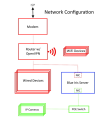
Hello! I've got BI working pretty good on a Swann camera-salvage home system. It runs on a separate computer 192.168.10.xxx. I have my home network on 192.168.0.xxx using Omada ER605. A POE switch powers the cameras, and an open port is plugged into an unmanaged switch on the xxx.0.xxx home network. Wife wants to see the cameras on her phone. I created VLAN 10 and a VPN in the ER605, but am getting bogged down somewhere either on the 2 networks or on the OpenVPN. I cannot get to BI on 192.168.10.xxx and of course I'm doing something wrong. Any tutorial or vids with this re-hashed scenario? Thanks!