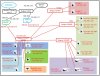
I am really struggling with this setup. I wanted to use a Ubiquiti Flex Switch so I would only need to run one ethernet to my attic. I wanted to terminate the ethernet from my basement switch to a 2nd switch w POE injector to the Flex switch in the attic and then run wires to the outdoor cams.
However with the "dual nic" setup, I can't get my Unifi Flex Switch Online. My "second" switch has 1 ethernet going from the switch to the BI PC. The 2nd ethernet goes into a POE injector then into the Flex switch and onto the camera.
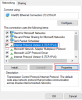
The problem is since the Flex switch is coming off the 2nd switch (not hooked into the primary switch with router/internet access), it can never get an IP. I am unable to log into the GUI of the flex switch because it can't get to the router to get an IP. Unfortunately if I can't manage the switch, I cant get it to power the cam. Is there any workaround for this or do I just have to get rid of the flex switch and buy an unmanaged POE? I really want to use the flex switch so I can run less wires but I just can't figure this out and am extremely frusterated.
However with the "dual nic" setup, I can't get my Unifi Flex Switch Online. My "second" switch has 1 ethernet going from the switch to the BI PC. The 2nd ethernet goes into a POE injector then into the Flex switch and onto the camera.
The problem is since the Flex switch is coming off the 2nd switch (not hooked into the primary switch with router/internet access), it can never get an IP. I am unable to log into the GUI of the flex switch because it can't get to the router to get an IP. Unfortunately if I can't manage the switch, I cant get it to power the cam. Is there any workaround for this or do I just have to get rid of the flex switch and buy an unmanaged POE? I really want to use the flex switch so I can run less wires but I just can't figure this out and am extremely frusterated.