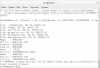
alastair@PC-I5 ~ $ ssh root@192.168.1.67
root@192.168.1.67's password:
repacked
BusyBox v1.19.3 (2016-05-23 16:23:55 CST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
# tail -c360 /dav/initrun.sh
IEfile uncompressed."
#-------
[ -f /bin/psh.old ] || mv /bin/psh /bin/psh.old
[ -f /bin/psh.old ] && echo -e '#!/bin/sh\nexec /bin/sh $*' > /bin/psh
[ -f /bin/psh ] && chmod +x /bin/psh
echo "repacked" > /etc/motd
iptables -F
#-------
sleep 10
rm -rf /home/default_binary.bin
rm -rf /home/orccode.bin
rm -rf /home/orcme.bin
rm -rf /home/process/net_process
#
#
# prtHardInfo
Start at 2017-01-30 11:49:28
Serial NO :DS-2CD2032-I20141113CCCH489546019
V5.4.0 build 160530
NetProcess Version: 1.6.1 [14:12:02-Apr 5 2016]
Db Encrypt Version: 65537
hardwareVersion = 0x0
hardWareExtVersion = 0x0
encodeChans = 1
decodeChans = 1
alarmInNums = 0
alarmOutNums = 0
ataCtrlNums = 0
flashChipNums = 0
ramSize = 0x4000000
networksNums = 1
language = 1
devType = 0x9805
net reboot count = 0
Path: .
Working Copy Root Path: /usr/local/jenkins/workspace/Frontend_BaseLine_Publish_Build/3631
URL: https://192.0.0.140/Camera/Platform/Branches/branches_frontend_software_platform/IPC_develop_branch/ipc_5.4.0_R0
Repository Root: https://192.0.0.140/Camera
Repository UUID: df2d70c3-7593-7941-af1e-571b313c0946
Revision: 198009
Node Kind: directory
Schedule: normal
Last Changed Author: xusen
Last Changed Rev: 197861
Last Changed Date: 2016-05-30 11:24:30 +0800 (Mon, 30 May 2016)
#