Well, I'd rather hear something like that than....you know...like he took a dirt nap. Thanks for that feedback.I stumbled on a post on a different forum a few months ago where he stated he was a former member of IPCamtalk. He said he had his reasons but didn't elaborate.
VPN Primer for Noobs
- Thread starter nayr
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Jim I.
Getting comfortable
I've been trying to find the forum where I saw his post, but no luck so far. I think it was either on Reddit or Blueirissoftware.com. I recognized him because I believe he was using the same name.Well, I'd rather hear something like that than....you know...like he took a dirt nap. Thanks for that feedback.
Could be, and I hope it's that. Six years is a long break!I vaguely remember someone saying he was talking a break since IPCAMTALK was taking a lot of time away from the rest of his life.
TwoDollarBlue
n3wb
If I hardwire my BI computer directly to the router running OpenVPN, is there any need to login as a client on OpenVPN connect? I ask because when I was logging in as a client the subnet ip assigned would change based on the order the clients connected. This made me have to constantly change the IP on the BlueIris iOS app which is annoying.
Hi,
I use a dsl infrastructure for my network.
I'm considering of moving to fiber infrastructure.
Thus i need to replace my bridge roter to a media converter.
Now: ISP dsl -> bridge -> vpn router.
After: ISP fiber -> media converter -> vpn router.
I'm considering of buying a cheap media converter (ZTE F601).
Should i but a more secured one? (or more reliable) or rather it is not important, because data is encrypted anyway via the vpn tunnel (POPE wan is defined within the vpn router).
Thanks.
I use a dsl infrastructure for my network.
I'm considering of moving to fiber infrastructure.
Thus i need to replace my bridge roter to a media converter.
Now: ISP dsl -> bridge -> vpn router.
After: ISP fiber -> media converter -> vpn router.
I'm considering of buying a cheap media converter (ZTE F601).
Should i but a more secured one? (or more reliable) or rather it is not important, because data is encrypted anyway via the vpn tunnel (POPE wan is defined within the vpn router).
Thanks.
Last edited:
Wouldn't it be more like this? And you would have an ONT and not need a media converter?
ISP fiber -> ONT (Optical Modem) -> VPN router
Well, it is actually consider to be an ONU device (i'm not familiar with the difference in compare to ONT).
ISP fiber -> ONU -> VPN router
I wonder about the vulnerability of using it.
Now, I'm using a DSL router which functions as a bridge to my vpn router.
Last edited:
An ONT and an ONU are the same thing. ONT and ONU both refer to the consumer end equipment in an optical fiber to the home (FTTH) communication link. ONT is an ITU-T term, whereas ONU is an IEEE term. ITU-T and IEEE are two different telecommunication standards.Well, it is actually consider to be an ONU device (i'm not familiar with the difference in compare to ONT).
ISP fiber -> ONU -> VPN router
I wonder about the vulnerability of using it.
Now, I'm using a DSL router which functions as a bridge to my vpn router.
Your DSL modem was likely running in "bridge mode" meaning it simply furnished the Internet and the router did the routing.
The ZTE F601 "media converter" in your first post IS, in fact, an ONT....so "ISP fiber -> ONU or ONT -> VPN router" is what you'll have.
Doesn't your ISP provide the ONT/ONU ?
It provides a router (others do provide ont).An ONT and an ONU are the same thing. ONT and ONU both refer to the consumer end equipment in an optical fiber to the home (FTTH) communication link. ONT is an ITU-T term, whereas ONU is an IEEE term. ITU-T and IEEE are two different telecommunication standards.
Your DSL modem was likely running in "bridge mode" meaning it simply furnished the Internet and the router did the routing.
The ZTE F601 "media converter" in your first post IS, in fact, an ONT....so "ISP fiber -> ONU or ONT -> VPN router" is what you'll have.
Doesn't your ISP provide the ONT/ONU ?
One should buy the ont independently.
Too bad. It leaves the ISP an outlet to blame your equipment when something doesn't work as it should....like the Internet being "down".It provides a router (others do provide ont).
