Thank you wery much...If your users are having botnet add user names to their cams or NVRs, then the problem is not the cams or NVRs. It is the (lake of) firewall/modem/router that is letting them in
And thank you for your read fully my message at all
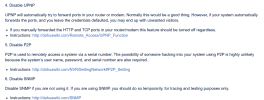
I don't use port forwarding.
It was these tips of yours that really helped in solving the problem described.The process of adding a new hacked user was found in the logs:
A connection was made using p2p without a user name but with administrator rights.
After that, a new user was added
But if I answer you seriously: I can advise you to check each of your cameras for hacking just in case
I really hope that YOUR vpn and firewalls helped you
I have video surveillance networks with different numbers of cameras
In some networks there are 3-5 of them, in other networks there are 500-600 of them.
Not all of them are hacked.
But it is enough if in a network of 300 cameras there are 10-15 hacked