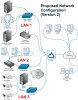
Segregating our networked IP cameras
- Thread starter Q™
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Yes, but I was commenting on his specific setup and he has a cisco firewall, which has more than one interface.
Yes, our Pix 515e has 3 (or 4?) WAN interfaces...but we only use 1 of the 3. However, the Pix is 15 years old and it's time to put it to pasture IMO. We don't have a lot of money to spend on this stuff so the plan is to replace the Pix 515e with a Cisco ASA 5506-X which -- I believe -- has eight (8) WAN interface ports.
So then this is the solution which may address my needs:...
1) Create three (3) physically separate and distinct LANs (each isolated on it's own switch).
2) Each LAN will connect to it's own Cisco ASA 5506-X interface port.
3) Dual hone the BI server on LAN 3 so that WAN devices -- and LAN 1 devices\workstations -- will be able to access the Blue Iris server on LAN 3.
What do you guys think? Is this my "best solution" given my extremely limited budget and sadly limited technical ability?
j4co
Pulling my weight
Why dual home the BI server, than that becomes a weak point in the security.
If you need remote access from user pc to BI server, open the ports in the firewall to communicate from that vlan to the BI vlan. Also any traffic from the BI vlan (ntp and whatever) can go out if needed based on rules.
The best idea with firewall is to deny anything, and only permit things you think are needed.
Again, firewalls is not my work, but i read a lot on it when i worked on my own firewall.
But you better look for info and help on cisco support forums. I assume more skilled people will help you there.
If you need remote access from user pc to BI server, open the ports in the firewall to communicate from that vlan to the BI vlan. Also any traffic from the BI vlan (ntp and whatever) can go out if needed based on rules.
The best idea with firewall is to deny anything, and only permit things you think are needed.
Again, firewalls is not my work, but i read a lot on it when i worked on my own firewall.
But you better look for info and help on cisco support forums. I assume more skilled people will help you there.
hmjgriffon
Known around here
" data-source="post: 149356"
class="bbCodeBlock bbCodeBlock--expandable bbCodeBlock--quote js-expandWatch">
Save a ton of money by replacing the pix with something many times cheaper and easy to use like a pfsense firewall, Cisco stuff is criminally expensive, how much is an ASA like a couple grand? The rest of the plan sounds good, put each vlan on its own gear and run it all back to the firewall, dual homing the bi box is totally unnecessary, you can control all access at the firewall. Keep it simple.
Yes, our Pix 515e has 3 (or 4?) WAN interfaces...but we only use 1 of the 3. However, the Pix is 15 years old and it's time to put it to pasture IMO. We don't have a lot of money to spend on this stuff so the plan is to replace the Pix 515e with a Cisco ASA 5506-X which -- I believe -- has eight (8) WAN interface ports.
So then this is the solution which may address my needs:...
1) Create three (3) physically separate and distinct LANs (each isolated on it's own switch).
2) Each LAN will connect to it's own Cisco ASA 5506-X interface port.
3) Dual hone the BI server on LAN 3 so that WAN devices -- and LAN 1 devices\workstations -- will be able to access the Blue Iris server on LAN 3.
What do you guys think? Is this my "best solution" given my extremely limited budget and sadly limited technical ability?
So then this is the solution which may address my needs:...
1) Create three (3) physically separate and distinct LANs (each isolated on it's own switch).
2) Each LAN will connect to it's own Cisco ASA 5506-X interface port.
3) Dual hone the BI server on LAN 3 so that WAN devices -- and LAN 1 devices\workstations -- will be able to access the Blue Iris server on LAN 3.
What do you guys think? Is this my "best solution" given my extremely limited budget and sadly limited technical ability?
j4co
Pulling my weight
My simple firewall is based on this setup: Intel Mini-ITX Atom 8-core Hardware Build Recipe Available Here
Hardware:
supermicro MBD-A1SRI-2758F-O
2 x samsung M474B1G73QH0-YK0 (8 GB Sodimm)
M350 mini-ITX casE
3x Evercool EC4015SH12BP
samsung MZ7WD240HCFV-00003 240 GB SSD
192 watt 12 volt brick
This thread gave me great insight in firewall setup: Taming the beasts... aka suricata blueprint
It can do 1 GE line speed with file copy between lan and wan in tests.
This was without much services installed though. No surrecata or snort for example running.
I simply trunk vlans over 1 cable into the firewall, but it has 4 interfaces onboard.
This is like 450€ or so in total from what i remember.
Hardware:
supermicro MBD-A1SRI-2758F-O
2 x samsung M474B1G73QH0-YK0 (8 GB Sodimm)
M350 mini-ITX casE
3x Evercool EC4015SH12BP
samsung MZ7WD240HCFV-00003 240 GB SSD
192 watt 12 volt brick
This thread gave me great insight in firewall setup: Taming the beasts... aka suricata blueprint
It can do 1 GE line speed with file copy between lan and wan in tests.
This was without much services installed though. No surrecata or snort for example running.
I simply trunk vlans over 1 cable into the firewall, but it has 4 interfaces onboard.
This is like 450€ or so in total from what i remember.
hmjgriffon
Known around here
There you go, I bought parts off Amazon and put mine together, ASAs can be a pain to configure, and Cisco may not even include everything you want in their base license which means even more $$$$. Only thing Cisco it's good for is job security of network engineers and security guys lol.My simple firewall is based on this setup: Intel Mini-ITX Atom 8-core Hardware Build Recipe Available Here
Hardware:
supermicro MBD-A1SRI-2758F-O
2 x samsung M474B1G73QH0-YK0 (8 GB Sodimm)
M350 mini-ITX casE
3x Evercool EC4015SH12BP
samsung MZ7WD240HCFV-00003 240 GB SSD
192 watt 12 volt brick
This thread gave me great insight in firewall setup: Taming the beasts... aka suricata blueprint
It can do 1 GE line speed with file copy between lan and wan in tests.
This was without much services installed though. No surrecata or snort for example running.
I simply trunk vlans over 1 cable into the firewall, but it has 4 interfaces onboard.
This is like 450€ or so in total from what i remember.
nayr
IPCT Contributor
Ubiquiti EdgeRouters do GigE subnet routing and can be had for a fair price..
pFSense could not scale for shit so I left it behind long ago, wouldn't use multiple cores just a single one.
pFSense could not scale for shit so I left it behind long ago, wouldn't use multiple cores just a single one.
hmjgriffon
Known around here
I think it does now, either freeBSD, which is pfsense, or OpenBSD does more than one core, pretty sure it's freeBSD. Ubiquity is nice stuff though too.Ubiquiti EdgeRouters do GigE subnet routing and can be had for a fair price..
pFSense could not scale for shit so I left it behind long ago, wouldn't use multiple cores just a single one.
tigerwillow1
Known around here
Reading this sends me begging for help. I'm using a Cisco SF300-24P managed switch that supports layer 3. I originally thought I could just set up a couple of overlapping vlans (one for the home network, one for the cameras), with the nvr and computer as members of both, to keep the cameras from being able to access the wan. The switch allows me to configure it this way, but it doesn't work as I want it to. The nvr and computer can access only one of the vlans at any given time based on their port's pdid setting. From what I've read, I should be able to do what I want with L3 routing on the switch. Is that correct? And any hints would be appreciated. I'm getting nowhere with just the switch manual.My work is in L3 routing with large cisco devices with m-bgp over mpls.
I will ask a firewall collegue monday.
Save a ton of money by replacing the pix with something many times cheaper and easy to use like a pfsense firewall, Cisco stuff is criminally expensive, how much is an ASA like a couple grand? ...
...Only thing Cisco it's good for is job security of network engineers and security guys lol.
Not much love for Cisco, eh?
The Cisco ASA 5506-X has been quoted at $850.00 from a local vendor. The engineer who will write the configuration is quoted at $90.00 hour. I certainly could write the configuration but it'd probably take me a couple of weeks to learn how and I don't have that kind of time. You see, I'm a small business owner. I sign the checks, negotiate contracts with billion-dollar corporations, rebuild the RAID array, shovel the snow and take out the garbage. And while I'm good at IT it takes me a long time to learn shit...then I don't use the shit I learned for a couple of years...and when I need that shit again...I have to learn the shit all over again. I believe the last time I did serious work inside the Pix config was something like 3-years ago, and since then I'm been doing simple port opens and closings. No, I don't think so. I'll pay the network engineer to write the config and get the ASA working and then I'll rummage around in there and figure out how it works a little bit at a time. The company providing the services uses Cisco gear, so it's their call and I'm willing to part with the cash to get it done.
But everyone's help is greatly appreciated, and I consider myself sincerely fortunate to receive it.
Thank you fellas.
j4co
Pulling my weight
I like your approach. If you have support from that company, I would do the same.
At least you know your idea is possible.
At least you know your idea is possible.
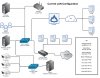
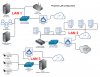
Not much love for Cisco, eh? View attachment 14078
The Cisco ASA 5506-X has been quoted at $850.00 from a local vendor. The engineer who will write the configuration is quoted at $90.00 hour. I certainly could write the configuration but it'd probably take me a couple of weeks to learn how and I don't have that kind of time. You see, I'm a small business owner. I sign the checks, negotiate contracts with billion-dollar corporations, rebuild the RAID array, shovel the snow and take out the garbage. And while I'm good at IT it takes me a long time to learn shit...then I don't use the shit I learned for a couple of years...and when I need that shit again...I have to learn the shit all over again. I believe the last time I did serious work inside the Pix config was something like 3-years ago, and since then I'm been doing simple port opens and closings. No, I don't think so. I'll pay the network engineer to write the config and get the ASA working and then I'll rummage around in there and figure out how it works a little bit at a time. The company providing the services uses Cisco gear, so it's their call and I'm willing to part with the cash to get it done.
But everyone's help is greatly appreciated, and I consider myself sincerely fortunate to receive it.
Thank you fellas.
I understand fully, Sometimes you have bite the bullet and let the trained professionals do their thing. All those guys LOVE Cisco stuff and for good reason.
Its a security and support issue. $90 a hour is very fair considering the rates up here in NY. Time is money for me and I know my limitations and when its worth paying somebody to do what it would take me days to figure out. Like getting my sorry ass on a ladder and cleaning out my gutters. I could spend half a day on a Saturday doing it or hire a team to do it for $150 bucks. That $150 bucks would not even cover my hospital deductible after I fell of the ladder. Well spent money.

 said:
said: