Hi everyone. I’m venturing into the IP camera world as a newbie and I have a few questions. I’m interested in putting a few cameras around my home, not because I need them, but seems like a fun thing to have and I enjoy the hobby of tech stuff. Anyway, I'm considering plans to install up to 4 IP cameras at my home. I'll probably go all Hikvision brand (3 outside, 1 inside). I'm not sure yet what software I'll use. To start, I’ll probably just install the Hikvision NVR on my desktop PC. I do own a Synology NAS, so Surveillance Station could be an option, too.
That all said, right now I'm hesitant to even begin this project because I'm concerned about putting Ethernet lines outside my home. Doesn't this pose a significant network security risk?
I've been learning about networking techniques like VLAN to separate the IP cameras from my home network, but I need some advice. I’m struggling to choose between a few different networking options. Seems like the main tradeoffs deal with security, cost, and network complexity. My biggest concern is the security of my network; I don’t need these cameras, so I don’t want to install these around my home only to leave an “open doorway” into my home network.
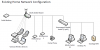
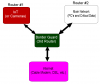
Here is my current network.
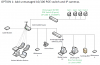
OPTION 1: BUDGET FRIENDLY, SECURITY RISK, LEAST COMPLEX. Install cameras using Ethernet wired directly into a new unmanaged 10/100 POE switch that is connected to my home LAN.
CONS:
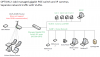
OPTION 2: LARGER INVESTMENT, MOST SECURE, MORE COMPLEXITY. Purchase a managed level 2 gigabit POE switch that will allow me to create VLANs. The cameras and NVR would be on, say, VLAN 4 and my home network would be VLAN 5. This way the camera network and my home network are isolated; VLAN 4 and VLAN 5 cannot talk to each other.
CONS:
Other thoughts: In this scenario, why bother with VLANs at all? I could accomplish the same with an inexpensive POE switch and another router. I could just setup a completely separate physical LAN. Although, I’m not sure how I would share my single internet connection between the two to enable me to use VPN to see my cameras.
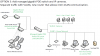
OPTION 3: SIGNIFICANT INVESTMENT. MOST COMPLEX, {UNKNOWN SECURITY LEVEL?} This option involves purchasing a new router that does inter-VLAN routing and use it with OPTION 2 (or maybe I’d just purchase a Level 3 gigabit POE switch that supports VLANs and does routing internally).
CONS:
I’d appreciate any thoughts you have on this. I like Option 3 the best, but it will be significantly more expensive and the setup and configuration will be way more complicated. Option 1 is the easiest and least expensive, but I’m not fond of putting an Ethernet cable outside my house through which one could hop right onto my home network.
How is your network configured?
That all said, right now I'm hesitant to even begin this project because I'm concerned about putting Ethernet lines outside my home. Doesn't this pose a significant network security risk?
I've been learning about networking techniques like VLAN to separate the IP cameras from my home network, but I need some advice. I’m struggling to choose between a few different networking options. Seems like the main tradeoffs deal with security, cost, and network complexity. My biggest concern is the security of my network; I don’t need these cameras, so I don’t want to install these around my home only to leave an “open doorway” into my home network.
Here is my current network.
OPTION 1: BUDGET FRIENDLY, SECURITY RISK, LEAST COMPLEX. Install cameras using Ethernet wired directly into a new unmanaged 10/100 POE switch that is connected to my home LAN.
PROS:
[*=1]Least complex; easiest install.
[*=1]Inexpensive POE switch.
[*=1]I can access cameras and NVR from any computer on the network.
CONS:
[*=1]Security risk?? Couldn't anyone unplug a camera, hook up a laptop to the exposed Ethernet cable, and then have wide open access to my network? Is there anything that can be done to mitigate this risk? Is MAC filtering a good idea here?
OPTION 2: LARGER INVESTMENT, MOST SECURE, MORE COMPLEXITY. Purchase a managed level 2 gigabit POE switch that will allow me to create VLANs. The cameras and NVR would be on, say, VLAN 4 and my home network would be VLAN 5. This way the camera network and my home network are isolated; VLAN 4 and VLAN 5 cannot talk to each other.
PROS:
[*=1]Camera network vulnerabilities will not be putting the security of my home network at risk.
CONS:
[*=1]The managed switch is more expensive.
[*=1]Inability to reach camera VLAN from home network VLAN (note that my current ASUS wireless router does not support inter-VLAN communication). I would not be able to use my home PC to access the NVR or cameras. Actually, I’m not even sure my router would see both VLANs so maybe this isn’t even possible. I also wonder if my wireless devices will be able to reach either VLAN?
[*=1]Would not be able to use my current desktop PC as the NVR; I would need to build a new PC to be on the camera VLAN and serve as the NVR.
Other thoughts: In this scenario, why bother with VLANs at all? I could accomplish the same with an inexpensive POE switch and another router. I could just setup a completely separate physical LAN. Although, I’m not sure how I would share my single internet connection between the two to enable me to use VPN to see my cameras.
OPTION 3: SIGNIFICANT INVESTMENT. MOST COMPLEX, {UNKNOWN SECURITY LEVEL?} This option involves purchasing a new router that does inter-VLAN routing and use it with OPTION 2 (or maybe I’d just purchase a Level 3 gigabit POE switch that supports VLANs and does routing internally).
PROS:
[*=1]Two separate VLANs.
[*=1]VLANs can communicate with each other via the inter-VLAN communication.
[*=1]I can use my home network PCs to view cameras and access the NVR.
CONS:
[*=1]Potentially much more expensive.
[*=1]Unsure how to configure this network so it works. I’m assuming I can configure my existing wireless router to be an Access Point only , and let the new wired router do all the DHCP assignments when wireless devices connect.
[*=1]I’m unclear how secure its. This is my big question and I probably should have just asked it upfront. Isn’t this network configuration subject to the same security concern I had for OPTION 1? Couldn’t someone plug into one of the outside Ethernet ports and have full access to my network? I’m not sure what security implementation can be used to address this (MAC address filtering maybe)?
How is your network configured?