duplo
Getting comfortable
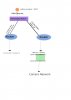
Looks good and easy, i like the way because its a mix out of vlan and physical seperation.
So you dont need to deal with firewall rules and it should be less problems with bandwidth limitations.
you should only use one 10G connection to the first switch and use it as trunk. dont see any reason using two physical connections to the router??
Because its omada you need at least one firewall rule
omada allows inter vlan traffic by default. you need to block this,
otherwise devices can communicate. also you could get crazy loops which can pull your whole network down, caused by the windows pc which can do both.
and the block cctv network from internet rule
So you dont need to deal with firewall rules and it should be less problems with bandwidth limitations.
you should only use one 10G connection to the first switch and use it as trunk. dont see any reason using two physical connections to the router??
Because its omada you need at least one firewall rule
omada allows inter vlan traffic by default. you need to block this,
otherwise devices can communicate. also you could get crazy loops which can pull your whole network down, caused by the windows pc which can do both.
and the block cctv network from internet rule
Last edited: