Hi everyone,
I am working on an open-source project I would like to share with people used to play with videosurveillance cameras and propose you to participate.
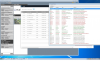
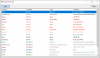
This is small unique tool that scan a network and can detect several camera vendors, using open protocols (ONVIF, UPnP, etc.) but ALSO proprietary vendor discovery protocols.
Very last build 2022-02-12 with more protocols can be found here: UniversalScanner (Portable) or here: UniversalScanner (Installer).
Added : Advantech
I am looking for Dlink camera owner, Foscam camera owner or HID Controller owner that could help me to perform tests.
You will need Windows system with dotNet v4.5.2
Today, it supports the open protocols bellow:
You have a bunch of advanced options in registry (IPv6, show all protocols, show auto-config IPs, enhance ONVIF compatibility, etc.), more details here.
I was thinking to make also a Linux software port later (would be in command line) for installers who install/use camera over Linux.
You know another vendor discovery protocol that would be good to have integrated into the tool?
Then you can follow this procedure to collect enough information for me to integrate a new private detection protocol.
Thanks!
Julien
I am working on an open-source project I would like to share with people used to play with videosurveillance cameras and propose you to participate.
This is small unique tool that scan a network and can detect several camera vendors, using open protocols (ONVIF, UPnP, etc.) but ALSO proprietary vendor discovery protocols.

Very last build 2022-02-12 with more protocols can be found here: UniversalScanner (Portable) or here: UniversalScanner (Installer).
Added : Advantech
I am looking for Dlink camera owner, Foscam camera owner or HID Controller owner that could help me to perform tests.
Release UniversalScanner 2021-09-05 · julienblitte/UniversalScanner (added version notifier)
Release UniversalScanner 2021-07-21 · julienblitte/UniversalScanner (added protocol Advantech)
Release UniversalScanner 2021-06-06 · julienblitte/UniversalScanner (added contextual menu)
Release UniversalScanner 2021-05-17 · julienblitte/UniversalScanner (added protocol GCE, fixed Dahua DSS issue)
Release UniversalScanner 2021-02-13 · julienblitte/UniversalScanner (added protocol Eaton)
Release UniversalScanner 2021-07-21 · julienblitte/UniversalScanner (added protocol Advantech)
Release UniversalScanner 2021-06-06 · julienblitte/UniversalScanner (added contextual menu)
Release UniversalScanner 2021-05-17 · julienblitte/UniversalScanner (added protocol GCE, fixed Dahua DSS issue)
Release UniversalScanner 2021-02-13 · julienblitte/UniversalScanner (added protocol Eaton)
You will need Windows system with dotNet v4.5.2
Today, it supports the open protocols bellow:
- SSDP (UPnP)
- WS-Discovery (ONVIF)
- DNS-SD (Zeroconf)
- GigE Vision (industrial cam protocol)
- Axis
- HikVision
- Dahua
- Bosch
- Hanwha
- Vivotek
- Sony
- 360Vision
- NiceVision
- Panasonic
- Arecont
- Ubiquiti
- Eaton
- Advantech
- Google Cast
- VStarCam
- Microchip
- Lantronix
- Eden Optima Box
- Uniview: ONVIF/WS-Discovery
- Flir: UPnP/SSDP and GigE Vision
- Siqura: UPnP/SSDP and ONVIF/WS-Discovery
- Mobotix: ONVIF/WS-Discovery
- GCE Electronics: Microchip (enhanced)
- ELA Access Control: Microchip
- Vauban Access Control: Lantronix
- Eden Access Control (sub-controller): Lantronix
You have a bunch of advanced options in registry (IPv6, show all protocols, show auto-config IPs, enhance ONVIF compatibility, etc.), more details here.
I was thinking to make also a Linux software port later (would be in command line) for installers who install/use camera over Linux.
You know another vendor discovery protocol that would be good to have integrated into the tool?
Then you can follow this procedure to collect enough information for me to integrate a new private detection protocol.
Thanks!
Julien
Last edited: