Ubiquity EdgeRouter X - Configuring to Isolate Surveillance Networks
(This topic began as an inquiry regarding interest. Enough desire was shown to proceed. Main content is later in this thread)
Main content begins at Ubiquity EdgeRouter X - Configuring to Isolate Surveillance Networks
Introduction
The Ubiquity EdgeRouter X is a low cost ($62), highly configurable, stable, managed router that can safeguard your surveillance network from cameras "phoning home" while still giving you full access to cameras from your computer. Unfortunately, configuring an EdgeRouter X is difficult and requires considerable network knowledge. The router arrives from factory as little more than a switch. Once configured, it is a powerful device, but many steps are required to configure the router into a useful router and firewall.
For someone well versed in network wiring, protocols, and router rules, that process can require hours of painstaking work.
This topic provides provide a faster, easier path via a pre-configured settings file.
Configuration Features
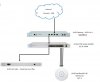
WAN 0 (eth0) - This connects to the internet and expects to receive its WAN address via DHCP. Typically your cable modem in bridge mode would connect to this.
LAN 1 Main (eth1) - Main, general purpose network that has full access to WAN and all other LANs. Because main LAN has full access to other LAN's, your main computer can connect with surveillance, and IOT devices.
Guest WiFi (eth0.1003) - VLAN 1003 for guest access WiFi access points. Access only to internet, but no LAN's
LAN 2 Surveillance (ETH2) - Isolated LAN that cannot access the internet nor any other LAN. Cameras and NVR/PC live on this isolated network. Only the NVR/PC is (optionally) granted special access to WAN. Cameras cannot access anything on the outside world. They even must get NTP time from the EdgeRouter X.
LAN 3 Limited - A limited LAN for IOT devices. Limited LAN 3 can reach internet, but no other LAN's
LAN 4 Limited - Another limited LAN. Limited LAN 4 can reach internet, but no other LAN's
OpenVPN server (vtun0) - OpenVPN tunneling for remote access. This is an advanced setup feature. For security purposes, it is not pre-built in my configuration file. Instead I supply instructions for building the OpenVPN service on your EdgeRouter.
Notes:
Each LAN is physically separate, and on different ip ranges.
LoopBack (aka Hairpin NAT) works with EdgeRouter X. You can use same DynDNS name inside and outside of your network.
We will not be using the EdgeRouter X's pass through POE.
Network Wiring
(This topic began as an inquiry regarding interest. Enough desire was shown to proceed. Main content is later in this thread)
Main content begins at Ubiquity EdgeRouter X - Configuring to Isolate Surveillance Networks
Introduction
The Ubiquity EdgeRouter X is a low cost ($62), highly configurable, stable, managed router that can safeguard your surveillance network from cameras "phoning home" while still giving you full access to cameras from your computer. Unfortunately, configuring an EdgeRouter X is difficult and requires considerable network knowledge. The router arrives from factory as little more than a switch. Once configured, it is a powerful device, but many steps are required to configure the router into a useful router and firewall.
For someone well versed in network wiring, protocols, and router rules, that process can require hours of painstaking work.
This topic provides provide a faster, easier path via a pre-configured settings file.
Configuration Features
WAN 0 (eth0) - This connects to the internet and expects to receive its WAN address via DHCP. Typically your cable modem in bridge mode would connect to this.
LAN 1 Main (eth1) - Main, general purpose network that has full access to WAN and all other LANs. Because main LAN has full access to other LAN's, your main computer can connect with surveillance, and IOT devices.
Guest WiFi (eth0.1003) - VLAN 1003 for guest access WiFi access points. Access only to internet, but no LAN's
LAN 2 Surveillance (ETH2) - Isolated LAN that cannot access the internet nor any other LAN. Cameras and NVR/PC live on this isolated network. Only the NVR/PC is (optionally) granted special access to WAN. Cameras cannot access anything on the outside world. They even must get NTP time from the EdgeRouter X.
LAN 3 Limited - A limited LAN for IOT devices. Limited LAN 3 can reach internet, but no other LAN's
LAN 4 Limited - Another limited LAN. Limited LAN 4 can reach internet, but no other LAN's
OpenVPN server (vtun0) - OpenVPN tunneling for remote access. This is an advanced setup feature. For security purposes, it is not pre-built in my configuration file. Instead I supply instructions for building the OpenVPN service on your EdgeRouter.
Notes:
Each LAN is physically separate, and on different ip ranges.
LoopBack (aka Hairpin NAT) works with EdgeRouter X. You can use same DynDNS name inside and outside of your network.
We will not be using the EdgeRouter X's pass through POE.
Network Wiring
- NEVER NEVER connect an ethernet cable between different LANs. They must remain separate. Their only interconnection is via the EdgeRouter X.
- Each LAN coming out of the EdgeRouter gets connected to a physically separate switch. For instance, LAN 1 Main would connect to a regular network switch. Then, your regular network devices would connect to that Main LAN switch.
- Your Surveillance LAN 2 would be well served with a POE+ switch into which your surveillance cameras and recording PC connect.
- If you use an NVR and it implements its own subnet, your cameras can alternatively connect to the NVR.
Last edited: