catcamstar
Known around here
- Jan 28, 2018
- 1,656
- 1,196
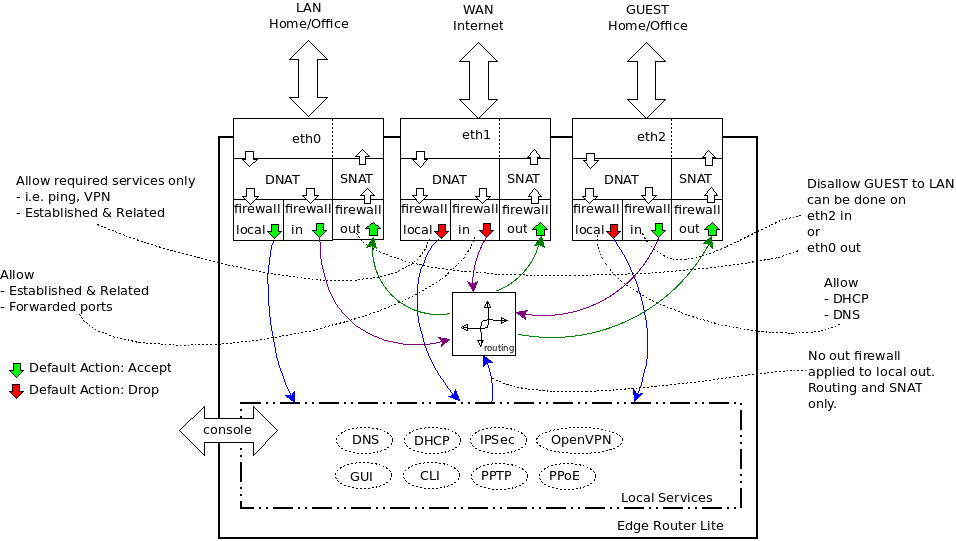
I have a limited understanding of VLANs, but based on the Ubiquity configs I've been messing around with it APPEARS to me that if something is connected to a switch port and the PORT is assigned a VLAN, that regardless of any trickery, anything attached to that port will get tagged to the assigned VLAN.
Well, there are a couple of things to mention:
- if you talk about a "port" on Ubiquity: either you put a physical port in 1 vlan, which renders that physical port to that vlan, anything else you put behind it (even if the device "fakes" trunking/port tagging or any other jokes), it falls in that vlan. This does mean that you "might" loose physical ports against the "flexibility" of using vlans. This is off course a security versus manageability trade-off.
- if you do enforce tagging on a physical port, you need to understand that IF anything behind that port "fakes" (forges?) a vlan, it can do whatever it wants IN that vlan. If that vlan can reach the internet, well, you get the idea.
- BY DEFAULT, a VLAN is like a physically constructed LAN (with classic ethernet switches). This said: there is absolutely no OUT OF THE BOX routing! It's like stacking 2 switches with on top of each other, without an interconnection. YOU define the routing (and now we are entering the debate: do you want a L2 router or a L3 switch) - which means that a vlan cannot out of the box "open" the internet for your vlan devices (eg camera's). Hence my "black hole vlan". It does what its name says it does.
- that's why I explained above that it makes more sense to do the L2 switching on a switch than "forcing" a L3 capable router do some "stupid" switching. MAC allocation tables in switches serve their purpose
Someone had posted some crazy attempts by a camera to escape containment, I just can't ever find that thread on these forums to refer back against. But surely one of the more potentially insidious things to have to worry about is the camera being programmed to try and find a path out of the network.
I've seen that post too. And I know of other devices that spawn random mac addresses, forks random dhcp "fake" leases, and even create docker instances on botnetted devices to bypass any firewall. The internet has changed a lot since 1992, it's better be safe than sorry.
And don't forget the most important rule: you enforce the security you want, because in 10 years, everything on this forum is obsolete anyhow ;-)
Good luck!
CC