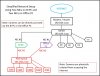
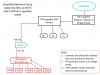
Also just to add to the conversation when a network is simply isolated via software or managed by a central firewall router appliance like pfSense.
Rules can be made to allow any network to be accessed and routed to.
Regardless, anyone who is serious about video security will not have the same on the regular LAN. Nor will they allow any physical connection to the Internet whether in or out.
The obvious benefits of following this simple and common sense approach is zero impact to the existing LAN as it pertains to bandwidth.
If something is physically (island) isolated it’s near impossible to breach the system without being on site tapping into the same!

Running a dual NIC is definitely the easiest to deploy for anyone. Those who rely on software VLAN’s also benefit from the ease of segregation and isolation but should NEVER ever forget. Any software can be compromised and history has proven VLAN’s are not immune to a breach.
Cisco the largest network company has patched up no less than five VLAN issues during the course of five years. The industry as a whole has either fixed, identified, or left open holes in VLAN implementation depending upon who the vendor is!
This also applies to the use of VPN. There have been no less than 25 incidents of compromise or breaches mostly as it relates to services vs the tunnel communications.
If one takes the time to Google any encryption you will quickly learn every known system as broken. Hence the depreciation of SSL and many other so called keys.
Ultimately if one applies all of the industry best practices & techniques you’ll surely be further ahead vs doing nothing! Just don’t fall prey to thinking nothing can ever happen as every government that has more money & resources than God has been hacked!

Name any 3 letter government agency = Hacked. Any industry = Hacked. Any business = Hacked
As such always update, patch, iterate, and stay informed with the latest news and possible solutions to mitigate the same!