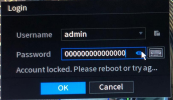
They have probably got in via the backdoor and that is why they logins look to be local.
We had someone here about 6 months ago with a similar issue with a Hikvision NVR and they thought they were being attempted to be hacked by someone within their house that they didn't give access to. It ended up being a backdoor vulernability.
I am after finding this backdoor so that I can fix it with perimeter security if the code itself is vulnerable- any info would be of help