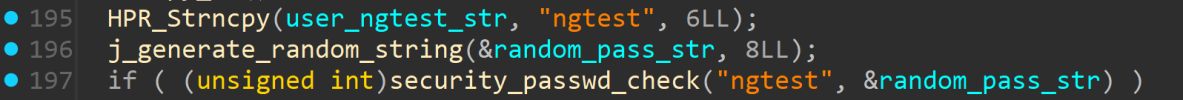
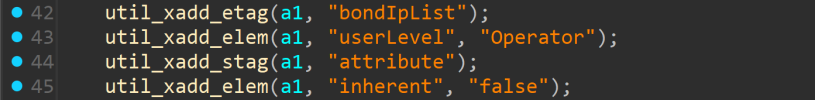
I have a DS-7616NXI-I2/16P/S NVR with firmware V5.04.066 build 250620 (latest).
I have connected multiple Hikvision camera's through LAN and PoE.
When i go to the webinterface of the "NVR->Device Access->Device->Video Device->Operation->Go" to manage the camera itself through the NVR it creates a user called "ngtest" on the camera. When you close the window the user remains on the camera. It does this on any Hikvision camera (LAN and PoE).
It is possible to remove the user on the camera directly but when you use the "Operation" option on the NVR the user gets created again. It is not possible to remove the user from the camera when you use the Operation function from the NVR. It's impossible to remove the user within camera's that are connected through the PoE ports of the NVR itself.
When you manually create the "ngtest" user on the camera as a normal user with any permission, and afterwards manage it through the Operation function from the NVR the user gets overwritten and gets all the permissions that you can see on the screenshot below. After you manage the camera throughe NVR you cannot log in with the "ngtest" user, even when you change the password of that users on the camera itself.
Here are some screenshots (some in dutch) but you can see whats happening. The users also pops-up in the online user list from the camera itself.
The front windows is the pop-up window when you manage a the camera from the NVR (it's the camera that you manage) .255 is the IP of the NVR, The window behind it (dutch) is the webinterface directly from the camera itself, showing the created users and the local admin.
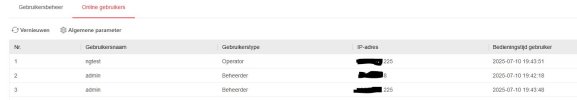
This is the online users list when accessing the camera directly, it is showing the "ngtest" user as "online".
These are the permissions the user has on the camera itself:

I find this disturbing and cannot find any documentation of this "feauture". This shouldn't happen and in my opinion is a security issue. Especially when the camera is accessible from the internet.
Somebody familiar with this?
PS: i already informed Hikvision support, but haven't got an response jet.
I have connected multiple Hikvision camera's through LAN and PoE.
When i go to the webinterface of the "NVR->Device Access->Device->Video Device->Operation->Go" to manage the camera itself through the NVR it creates a user called "ngtest" on the camera. When you close the window the user remains on the camera. It does this on any Hikvision camera (LAN and PoE).
It is possible to remove the user on the camera directly but when you use the "Operation" option on the NVR the user gets created again. It is not possible to remove the user from the camera when you use the Operation function from the NVR. It's impossible to remove the user within camera's that are connected through the PoE ports of the NVR itself.
When you manually create the "ngtest" user on the camera as a normal user with any permission, and afterwards manage it through the Operation function from the NVR the user gets overwritten and gets all the permissions that you can see on the screenshot below. After you manage the camera throughe NVR you cannot log in with the "ngtest" user, even when you change the password of that users on the camera itself.
Here are some screenshots (some in dutch) but you can see whats happening. The users also pops-up in the online user list from the camera itself.
The front windows is the pop-up window when you manage a the camera from the NVR (it's the camera that you manage) .255 is the IP of the NVR, The window behind it (dutch) is the webinterface directly from the camera itself, showing the created users and the local admin.

This is the online users list when accessing the camera directly, it is showing the "ngtest" user as "online".

These are the permissions the user has on the camera itself:

I find this disturbing and cannot find any documentation of this "feauture". This shouldn't happen and in my opinion is a security issue. Especially when the camera is accessible from the internet.
Somebody familiar with this?
PS: i already informed Hikvision support, but haven't got an response jet.
Last edited: