I have a 16 channel HIKVision camera, with virtual host enabled.
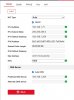
If I want to access a camera directly through a web browser, I can access like this:
Just the IP address of the NVR and port to connect to. I can configure camera settings, view the live stream via the browser etc. etc.
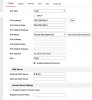
I use iVMS software on my PC or tablets to stream footage. I configure them to talk directly to the NVR and get the stream just fine.
However, is it possible to connect directly to the camera and access the video streams? Rather than connecting to the NVR, I would like to access the cameras directly via the virtual host feature? Can that be done? I have tried a couple of different ways in iVMS but have not had any luck.
If I want to access a camera directly through a web browser, I can access like this:
Just the IP address of the NVR and port to connect to. I can configure camera settings, view the live stream via the browser etc. etc.
I use iVMS software on my PC or tablets to stream footage. I configure them to talk directly to the NVR and get the stream just fine.
However, is it possible to connect directly to the camera and access the video streams? Rather than connecting to the NVR, I would like to access the cameras directly via the virtual host feature? Can that be done? I have tried a couple of different ways in iVMS but have not had any luck.