Only a couple of these questions are 'general' networking ones. Others are very specific to you hardware and network address assignments.
does the default gateway mean anything on the cameras on a subnet?
No.
If possible don't defined any address as the GW. If one is needed, enter a totally fictional one (within the private IP ranges).
All devices within a specified subnet can 'find' each other without a need of a GW; a GW provides access to another network router to which multiple networks are connected.
My router no longer sees the ip addresses on the VLAN s that are not 1. Is that right?
VLAN ID1 is the standard default for VLAN capable devices. Whenever possible VLAN ID1 is removed from network devices as other VLANs are added to an environment. (this would remove the typical connect and forget to hosts, clients, and network appliances. making it impossible for an unknown device being added and having connectivity to some part or all of the network it was connected into)
If new VLANs have not been added to the port which is connected to the router, then Yes this is correct. (that is the purpose of VLANs, not letting one network 'see' another network unless defined.
However, simply adding other VLANs to the router-port will not magically work. The router must be able to understand the multiple Network Address (192.168.13.#/24, 192.168.11.#/24, etc) being delivered to it.
Which of the methods are you using to connect your environment to the internet; L3 Switch (GS752), L3 Router (AX92U), or other L3 device?
I would use that display list for seeing who is connected and getting MAC addresses etc.
Who is connecting to what?
How is WHO connecting to what?
Should i be the last switch before internet? or just who cares number?
Don't follow/understand the question... who/which is "i"?
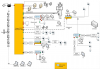
The order of connection is as you've configured in the diagram:
<internet> === <ISP Modem> === <AX92U> === <GS752> === <other switches>
AX92U is your multi-purpose device; Firewall, Switch, VPN, DHCP,
DDNS, etc. It MUST be the first device in your network (unless you have another Firewall appliance)
For maintenance , I thought of using an old router plugged into each VLAN (4) .. On only when doing maintenance with a wireless connection to the router. Then , I think, i could see all the ip addresses from the cameras.
Trying to decipher statement;
old-router plugged into VLAN ID14 (on switch port of GS752)
client device connected via Wi-Fi to old-router
all of the VLAN ip addresses would be present on the 'connection', though the client would only connect to one IP Network at a time via manual address configuration on client device with port set as UNTAGGED.
================
Your ideas need to be confirmed via experimentation, as you are already doing. A lot has changed in the VLAN environment as "smart" enhancements from when I was exposed to the typical configurations. I can't tell you, for sure, if what you're stating is possible or not without fully understanding your hardware, environment, requirements, and configuration.
Again, you're at the point where only you can continue to implement and see what does or does not work.