Excuse the long rant; it's definitely on-topic and should be useful to someone.
I have a few OEM Hikvision cameras, model NP104-IR/4X, (equivalent to DS-2DE2A404IW-DE3), running on my home network since 2018. I happened upon the advisory of the latest Hikvision exploit/vulnerability last Friday while trying to add the cams to Home Assistant (
Hikvision) and promptly freaked-out. It was then that I started down the path of understanding the difference between Hikvision v. OEM Hikvision. OEM is equivalent to SOL (Sh*t Outta Luck) when it comes to getting any information (let alone support) on the cams from Hikvision. They wouldn't even tell me if the sun was out, let alone if the firmware version I was running was indeed vulnerable. After exhausting all options, I decided it had to be. I wish a simple command/test would have accompanied the advisory, some harmless command I could run against the cams that would confirm they were vulnerable, but I guess that would help the bad guys down the road to exploiting the vulnerabilities. Of course, the real bad guys would already be well down the exploiting road just hearing the vulnerability exists, but I understand the principle in not wanting to give them any help.
In searching I found the
latest firmware for my OEM camera, NP104-IR_4X_5.6.12_190807(.)dav; that would still be vulnerable to my understanding, but I decided to give it a try. All the cautions and warnings about flashing OEM cams with Hik firmware had me fearing flashing the cams with anything directly from Hik, but I also downloaded two firmware files that seemed like they would work with the DS-2DE2A404IW-DE3 models. I dusted off the Internet Explorer browser and logged into the cam GUI and attempted to upgrade the firmware through the Maintenance page. None of the .dav files would flash. Every upload attempt resulted in a "failed to get the upgrading process" error. A day of trials and tweaks resulted in nothing. I decided I had no choice but to risk bricking a cam (or turning it into a Chinese GUI) by going down the
TFTP route.
I tried the Hikvision TFTP server, had no luck (wouldn't complete the upload), so I gave the
GitHub - scottlamb/hikvision-tftpd: Unbrick a Hikvision device (NVR or camera) via TFTP script a try. Put the script on one of my Raspberry Pi 3+, issued the listed commands in the Terminal, restarted my cam and it worked like a charm! Well, I did have to run it/restart the cam several times when any of the uploads stalled, but it worked! I owe Scott Lamb a few beverages...
All three .dav files uploaded and the GUI never went Chinese, but there was a definite difference in picture quality/functionality. The
latest firmware for the NP104-IR/4X (5.6.12_190807) flashed fast (file is only 23MB) and picture quality/functionality didn't change. The .dav file I downloaded from the international Hik site was the latest version I could find, 5.7.1_211015, it was nearly double in size (46MB). It uploaded and the GUI was the same, but the picture from the cam was crazy; almost had a Matrix-like effect with cascading pixels/blocks and the IR lights also didn't seem to work. I then flashed the .dav I downloaded from us.hikvision DS-2DE2A404IW-DE3 product page (5.6.800_210628); it was the largest of the files (48MB). That installed correctly and
seems to have given me the same/better picture quality as the 5.6.12_190807 firmware. I haven't kicked the tires all the way around with it yet, but I think this is as good as it gets for now.
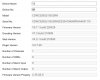
Here's the disconcerting thing with the installed firmware, when I check the System Settings,
it reports I'm running V5.6.12 build 190807 firmware (not 5.6.800_210628). I re-flashed multiple times, it never changed. I can only guess it's one of two things:
1) the 5.6.12_190807 firmware somehow locked the cam, so (even though it seems the firmware upgrade process worked) no subsequent firmware can install
2) the Hikvision programmer(s) neglected to change the version in the .dav file, so it's reporting the wrong version
....wait a minute, a third option just occurred to me:
3) they just copied/doubled the code in the 5.6.12_190807 firmware to make it look like they were taking action and released that (probably not, but maybe)
The Hikvision disclosure page (
Security Notification - Command Injection Vulnerability in Some Hikvision products) is confusing on whether or not (whatever) the firmware I'm running is vulnerable. On the positive side, the row for the DS-2DExxxx cams states "
Versions before (not include) V5.5.0 build xxxxxx " are vulnerable. That would be good, except that in the paragraph above the table it states "
Your device firmware is affected by this security vulnerability (CVE-2021-36260) if its version dated earlier than 210628. " 190807 being before 210628, I can only conclude after all of this, I am still running vulnerable firmware

If anybody has any tips on my situation or tests I can run to see if I'm still exploitable, I'd welcome them. I don't expose the cameras directly to the internet, but the VMS I use (Zoneminder) is accessable outside the LAN. I think that affords me some level of security against the exploit, but I still hate the idea of running two compromisable (that'll be an acceptable word to Webster's sooner or later) devices on my network.
“And I only am escaped alone to tell thee.”