You know, after been running win 7 forever, I just had to buy a new motherboard and cpu, cause of lightning. So, now I installed win 10 pro for the first time for personal use. It's not kind to my usual practices, and its driving me bonkers on adding the same intel addon nic card, that was working just fine before.
This new mobo has a second nic built in which I couldnt configure either.
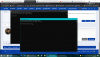
Using all the settings here above I cant connect to my cameras through the switch I have. I get errors in the network adapter.
I'm using 192.168.70.10 as my nic ip address. all my cams are 192.168.70.21 and above.
in the network settings:
one of the problems is DHCP is not enabled.
auto config - yes-
ip 192.168.70.10
subnet mask 255.255.255.0
default gateway either i leave blank or set to 192.168.70.254
dns server - 192.168.70.254
dns servers click on Netbios over tcpip - enabled
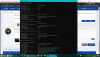
advanced:
IP settings:
one entry 192.168.10 - sbmask 255.255.255.0
def gateways Gateway - Metric automatic metric
DNS
192.168.70.254
checked - Append prim and ...
WINS
no addresses entered
checked enable lmhosts
netbios setting default
any insight ?
i checked win10 for card driver update, win says - its generic driver is OK < probably should check with intel though.
Win 7 was a breeze to set up..
This new mobo has a second nic built in which I couldnt configure either.
Using all the settings here above I cant connect to my cameras through the switch I have. I get errors in the network adapter.
I'm using 192.168.70.10 as my nic ip address. all my cams are 192.168.70.21 and above.
in the network settings:
one of the problems is DHCP is not enabled.
auto config - yes-
ip 192.168.70.10
subnet mask 255.255.255.0
default gateway either i leave blank or set to 192.168.70.254
dns server - 192.168.70.254
dns servers click on Netbios over tcpip - enabled
advanced:
IP settings:
one entry 192.168.10 - sbmask 255.255.255.0
def gateways Gateway - Metric automatic metric
DNS
192.168.70.254
checked - Append prim and ...
WINS
no addresses entered
checked enable lmhosts
netbios setting default
any insight ?
i checked win10 for card driver update, win says - its generic driver is OK < probably should check with intel though.
Win 7 was a breeze to set up..