I took the liberty to take this from our documentation. Hope this helps

But as jarrow has said before me. If you can, use the VPN Method. It's a bit more finicky to set up but safer in the long run.
1.device that integrates only the P2P function.
To use UDP hole punch technology for remote access, the firewall output of the device must allow the following ports:
● UDP ports: 0-65535
● TCP ports: 9116, 9118, 12366, 12367
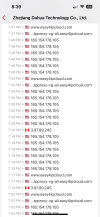
● Dahua servers use dynamic IP addresses, their domain names and functions are:
| Domain Name | Function |
| easy4ipcloud.com | Device login and registration |
| easy4ip.com | Device login and registration |
2.Device supporting P2P and Cloud Business
To use UDP hole punch technology for remote access and normal operation of video surveillance services, the firewall output of the device must allow the following ports:
● UDP ports: 0-65535
● TCP ports: 443, 9112, 9113, 9116, 9118, 10000, 12367, 15100, 15101, 15301, 15600, 15900, 16759
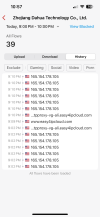
● Dahua servers use dynamic IP addresses, their domain names and functions are:
| Domain Name | Function |
| easy4ipcloud.com | Device login and registration |
| easy4ip.com | Device login and registration |
| dms.easy4ipcloud.com | Device login and registration |
| paas-dms-edge-fk.easy4ipcloud.com | Device login and registration |
| smartdeviceproxy-edge-fk.easy4ipcloud.com | Device login and registration |
| devaccess.easyipcloud.com | Device login and registration |
| dus.easy4ipcloud.com | Cloud upgrade of device firmware |
| aktualisieren.easy4ip.com | Cloud upgrade of device firmware |
| update.easyviewercloud.com | Cloud upgrade of device firmware |
| vrs.easy4ipcloud.com | Upload device images and videos |
| pps.easy4ipcloud.com | Upload device messages |
| das.easy4ipcloud.com | Upload device messages |
| das-fk.easy4ipcloud.com | Upload device messages |
| devicelogserver-fk.easy4ipcloud.com | Uploading device log |