Use 'help' to find what commands are available.
They vary a lot with the model and date of the NVR.
What do you need to do / what problem needs to be solved?
I want to run command of os or /bin/sh. and I do along GUI.
* run go -> load sec.bin on memory as picture 0x81fffa90. after run command
* go 0x81fffa90 (comand is not hapenning any thing...)
What u-boot version are you using?
What camera are you trying to use sec.bin on ?
Info uboot version and command:
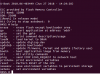
and I dump Nand 128MB to find key unpack firmware. I have use Pi3(raberry) connect pin of chip nand flash but seam as it only data of app (not sure).
Info Cam Hikvision DS-2CD2X21G0.
I dump 128MB from chip flash winbond W25N01xxIG. but i don't know where key was save.
I have alot infomations from chipflash:
strings file_flash_dump :
....
The length of key must be less than or equal to 16!
Error! efuse write key time out!
Error! efuse load key out!
%s,%d: invalid key len 0x%x.
%s,%d: Hmac key initial failed!
%s,%d: hash i_key_pad and message start failed!
%s,%d: hash i_key_pad and message update failed!
%s,%d: Hash Final i_key_pad+message failure, ret=%d
,%d: Hash Init o_key_pad+hash_sum_1 failure, ret=%d
%s,%d: Hash Update o_key_pad failure, ret=%d
%s,%d: Hash Final o_key_pad+hash_sum_1 failure, ret=%d
%s,%d: RSA padding mode error, mode = 0x%x. public key encryption operation, the block type shall be 02.
%s,%d: For a private key decryption operation, the block type shall be 02.
%s,%d: key is null.
%s,%d: For a private- key encryption operation, the block type shall be 00 or 01.
%s,%d: For a public key decryption operation, the block type shall be 00 or 01
....
I know partitions:
SPI Nand ID Table Version 2.4
[ 1.602149] SPI Nand(cs 0) ID: 0xef 0xaa 0x21
[ 1.606622] nand: device found, Manufacturer ID: 0xef, Chip ID: 0xaa
[ 1.612980] nand: Winbond W25N01GV
[ 1.616460] nand: 128MiB, SLC, page size: 2048
[ 1.620901] Nand(Auto): OOB:64B ECC:4bit/512
[ 1.625111] nand: ECC provided by Flash Memory Controller
[ 1.630824] Creating 14 MTD partitions on "hinand":
[ 1.635761] 0x000000000000-0x000000100000 : "bld"
[ 1.642993] 0x000000100000-0x000000180000 : "env"
[ 1.649935] 0x000000180000-0x000000200000 : "enc"
[ 1.657018] 0x000000200000-0x000000280000 : "sysflg"
[ 1.664148] 0x000000280000-0x000000380000 : "dpt"
[ 1.671242] 0x000000380000-0x000000b80000 : "rcvy"
[ 1.681896] 0x000000b80000-0x000001380000 : "sys0"
[ 1.692478] 0x000001380000-0x000001b80000 : "sys1"
[ 1.703118] 0x000001b80000-0x000003d80000 : "app0"
[ 1.727432] 0x000003d80000-0x000005f80000 : "app1"
[ 1.752781] 0x000005f80000-0x000006580000 : "cfg0"
[ 1.764507] 0x000006580000-0x000006b80000 : "cfg1"
[ 1.775091] 0x000006b80000-0x000007780000 : "syslog"
[ 1.788864] 0x000007780000-0x000007f80000 : "resv"
Can you help me unpack Firmware
"E3 platform"
Nand flash w25n01xxIG -
file_dump
