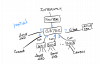
I am going to setup the VLANS where i can with an existing gs724 (supports trunkline) One example: 5 cameras and a Kohler generator on remote switch with one line coming to VLAN switch. Kohler needs to see the internet to report its status. I can add a ~$400 router and get a trunk line and setup two PVIDs etc. I am looking for a way to isolate and keep functionality. Moving generator to wireless is possible but WiFi signal is bad there and yet improving signal is another possible option. I need 3 more Trunkline routers to keep existing functionality. So looking at next best options for the other locations.
Rules seem ok too, But understanding example below?
Rules Like using the deny list with camera ip(175) and router or access list with camera and BI server? Seems right but allow only one port ? 554? port range seems to only take one number??
Thanks for your patience!
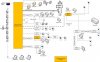
View attachment 181757
A detailed networking diagram of all devices (router, switches, hosts, cameras, etc) is in order. If you don't have one, make one; you'll need it to create and maintain the VLAN network you're working towards implementing.
I'd highly recommend NOT to use Wi-Fi for anything other than a tablet or phone.
To minimize additional purchases, attempt to consolidate "like" devices onto single switches. If not possible, then it may require (re) stringing network cable or perhaps additional costs (switches) is inevitable. That does not mean that L2 (VLAN) switches are required. A port on the current GS752 can be assigned to a VLAN as UNTAGGED. A switch connected to that particular port will be servicing that VLAN to all devices connected to it. (this is where a picture is worth a thousand words, also helps in network re-design of current environment)
An ASUS router (as by the attachment) you can block outbound devices, up to 32 entries. First ensure you have enabled this feature

Using the Filter Table, one IP at a time enter
Source IP <camera IP>
Port Range <leave blank>
Destination IP <leave blank>
Port Range <leave blank>
Protocol <BOTH> ( i think this is an option )
Click the + to ADD the entry
Repeat for all camera IPs. Leaving the field blank is a "wildcard" blocking this IP from exiting the local LAN; i.e. no internet access. Access to the device (camera or other) is still available on the local Network.
Another method and actually simpler, when the IP is already in use on the LAN, is to block internet access with a single click.
From the login page; NETWORK MAP
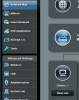
Click on VIEW LIST and the following screen will appear

The Globe Icon is a toggle on/off for internet access. Click once will disable internet access for that device. Click again and it will allow internet access.
---
Side-note/Off-topic
If you haven't already looked into ASUS-Merlin, it's worth a few minutes to do so. It is a replacement firmware for most ASUS routers and if you have a supported router I'd recommend downloading and installing it. It has the same look-feel as stock firmware with MANY additional features and functions. There are many articles on the author who has ties to ASUS as they share improvements/upgrades between the Vendor firmware version and ASUS-Merlin.
Use this forum for posts about all versions of this alternative firmware for ASUS wireless routers

www.snbforums.com