is 192.168.1.0/24. This is VLAN 4. The SSID is camSSID.
Router is connected to VLAN 2 with IP address 192.168.29.1
Managed switch IP address for VLAN 2 is 192.168.29.2.
The management IP for the WAP will be 192.168.29.3.
This is for a Cisco 3702i which can be found used on Ebay for under $40. Cisco Aironet 3700 Series Access Points Data Sheet. Similar configs for other models.
You know how to configure VLANs on your POE switch. The Cisco WAP is powered using POE.
Your cameras are only on the 2.4GHz spectrum so only the 2.4GHz radio is configured for camSSID. The home network is configured for both 2.4GHz and 5GHz.
The SSID for your home network is broadcast but the SSID for camera is hidden. You will have to explicit configure the SSID on your devices because they will not find them.
Security is using WPA2 personal (pre-shared keys). If you want to do WPA2 enterprise, ping me. You will need an external authentication server.
There is a web GUI for the WAP but it is limited. We are doing a special config for the VLAN separation so we are using CLI.
1. Make sure your AP is in autonomous mode. You can google for instructions.
2. Set the switch port connecting to the WAP to be a trunk. Set the native vlan for that port to be VLAN 2.
3. You can enter this config through the console or via remote terminal if you have that configured already. You will have to do the "crypto key generate..." to setup SSH.
4. Your configuration will look something like this. Note that some configuration left out because they were defaults.
5. You can access the web GUI and check out the config afterwards.
ip routing
ip domain name mydomain.com
!
dot11 ssid homeSSID
vlan 2
authentication open
authentication key-management wpa version 2
mbssid guest-mode
wpa-psk <this is your SSID password>
!
dot11 ssid camSSID
vlan 4
authentication open
authentication key-management wpa version 2
wpa-psk <this is your SSID password for cams>
!
!
username ADMIN privilege 15 secret <this is your admin password>
!
bridge irb
!
interface Dot11Radio0
no ip address
!
encryption vlan 2 mode ciphers aes-ccm
!
encryption vlan 4 mode ciphers aes-ccm
!
ssid homeSSID
!
ssid camSSID
!
antenna gain 0
stbc
mbssid
station-role root
!
interface Dot11Radio0.2
encapsulation dot1Q 2 native
bridge-group 2
!
interface Dot11Radio0.4
encapsulation dot1Q 4
bridge-group 4
!
!
interface Dot11Radio1
no ip address
!
encryption vlan 2 mode ciphers aes-ccm
!
ssid homeSSID
!
antenna gain 0
peakdetect
dfs band 3 block
stbc
mbssid
channel width 80
channel dfs
station-role root
!
interface Dot11Radio1.2
encapsulation dot1Q 2 native
bridge-group 2
!
interface GigabitEthernet0
no ip address
duplex auto
speed auto
!
interface BVI2
ip address 192.168.29.3 255.255.255.0
!
ip forward-protocol nd
no ip http server
ip http secure-server
ip route 0.0.0.0 0.0.0.0 192.168.29.1
!
bridge 2 route ip
!
line con 0
line vty 0 4
login local
transport input ssh
!
end
Last edited:
