I'm working towards transitioning my network from a flat network to a segmented network with at least 3-4 zones, using pfsense as my firewall. At some point down the road I will move all of my cameras to a completely isolated network with a dedicated connection to a 2nd NIC on my BI computer, but for now I'm using this as an opportunity to learn firewalling. So I want to figure out how to make this work today, even though this will not be my configuration tomorrow.
Last week I had my BI PC and all my cameras on the same subnet, and everything worked fine, as you'd expect.
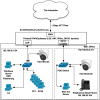
Yesterday I experimented by putting one camera (.50.26) on a new LAN like this. I'm the "me" computer in the LAN0 subnet:
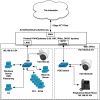
Right now LAN0 has the default "pass any/any" firewall rule:

so I can access from "me" to the Amcrest camera at .50.26, in a browser with live video (which I believe travels over HTTP).
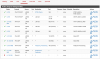
I set up a rule on the LAN50 side to allow RTSP traffic to come back:

where RTSP_Clients is an alias that includes the IP addresses for both the "me" PC and the BI PC. With this set of rules, BI can see (and serve) the stream from the 50.26 camera. I can also see the RTSP stream in VLC. All good so far.
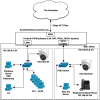
Today I tried moving the BI PC camera to the LAN50 side:
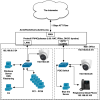
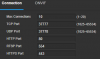
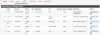
Because the LAN50 side lacks the default "pass any/any" rule, I tried enabling a bunch of rules to allow the BI PC to see the camera that's still on the .0 side, e.g. 192.168.0.24, per the camera's settings:
I can access the .0.24 camera from a browser in the BI PC, including live video, but I cannot view an RTSP stream in VLC from the BI PC.
BI can interrogate the 0.24 camera's settings via ONVIF and the Find/Inspect button, but it cannot get the RTSP stream.
If I add a "pass any/any" firewall rule on the LAN50 side then VLC and BI both work from the BI PC, but of course that defeats the whole purpose of segmenting my network. But it at least tells me the problem is the firewall rules on the LAN50 side and not anything on the LAN0 side.
Am I missing some ports in my firewall rules? Thanks!
Last week I had my BI PC and all my cameras on the same subnet, and everything worked fine, as you'd expect.
Yesterday I experimented by putting one camera (.50.26) on a new LAN like this. I'm the "me" computer in the LAN0 subnet:

Right now LAN0 has the default "pass any/any" firewall rule:
so I can access from "me" to the Amcrest camera at .50.26, in a browser with live video (which I believe travels over HTTP).
I set up a rule on the LAN50 side to allow RTSP traffic to come back:
where RTSP_Clients is an alias that includes the IP addresses for both the "me" PC and the BI PC. With this set of rules, BI can see (and serve) the stream from the 50.26 camera. I can also see the RTSP stream in VLC. All good so far.
Today I tried moving the BI PC camera to the LAN50 side:

Because the LAN50 side lacks the default "pass any/any" rule, I tried enabling a bunch of rules to allow the BI PC to see the camera that's still on the .0 side, e.g. 192.168.0.24, per the camera's settings:

I can access the .0.24 camera from a browser in the BI PC, including live video, but I cannot view an RTSP stream in VLC from the BI PC.
BI can interrogate the 0.24 camera's settings via ONVIF and the Find/Inspect button, but it cannot get the RTSP stream.
If I add a "pass any/any" firewall rule on the LAN50 side then VLC and BI both work from the BI PC, but of course that defeats the whole purpose of segmenting my network. But it at least tells me the problem is the firewall rules on the LAN50 side and not anything on the LAN0 side.
Am I missing some ports in my firewall rules? Thanks!

 Fixed:
Fixed: