Hello!
I have several Imou cameras at home (I think they are DAHUA rebranded models), currently pointing towards the garden. I'd like to use some of them indoors, but privacy is a concern. So, I set up Frigate to monitor the RTSP stream from the cameras and configured a router with a firewall to block internet traffic for the cameras' IPs. When I activate the firewall, I lose connectivity on the Imou app, indicating that at least that connection is being blocked. Yay!
However, I'm not 100% sure they're not connecting in some other way. So, I thought of using a network analyzer, Wireshark, for the first time.
I started Wireshark, set up a filter to watch only the LAN IP range of my cameras (both sending or reciving), and saw this:
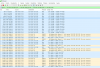
So I thought, this is working, I see no "outside" connections. Nice!
To double-check, I tried the opposite: I deactivated the firewall and opened the app on my mobile, and I could see the cameras, thus confirming hey're connecting to the cloud.
I went to Wireshark and... no new connections. I saw the same type of info as before. So, Wireshark isn't detecting the connection to the cloud. How can I be sure then?
So... what am I doing wrong, and what can I do to see those cloud connections in Wireshark? Theoretically, I'm "secured," but I want to make sure!
PD: according to chatgpt:
I have several Imou cameras at home (I think they are DAHUA rebranded models), currently pointing towards the garden. I'd like to use some of them indoors, but privacy is a concern. So, I set up Frigate to monitor the RTSP stream from the cameras and configured a router with a firewall to block internet traffic for the cameras' IPs. When I activate the firewall, I lose connectivity on the Imou app, indicating that at least that connection is being blocked. Yay!
However, I'm not 100% sure they're not connecting in some other way. So, I thought of using a network analyzer, Wireshark, for the first time.
I started Wireshark, set up a filter to watch only the LAN IP range of my cameras (both sending or reciving), and saw this:

So I thought, this is working, I see no "outside" connections. Nice!
To double-check, I tried the opposite: I deactivated the firewall and opened the app on my mobile, and I could see the cameras, thus confirming hey're connecting to the cloud.
I went to Wireshark and... no new connections. I saw the same type of info as before. So, Wireshark isn't detecting the connection to the cloud. How can I be sure then?
So... what am I doing wrong, and what can I do to see those cloud connections in Wireshark? Theoretically, I'm "secured," but I want to make sure!
PD: according to chatgpt:
The IP addresses 239.255.255.251 and 224.0.0.22 are both used for specific types of multicast communications in IP networking.
Summary
- 239.255.255.251:
- This is the multicast address used for mDNS (Multicast DNS). mDNS is used for resolving hostnames to IP addresses within small networks that do not include a local name server. It is part of the Zeroconf protocol suite and is widely used for device discovery and service advertisement on local networks, such as discovering printers, cameras, or other network devices.
- 224.0.0.22:
- This is the multicast address used by IGMP (Internet Group Management Protocol) Version 3. IGMP is used by IP hosts to report their multicast group memberships to any immediately neighboring multicast routers. Specifically, 224.0.0.22 is used by IGMPv3 for sending Membership Report and Membership Query messages.
These addresses facilitate various network functionalities and are part of the normal operation of many devices and services on local area networks. If you're seeing traffic to these addresses, it's likely related to device discovery or multicast group management.
- 239.255.255.251: Multicast DNS (mDNS), used for device discovery on local networks.
- 224.0.0.22: IGMPv3, used for managing multicast group memberships.
Last edited:
