Sorry for the late udpate. I wanted to give your suggestions a couple of days before I could verify what the issue was, and also we are on baby watch, so we've been spending a lot of time in the hospital.
It's the server port. I was getting login attempts from eastern Europe mostly. Changed it to 12345, per the recommendation of someone on this forum, and I've not had one since. If I recall the explanation, it's usually "bots" making these attempts and they usually go for common ports like 8000. Change it to something different (that still works) and it appears to thwart those bot attempts.
Fullboogie is the winner! I changed my NVR "Server Port" (no idea what this is for) to some random value and the login attempts have completely stopped. What still baffles me is that I have absolutely no rules on my router to allow port 8000 access to my NVR. Does the NVR even have a login interface at that port for these "bots" to even attempt a login? So strange to me.....
Just turning off UPnP won't (generally) disable any ports that already have been opened. Just turns it off from that point forward. Also check directly what ports are open on the router.
The ShieldsUp scanner won't necessarily pick up some odd port unless you specify it. I used to have another online scanner that would run a complete scan but it's paid now and don't find any that work well on a quick search. Might download one to run local directly against your router from outside.
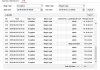
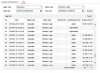
Mike, I have only two ports open most of the time, random ports for WOL and RDP, and since I never endabled UPnP, I have no routes created by it that currently exist. I disabled all of my routes (created by me) while testing, then just re-enabled those two for a few days ago and everything seem calm, so I don't think those are the issue. I did try hitting the NVR ports specifically using SheildsUp and they all came back as secure, so I don't know how these outside systems were able to get through to the NVR.
If you're getting connections to the service port then there has to be a route to that port.
Do you have hikconnect enabled?
If not then the only other way I think it's possible is if port 8000 is forwarded from your router to your nvr. Though those 192.x.x.x addresses that aren't part of your home network are strange.
Do you have any vpn set up? That's the ideal way to view cameras from outside your home network.
That's what I thought, but when I was testing this out, I had no routes enabled so it was techically locked down. Yes, I do have hikconnect enabled as that's how I was accessing my NVR using the HikConnect app. But when I disabled all of the NVR ports, I wasn't able to connect with the app anymore, but the login attempts were still happening until I changed the server port on the NVR.
Those other 192.168.11.x addresses are really freaking me out as they seem internal, but I never use .11, just .1
No, I haven't had the time to investigate how to set up a VPN, but I DO want to go down that router for security reasons, and I have read that I can use OpenVPN with DDWRT (which is what I have running on my router), so that is my plan in the future, but I'm not 100% sure I'll still be able to use apps like HikConnect over the VPN or not.
Found multiple hits for one of the IPs in your logs and it mentions port 8000 scanning - look here
51.38.36.213 | OVH SAS | AbuseIPDB
Is all of your network on 192.168.1.X ??
Yeah, everything on my network is using 192.168.1.x addresses, which thankfully rules out any hijacked system (though, I shut down all devices on my network and was still getting intrustion attempts, so that's not it), so I'm not sure how they're able to come from an address like 192.168.11.x.
It's not logical that there is no inbound access found for the external public IP address your PC is using for the relevant ports yet you still see inbound access attempts.
There are many ways in which common-brand routers can be compromised, to provide a 'foothold' in the local network.
Do you have 'Remote administration' enabled in the router?
You did power-cycle the router?
Are there any other ways in which your network is accessible from the internet?
Do you have any devices that are using a P2P (peer-to-peer) external access, or using torrents or similar, or using a VPN service to hide the network origin?
Do you have a NAS with a 'Cloud' facility enabled such as 'MyQNAPCloud' ?
That's what makes this so strange. Port 8000 is locked down, confirmed with ShieldsUp, but when I changed it, the attempts just stopped. I don't get it at all.
Do you have 'Remote administration' enabled in the router? Nope.
You did power-cycle the router? I have the router set up to reboot itself every couple of days.
Are there any other ways in which your network is accessible from the internet? No, just through my router.
Do you have any devices that are using a P2P (peer-to-peer) external access, or using torrents or similar, or using a VPN service to hide the network origin? No to both.
Do you have a NAS with a 'Cloud' facility enabled such as 'MyQNAPCloud' ? No NAS (just a windows file server, but not accessable remotely) or cloud services beyond Dropbox.
I wish I had more information to report back with that had a more satisfactory resolution, but it looks like it was just port 8000 which was magically accessable through my router that had no routes set up for that port.