I recently purchased an IP4M-1041B and have it set up on an isolated wifi network after first configuring it via the web UI over wired ethernet. At my firewall, I have an explicit block and log rule for outbound traffic from this isolated subnet. I have identified two abnormal behaviors from this camera that I'm curious about. One is that it retains factory default DNS servers when configured via DHCP, and the other is that this camera is constantly trying to contact AWS, despite no "cloud" configuration being obviously present.
The firmware on the camera is up to date:
Software Version: V2.800.00AC003.0.R, Build Date: 2022-08-11
WEB Version: V3.2.1.18144
ONVIF Version: 21.12(V3.1.0.1207744)
Other configuration notes:
DNS Problem
I configured the IP via DHCP, and noticed that despite my DHCP server handing out my internal nameserver addresses, the camera retained its default settings of 8.8.8.8 and 8.8.4.4 for nameservers, so I had to manually reconfigure the TCP/IP settings with my nameservers, which are handed out correctly via DHCP without issue to every other host on the network.
AWS Problem
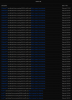
In PFSense, I see that this camera is trying to contact AWS pretty much all the time. I have included a minute's worth of log entries, but there are hundreds of identical entries, multiple times per minute, over 12+ hours. See end of post for those logs.
I understand from the documentation that this camera will try to contact "Amcrest Cloud" for 2 hours after every reboot, but the documented attempts to contact occur well past that timeframe.
I have an Amcrest IP8M-T2599EW that exhibits NONE of the above behaviors.
I recognize that this camera is more of a convenient home use camera than it is a professional grade camera, but I would still expect some reasonable behavior from it. It is a convenient form factor for moving around the house as needed as it does not need to be affixed to a surface, which is why I have it. Are these DHCP/DNS and AWS issues expected behavior, or bugs?
For clarity, 192.168.60.205 is the Amcrest camera.
The firmware on the camera is up to date:
Software Version: V2.800.00AC003.0.R, Build Date: 2022-08-11
WEB Version: V3.2.1.18144
ONVIF Version: 21.12(V3.1.0.1207744)
Other configuration notes:
- I have no cloud storage configured.
- I have no SD card installed.
- I have disabled P2P and did not use it to set the camera up.
- I have no DDNS set up.
- I have disabled UPnP.
- I do not have any SMTP set up.
- I do not have any remote recording setup, no storage destinations configured, no motion/tamper/audio/abnormality detect configured.
- I used only the web UI to configure the camera, and am primarily getting video from this device via RTSP to Frigate.
- I have not factory reset the camera yet.
DNS Problem
I configured the IP via DHCP, and noticed that despite my DHCP server handing out my internal nameserver addresses, the camera retained its default settings of 8.8.8.8 and 8.8.4.4 for nameservers, so I had to manually reconfigure the TCP/IP settings with my nameservers, which are handed out correctly via DHCP without issue to every other host on the network.
AWS Problem
In PFSense, I see that this camera is trying to contact AWS pretty much all the time. I have included a minute's worth of log entries, but there are hundreds of identical entries, multiple times per minute, over 12+ hours. See end of post for those logs.
I understand from the documentation that this camera will try to contact "Amcrest Cloud" for 2 hours after every reboot, but the documented attempts to contact occur well past that timeframe.
I have an Amcrest IP8M-T2599EW that exhibits NONE of the above behaviors.
I recognize that this camera is more of a convenient home use camera than it is a professional grade camera, but I would still expect some reasonable behavior from it. It is a convenient form factor for moving around the house as needed as it does not need to be affixed to a surface, which is why I have it. Are these DHCP/DNS and AWS issues expected behavior, or bugs?
For clarity, 192.168.60.205 is the Amcrest camera.
| Action | Time | Interface | Source | Destination | Protocol |
|---|---|---|---|---|---|
| Block | Feb 11 05:23:01 | VLAN60 | 192.168.60.205:36094 | 34.227.196.242:443 | TCP:S |
| Block | Feb 11 05:23:10 | VLAN60 | 192.168.60.205:55454 | 34.234.184.106:443 | TCP:S |
| Block | Feb 11 05:23:11 | VLAN60 | 192.168.60.205:55454 | 34.234.184.106:443 | TCP:S |
| Block | Feb 11 05:23:14 | VLAN60 | 192.168.60.205:55454 | 34.234.184.106:443 | TCP:S |
| Block | Feb 11 05:23:18 | VLAN60 | 192.168.60.205:55454 | 34.234.184.106:443 | TCP:S |
| Block | Feb 11 05:23:30 | VLAN60 | 192.168.60.205:55456 | 34.234.184.106:443 | TCP:S |
| Block | Feb 11 05:23:31 | VLAN60 | 192.168.60.205:55456 | 34.234.184.106:443 | TCP:S |
| Block | Feb 11 05:23:33 | VLAN60 | 192.168.60.205:55456 | 34.234.184.106:443 | TCP:S |
| Block | Feb 11 05:23:37 | VLAN60 | 192.168.60.205:55456 | 34.234.184.106:443 | TCP:S |
| Block | Feb 11 05:23:46 | VLAN60 | 192.168.60.205:36104 | 34.227.196.242:443 | TCP:S |
| Block | Feb 11 05:23:47 | VLAN60 | 192.168.60.205:36104 | 34.227.196.242:443 | TCP:S |
| Block | Feb 11 05:23:49 | VLAN60 | 192.168.60.205:36104 | 34.227.196.242:443 | TCP:S |
| Block | Feb 11 05:23:53 | VLAN60 | 192.168.60.205:36104 | 34.227.196.242:443 | TCP:S |
Last edited: