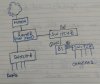
I'm at the stage now where I'm planning out my network for my house currently under construction. I am going the UniFi way of doing things, will get an Edge Router X, and for my setup, I'll have two switches, one UniFi 16 port PoE+ switch and for the other a UniFi 16-24 port non-PoE switch.
Anyway, all my cameras will be hooked into the PoE switch, along with the Blue Iris computer, with about 5 or 6 ports spare. The other switch will cater for all room points.
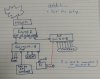
My question is, I'm thinking of using the spare PoE ports for my UniFi Access Points but they'll be on the same switch as my camera setup. Can the 3 or 4 Access Points be separated away from the cameras using VLAN. At this point, if the answer is yes, they can be separated, I don't need a detailed how to do it post (if one is forthcoming or a link that would be appreciated). As I write this I think I'm answering my own question but still would like to put it out there.
What I'm trying to avoid is purchasing a second switch with PoE abilities, hence, extra cost.
Anyway, all my cameras will be hooked into the PoE switch, along with the Blue Iris computer, with about 5 or 6 ports spare. The other switch will cater for all room points.
My question is, I'm thinking of using the spare PoE ports for my UniFi Access Points but they'll be on the same switch as my camera setup. Can the 3 or 4 Access Points be separated away from the cameras using VLAN. At this point, if the answer is yes, they can be separated, I don't need a detailed how to do it post (if one is forthcoming or a link that would be appreciated). As I write this I think I'm answering my own question but still would like to put it out there.
What I'm trying to avoid is purchasing a second switch with PoE abilities, hence, extra cost.