I had 3 IP cams that I ordered from Amazon - no name knock offs it appears - can't seem to find any 'brand' name anywhere. I had two of them installed and working just great. Then I made the mistake of checking their status - lo and behold it mentioned that there was an 'update' available to the software and I was foolish enough to believe that it would work. Over the Air update - sure, great chance of success! Luckily I only did one of the cameras. It got about half way thru the process and then just sat there …. after about 30 minutes I cancelled the process and sure enough -- the camera is bricked. Couldn't even see it on the network anymore. Luckily I had the third camera available and was able to use it to replace the dead one. But now I have a camera that is hooped unless I can breathe some life back into it.
As I said, it is not a brand name - it's a LOOKCCTV 2MP POE IP Camera made in China. Does what I need to monitor the home area while away on vacation and provide that little bit of visible security to the house. I have tried various steps to see if I can even connect to the cam again but SADP does not show it on the network (PC to stand alone router with IP of 192.0.0.128 and connected cam using separate power), TFTP does nothing since camera does not talk. Wondering whether try to use USB-TTY connect would accomplish anything?
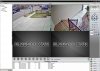
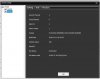
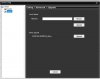
I have attached a couple of pics and am hoping someone might be able to point me in the right direction as to where I would connect to? I'm thinking the three 'copper' connections on the left side might be the power, TX and RX points - one is square and the other two are rounded - 1=power, 2=RX/TX?, 3=RX/TX? Of course once I get connected it might be all in vain if the camera is really bricked …. but what do I have to lose except time (retired) and maybe a few more strands of hair.
Appreciate any and all help … and remember, this PENSIONER is just trying to save money and these cameras did work well before I tried to update … lesson learned! Here's the pics ….
As I said, it is not a brand name - it's a LOOKCCTV 2MP POE IP Camera made in China. Does what I need to monitor the home area while away on vacation and provide that little bit of visible security to the house. I have tried various steps to see if I can even connect to the cam again but SADP does not show it on the network (PC to stand alone router with IP of 192.0.0.128 and connected cam using separate power), TFTP does nothing since camera does not talk. Wondering whether try to use USB-TTY connect would accomplish anything?
I have attached a couple of pics and am hoping someone might be able to point me in the right direction as to where I would connect to? I'm thinking the three 'copper' connections on the left side might be the power, TX and RX points - one is square and the other two are rounded - 1=power, 2=RX/TX?, 3=RX/TX? Of course once I get connected it might be all in vain if the camera is really bricked …. but what do I have to lose except time (retired) and maybe a few more strands of hair.
Appreciate any and all help … and remember, this PENSIONER is just trying to save money and these cameras did work well before I tried to update … lesson learned! Here's the pics ….