Hi,
New to this forum,
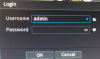
I own a Dahua DHI-NVR5216-16P-4KS2E [V4.001.0000006.0, Build Date: 2021-02-08 ]and recently noted a long beep from the system, never heard such beep before, looked at the system log and noticed 5 failed login attempts and again after few minutes heard same long beep and this time was looking at the monitor console (connected to console port of NVR) and noted someone was attempting to login and could see characters being entered on the login dialog box's password text field. (refer image)
Seems some one was connected to the system and were attempting to break-in but failed due to the strong password set on the device. This sounds to me a potential vulnerability with the system and adversary was able to exploit it and gained access to the system and was attempting to login ?
The log doesn't show where the attempts where made from which IP, it just says "
IP Address Local
It is crazy how could someone connect through to the NVR console remotely? NVR is connect to the router which has private WAN IP issue by ISP and is not directly exposed to internet as the IP is non routable/reachable from internet.
As anyone every encountered such situation ?
New to this forum,
I own a Dahua DHI-NVR5216-16P-4KS2E [V4.001.0000006.0, Build Date: 2021-02-08 ]and recently noted a long beep from the system, never heard such beep before, looked at the system log and noticed 5 failed login attempts and again after few minutes heard same long beep and this time was looking at the monitor console (connected to console port of NVR) and noted someone was attempting to login and could see characters being entered on the login dialog box's password text field. (refer image)
Seems some one was connected to the system and were attempting to break-in but failed due to the strong password set on the device. This sounds to me a potential vulnerability with the system and adversary was able to exploit it and gained access to the system and was attempting to login ?
The log doesn't show where the attempts where made from which IP, it just says "
IP Address Local
It is crazy how could someone connect through to the NVR console remotely? NVR is connect to the router which has private WAN IP issue by ISP and is not directly exposed to internet as the IP is non routable/reachable from internet.
As anyone every encountered such situation ?