@Sybertiger I support the KISS network layout like you have, recommend it all the time here, it’s the best for someone that wants things to work and doesn’t want a bunch of security problems! I don’t recommend pfSense for any newbie in networking (recommend against it in fact), the ASUS routers have all the basics covered and continue to get regular updates which addresses the main issue (security).
For me I like to tinker, and 3 years ago I was getting a 1Gbps fiberlink to the house and wanted to make the most of it, and the “recommended” hardware was the ASUS ROG AC5300 (> $300). I needed a device that could be both an OpenVPN server and OpenVPN client (to establish a remote connection to a house in another state that had cameras)
simultaneously. I wanted to experiment with security cameras but (at the time didn’t think of how dual-NIC would address those concerns). I wanted to learn about deep packet inspection. PfSense seemed like the perfect opportunity to tinker and get all those things (and built an SFX PC for about $450, but should have just bought a used one tbh). The learning curve for with only basic networking is a little steep, but I’m in IT and had an interest so that wasn’t really a downside.
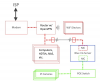
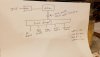
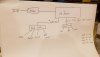
Fast forward, and now I have multiple wireless SSIDs (IOT, Guest, Primary) so I can have all the devices separated (IOT-untrusted no internet, Guest-untrusted w/Internet capped, Primary-trusted+internet uncapped) - but can allow firewall connections when necessary (like for IOT devices to talk to devices elsewhere on the network). When a new guest moves In (think rental/AirBnB), I can provide/change that password without changing any of the 30 other primary network devices (Chromecast, SmartTV etc). I don’t really trust security of Smart TVs and definitely not the DirecTV receivers but they all need internet access, so segregating them was possible this way. In the near future, with VLANs & in-wall AP+2 ports I can put all the Guest network ports and the Guest wireless on the same VLAN so the wired and wireless devices can interact and still be segregated from my stuff.
It’s full fledged overkill, but it’s also enterprise capable so literally anything I would want to experiment with, the pfSense box would let me try it out.....possibly to my own demise. My only wish is that it integrated with the Unifi equipment I’ve started to install.