This post is for Slugger who was asking me some questions.
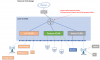
First, congrats on picking an enterprise switch, but also, good lucky on your learning journey. This just an example of how you might set it up. Most enterprises would choose a similar design rather than doing dual NICs.
Think of your 48-port switch as three 16 port switches as drawn in the diagram. Each VLAN is its own domain. One for IoT, one for cameras, and one for home. You can break up your switch into many smaller switches. It could be six 8-port switches. Or maybe a 5-port for IoT, 16-port for cameras, and the rest for Home.
The layer 3 switch allows it to route traffic between the VLANs (the smaller "virtual" switches). You also are able to create rules to filter traffic between VLANs. See my post here for an example of what kind of rules you might consider: Whitelist firewall settings for BlueIris
I'm not going to discuss the pros and cons of an enterprise switch, you can read that here: Switch choices....pros/cons of an Enterprise switch. A layer 3 managed switch is required.
These are the pros and cons of a VLAN design with inter-VLAN routing vs a dual NIC BlueIris design with separate switches.
Starting off with the Cons:
- more of a learning curve. Easier to understand physical switches than "virtual" switches.
Pros:
Arguments against:
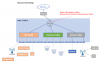
First, congrats on picking an enterprise switch, but also, good lucky on your learning journey. This just an example of how you might set it up. Most enterprises would choose a similar design rather than doing dual NICs.
Think of your 48-port switch as three 16 port switches as drawn in the diagram. Each VLAN is its own domain. One for IoT, one for cameras, and one for home. You can break up your switch into many smaller switches. It could be six 8-port switches. Or maybe a 5-port for IoT, 16-port for cameras, and the rest for Home.
The layer 3 switch allows it to route traffic between the VLANs (the smaller "virtual" switches). You also are able to create rules to filter traffic between VLANs. See my post here for an example of what kind of rules you might consider: Whitelist firewall settings for BlueIris
I'm not going to discuss the pros and cons of an enterprise switch, you can read that here: Switch choices....pros/cons of an Enterprise switch. A layer 3 managed switch is required.
These are the pros and cons of a VLAN design with inter-VLAN routing vs a dual NIC BlueIris design with separate switches.
Starting off with the Cons:
- more of a learning curve. Easier to understand physical switches than "virtual" switches.
Pros:
- more flexibility in terms of creating many switching domains.
- allows you to directly access and view cameras from home network. You don't have to RDP to BlueIris to access cameras. You can save screen captures directly. Recommend applying the appropriate ACLs to allow this to happen as well as block unwanted traffic to/from cameras.
- you don't have to physically touch a device to "move" it. You can change a device from VLAN to VLAN. Example: yesterday I added a new camera. My switch is in the basement but I have a drop in my office. I plugged in my Dahua into my wall jack, put that particular switch port to my "prep" VLAN. This prep VLAN is on the 192.168.1.x subnet. I'm able to connect to 192.168.1.108 from my laptop and change its IP to my camera VLAN. Then I connect to my switch and change that switch port to the camera VLAN and finish setting up my camera.
- allows you to do a dual IP design with one NIC (in this case you would trunk to your BI machine).
- allows you to trunk VLANs to Wireless APs. This way you can have an SSID per network. So you don't need a WAP per network. Cisco WAP config for dual VLAN/SSID example
- the switch can acts as your NTP and DHCP server.
Arguments against:
- one might say that a Con is no physical separation between the Camera VLAN and the Home VLAN. However VLAN separation is used in all Enterprises and Govt. In addition, you can employ security features such as 802.1x, mac filters, spoof guard, storm control, etc. Definitely apply the appropriate ACLs at a minimum.
- VLANs have no encryption. Technically this is true, but the only time you will see a VLAN tag is in a trunk interface. Most users will not use a trunk and my example below does not use any trunks. The switch ports that connect to your PC, router, and cameras are "access" ports. They will not have a VLAN tag and the end devices cannot hop to another VLAN. Also, with port security enabled, it even more secure.
- Someone could hack the switch. Yes, that is always a possibility, but along the same lines, someone could hack your BI machine. There are probably more vulnerabilities with Windows.
- you have a single point of failure with one switch. This is a different design discussion. A VLAN design does not restrict you to one switch. You can have a VLAN design with multiple switches trunked together.

Last edited: