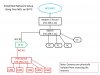
What you have shown above is a BI pc with only one NIC. If it has two, you are not showing the connections.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
IReallyLikePizza2
Known around here
Thanks, I've corrected below. So, just to make sure I’ve got it, please take a look at the REVISED network diagram below.
Please confirm that:
THANKS!
 .
.
Please confirm that:
- The BI PC can see all BLACK devices AND all RED devices
- ONLY the BI PC can see the RED devices
- The RED devices see ONLY the BI PC and each other.
- They RED devices can’t “phone home”.
- The BI PC can access the Internet
THANKS!
 .
.IReallyLikePizza2
Known around here
That will work, but you eventually "Trusting" the cameras that they won't talk on another subnet
Odds are they won't, but I wouldn't do it myself because I'm paranoid
Odds are they won't, but I wouldn't do it myself because I'm paranoid
That will work, but you eventually "Trusting" the cameras that they won't talk on another subnet
Odds are they won't, but I wouldn't do it myself because I'm paranoid
Thanks, but I'm not sure I follow. Can you please be more specific about your concern and how my proposed design introduces the issue?
IReallyLikePizza2
Known around here
Thanks, but I'm not sure I follow. Can you please be more specific about your concern and how my proposed design introduces the issue?
They are in the same broadcast domain and there is no firewalling, so there is nothing stopping from the camera talking to anything else on the network even though its not in the same subnet
It could send out broadcast traffic, and it would hit everything. If a camera were compromised, it could easily access everything else on the network
So, if I'm understanding you correctly, in the network example you provided, the cams all hang off the same switch directly attached to the BIPC, so the cameras are are, in effect, "quarantined" there. Whereas in my example, the cams are distributed around the network and not "quarantined" ??
The physical location of my cams forces me into a network design like the one I provided. I physically can't get the cams to all connect to a single switch that, itself, is only connected to the BIPC. For this reason, is my situation a better candidate for VLAN?
The physical location of my cams forces me into a network design like the one I provided. I physically can't get the cams to all connect to a single switch that, itself, is only connected to the BIPC. For this reason, is my situation a better candidate for VLAN?
NVR990, your situation would be a good application for VLAN. I have a similar situation with 30 cameras scattered across main lines . I implemented 3 VLANS and now my cameras are isolated from the internet. I had to replace some switches that didn’t support VLAN. I struggled with the concepts but got it working and all my devices are on the same subnet( makes book keeping easy) ( others don’t recommend) but different VLANS. I’m using 3 nic in my BI.
It is simplilist to understand one vendors implimentation of VLAN as they use different terminology . I had Netgear switches and stayed with them.
It is simplilist to understand one vendors implimentation of VLAN as they use different terminology . I had Netgear switches and stayed with them.
Each cam is physically connected to the internet. Why bother with two NICs in the PC if they are not on separate wired networks?
If you physically cannot change the wiring, then replace the two POE switches with managed POE switches and set up VLANS.
If you physically cannot change the wiring, then replace the two POE switches with managed POE switches and set up VLANS.
Each cam is physically connected to the internet. Why bother with two NICs in the PC if they are not on separate wired networks?
If you physically cannot change the wiring, then replace the two POE switches with managed POE switches and set up VLANS.
The cams are on a different subnet than the router/gateway, so how can they see the Internet?
IReallyLikePizza2
Known around here
In an ideal world, they won't. However the whole reason for segregating them is because Chinese network devices cannot be trusted
Technically, there is nothing stopping them from sneakily accessing the rest of the network
Technically, there is nothing stopping them from sneakily accessing the rest of the network
They are physically connected. Your router will rout to them. That is what routers do. Nothing is stopping any outside connection from seeing them either.
Nothing is stopping any outside connection from seeing them either.
Not sure I follow. What do you mean by the above?
Last edited:
kickstart24
Young grasshopper
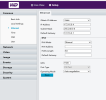
For the guide on page 1, is there a reason 192.168.1.50 is added in the windows network settings?
SpacemanSpiff
Known around here
Based on the example, the machine's network interface is primarily configured to use the 192.168.55.x network. The default IP address of dahua cams is 192.168.1.108. The 192.168.1.50 IP is bound to the network adapter as a secondary IP address in that step for convenience. Binding that secondary IP will allow that machine access to any new cams plugged in without having to change the machines IP scheme to 192.168.1.x, then switch it back once the new cam is configured.
kickstart24
Young grasshopper
Thanks. Makes sense !Based on the example, the machine's network interface is primarily configured to use the 192.168.55.x network. The default IP address of dahua cams is 192.168.1.108. The 192.168.1.50 IP is bound to the network adapter as a secondary IP address in that step for convenience. Binding that secondary IP will allow that machine access to any new cams plugged in without having to change the machines IP scheme to 192.168.1.x, then switch it back once the new cam is configured.
should_have
Young grasshopper
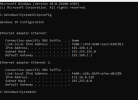
OK folks, I know google is your friend and it’s great. Unfortunately, I’m at my wits end. Can someone help me into setting up my IP Adress for my NVR so I can use the 2nd NIC Card I installed.
After fiddling with one of my cameras. I can get my Camera/GUI to work/appear on my screen via NIC 2. Earlier today it took me too long to get my NVR to recognize my camera back after fiddling with the settings via NVR.
I can get Blue Iris to work in NIC_1 as long as I have the Network Feed and my NVR going through a splitter. If I put my NVR only to NIC_1, I can't reach the GUI for the NVR! I can get the NVR's GUI when I tie the network and NVR through a switch.
Below are some screen shots of my NVR, Cameras & NIC.
SORRY, I'm exhausted. I'm thinking I worked to hard today to attempt to set-up VPN via OpenVPN
Or should I start a new Post ???
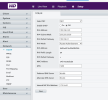
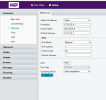
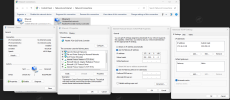
After fiddling with one of my cameras. I can get my Camera/GUI to work/appear on my screen via NIC 2. Earlier today it took me too long to get my NVR to recognize my camera back after fiddling with the settings via NVR.
I can get Blue Iris to work in NIC_1 as long as I have the Network Feed and my NVR going through a splitter. If I put my NVR only to NIC_1, I can't reach the GUI for the NVR! I can get the NVR's GUI when I tie the network and NVR through a switch.
Below are some screen shots of my NVR, Cameras & NIC.
SORRY, I'm exhausted. I'm thinking I worked to hard today to attempt to set-up VPN via OpenVPN
Or should I start a new Post ???




should_have
Young grasshopper
SpacemanSpiff
Known around here
OK folks, I know google is your friend and it’s great. Unfortunately, I’m at my wits end. Can someone help me into setting up my IP Adress for my NVR so I can use the 2nd NIC Card I installed.
After fiddling with one of my cameras. I can get my Camera/GUI to work/appear on my screen via NIC 2. Earlier today it took me too long to get my NVR to recognize my camera back after fiddling with the settings via NVR.
I can get Blue Iris to work in NIC_1 as long as I have the Network Feed and my NVR going through a splitter. If I put my NVR only to NIC_1, I can't reach the GUI for the NVR! I can get the NVR's GUI when I tie the network and NVR through a switch.
Below are some screen shots of my NVR, Cameras & NIC.
SORRY, I'm exhausted. I'm thinking I worked to hard today to attempt to set-up VPN via OpenVPN
Or should I start a new Post ???
View attachment 222903View attachment 222904
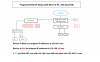
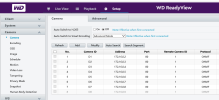
Camera D3 is assigned the same IP addresss (172.16.0.4) as the IP address defined in Setup --> Common --> Ethernet
You cannot have an IP address assigned to more than one device on a network. This is most likely the cause of the latency you described.
I recommend leaving the camera IP's as they are, and change the other value
Last edited: