I would suggest stop listening to
@tech_junkie
I get headache from what he writes
I dont understand why someone would plan a network like him, but everyone does things different. some people like problems, others not. there is no final solution.
You should think about these:
Cellular and wifi bridge connection are things you use when its impossible or too expensive to run a cable. It will never ever outperform a cable.
Cellular has horrible latency. wifi still has bad latency, better than cellular. Many things can make the connection worse, like weather.
You dont want latency when you can avoid it. You dont want unreliable connections.
Most providers only allow one connection. Then you wont be able to establish two for two routers. You end up connection them together. New cascade, new problems.
Connecting 2 routers together is a bad idea. People still do because they dont know better.
You get a nice thing called double nat.
You can get over some problems you get, but its hard to configure correctly.
You should think what your plan was at first.
2 NIC solutions are for people who have small networks. Some cameras around the house, short cable ways.
Can simply add another switch, connect all cams to it and connect the nvr/bi system onto it.
Simple, works, people are happy that they are safe from bad china cams.
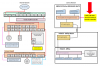
You already have a complex network with converters, multiple switches, 2.5G/10G etc.
To troubleshoot this is already difficult. You already saw it in your old thread.
If you dont use managed switches with webinterface its impossible to monitor a specific port. It will be always a pain in the ass to troubleshoot problems.
You always come to the point ... it is the converter? it is the camera ? it is switch XY ? a connector ? cable ? wifi bridge? cellular network ?
You will waste hours and days to test manually.
Looks like
@tech_junkie having fun with troubleshooting this
I dont even get your point.
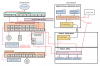
You already have 2 managed switches in your house. There is only one which is not. You simply get another 8 port like SG2210 connect it at the pole and you can use vlans if you want to seperate your cameras from your home network. You dont use vlans because
@tech_junkie dont like them ? aha. then just add wifi bridges and cellular connections.. oh boy!
You already have an advanced firewall, heck you can simply block the internet for the cameras if you are obsessed with the plan.
Why even did you bought the expensive network equipment at first when you now want to step back to a dumb network ?
Your provider may give you a dumb basic router for free. why even use omada stuff when you dont want to use most of the features ?
The majority simple connect everything to the internet, dont even think about all these things. Use alexa, share all their data with google, amazon and microsoft. dont give a shit.
There are even people using port forwarding.
What do you think will happen if you connect your camera to the internet ?
XI will watch you ?
Some weirdo will watch your driveway?
Someone hack into your network because you are so interesting like Taylor Swift?
I dont get it.
To my knowledge there are no proofs that ever happen somewhere

Keep it simple and think about how to troubleshoot problems in future.