One should buy the ont independently.
I hope I'm wrong but I've seen that a lot.
Do they at least provide a list of "recommended" ONT's for you to purchase to help insure compatibility and proper function?
Too bad. It leaves the ISP an outlet to blame your equipment when something doesn't work as it should....like the Internet being "down".
I hope I'm wrong but I've seen that a lot.
Do they at least provide a list of "recommended" ONT's for you to purchase to help insure compatibility and proper function?
Yes, they do provide it (a list).
Their router gives them an indication about the connectivity, but I can't use it with my private VPN router (it doesn't have 'disable NAT' - I believe nor their router).
Also, I'm not sure how to configure them to work together.
Last edited:
Thanks for the mass of information. But I've a few questions.
The picture should help to understand my questions:
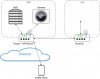
The picture should help to understand my questions:

- Why should I use a Router as a VPN-Server instead of using a VPN-Server behind the Router?
- I see that I should put the NVR in a Demilitarized Zone. But is it OK to put the cameras in the same subnet or is it better to put them in a seperate subnet (seperate router)?
- Should the participants in the DMZ be VPN-Clients or is it enough if the Server only shares his subnet with the VPN-Clients?
- I would configure a Firewall in Router A which
- - allows VPN-traffic into and outto the DMZ (maybe this answered the first question)
- - allows all traffic from and to Router B
- - denies everything else
-> would you agree? ( I know this is very roughly)
- - I think for camera-applications it's better to use wireguard ( because of the speed). Do You know some router in which I can configure a Wireguard-server or -client?
The Automation Guy
Known around here
Wireguard is the current way to go...
Not to be argumentative, but that is a pretty blanket statement that simply isn't true in every situation.
While Wireguard is a great choice in a lot of situations, it is also very basic and can struggle to make reconnections in some situations. You can usually force it to reconnect by restarting the VPN connection, but for a VPN that automatically shuts down the connection when data is not being transmitted and is supposed to restart it when needed, that is a huge hassle..... (It's like if your car that turns the engine off while idling to save fuel won't restart the engine when you push the gas pedal and you have to turn the key to restart it every time).
Last edited:
The Automation Guy
Known around here
If I understand your question correctly, the answer is no. You should never need to login to the VPN from the local network (and it probably won't work even if you tried due to "hairpin turning"). You only need to login to the VPN when you are away from your local network and want to connect to it. Any devices on the local network will work normally and don't need to be "logged into" the VPN and they will be accessible over the VPN.If I hardwire my BI computer directly to the router running OpenVPN, is there any need to login as a client on OpenVPN connect? I ask because when I was logging in as a client the subnet ip assigned would change based on the order the clients connected. This made me have to constantly change the IP on the BlueIris iOS app which is annoying.
Think of the VPN as a gateway in your router/firewall in the same way as your internet connection is a gateway. This gateway is just a conduit for data to travel through. The device on the local network are agnostic to the gateway. Their data might pass through it, but the devices themselves don't know the gateway exists. That functionality is provided by your router/L3 network devices.
TwoDollarBlue
n3wb
@The Automation Guy thank you for the response. That makes sense and makes my remote logins much easier.
Sparkey
Getting comfortable
OK, too much gibberish to slog through. I'm totally confused. My setup is as follows -
IP cams are on a non routed dedicated subnet (no gateway and no DNS)
Dedicated Blue Iris server.
Device that needs to be able to connect from outside the local network - iPhone.
That's it.
All of the instructions I've read seem to describe a much more complicated system. I don't need or want anything beyond what's listed above.
Also as a side note, I'm using OPNSense as my router. I have GeoIP installed and enabled and I'm still getting hit by China, the UK and a few others that are supposedly blocked. Anybody know why and how to correct this?
TIA
IP cams are on a non routed dedicated subnet (no gateway and no DNS)
Dedicated Blue Iris server.
Device that needs to be able to connect from outside the local network - iPhone.
That's it.
All of the instructions I've read seem to describe a much more complicated system. I don't need or want anything beyond what's listed above.
Also as a side note, I'm using OPNSense as my router. I have GeoIP installed and enabled and I'm still getting hit by China, the UK and a few others that are supposedly blocked. Anybody know why and how to correct this?
TIA
The Automation Guy
Known around here
First, you have to understand how firewalls and traffic routing work. (I'm not an IT expert and this following section is probably not technically correct, but hopefully you will understand the "gist" of it). There is basically two types of traffic coming into your local network: unsolicited traffic and solicited traffic. Solicited traffic is a response to an inquiry made by devices on your local network. Unsolicited traffic is traffic trying to access your network that was not initiated by some device on your network. Your firewall is only attempting to block the unsolicited traffic. It is always going to allow solicited traffic into the network, regardless of the geographic source of that data.Also as a side note, I'm using OPNSense as my router. I have GeoIP installed and enabled and I'm still getting hit by China, the UK and a few others that are supposedly blocked. Anybody know why and how to correct this?
TIA
This means that using GeoIP is really redundant to what the firewall is doing (by default at least). That's because by default the firewall is stopping ALL unsolicited outside traffic from getting in. GeoIP doesn't block any data that the firewall isn't also blocking unless you are allowing unsolicited outside traffic into your firewall for some reason.
Obviously if you have the ability to access your local network remotely (through port forwarding or a VPN service, etc), then you are allowing unsolicited outside traffic into your network. In that case, adding GeoIP can help by blocking unsolicited data from selected geographical areas. Just understand it is far from fool proof because it doesn't stop a Chinese hacker from simply using a VPN service to make his traffic appear to be originating in the USA (which obviously you probably wouldn't be blocking). Still, it does help filter out a bunch of noise before it hits your network. In fact that is exactly how I would describe it - GeoIP is a noise filter, not a security measure.
All that being said, the GeoIP still only blocks unsolicited traffic. If there is a device on your network trying to communicate with a server located in Chinese, UK, or anywhere else, the firewall is going to allow it because it is solicited traffic originating from your local network. This is why it is so important to isolate CCTV cameras and other IOT devices on your network and only allow them access to the internet if it is required (like a video streamer).
Also, are you sure that you are not simply confusing the logging that the GeoIP service does and assuming that traffic is allowed on the network? You should see unsolicited traffic from blocked GeoIPs being logged, but you should also see that the traffic was blocked and not allowed through. If it is being logged, but allowed through, then there is probably something wrong with your GeoIP settings.
Last edited:
Sparkey
Getting comfortable
Thank you sir. I'm seeing the access attempt within Blue iris.
I just slogged through setting up OpenVPN in OPNSense and now I'm even more confused than I've ever been. The only to devices I want to use the VPN is my iphone and the Blue iris server. Nothing in the instructions I followed said anything about the local (Blue Iris) server and other than sending the QR code to the iPhone itsaid nothing about setting up the Blue Iris app on the iPhone. Plus there were far to many option listed without a recommendation and most of them are anything but self explanatory.
And last but not least, how am i supposed to know if the VPN is working? Should all my computers be using the VPN? How do i set it up for just one computer to use it?
Been at this all day. Wish there was an overview with options instead of a follow this list type of instructions?
Wish there was an overview with options instead of a follow this list type of instructions?
I just slogged through setting up OpenVPN in OPNSense and now I'm even more confused than I've ever been. The only to devices I want to use the VPN is my iphone and the Blue iris server. Nothing in the instructions I followed said anything about the local (Blue Iris) server and other than sending the QR code to the iPhone itsaid nothing about setting up the Blue Iris app on the iPhone. Plus there were far to many option listed without a recommendation and most of them are anything but self explanatory.
And last but not least, how am i supposed to know if the VPN is working? Should all my computers be using the VPN? How do i set it up for just one computer to use it?
Been at this all day.
Mike A.
Known around here
- May 6, 2017
- 4,202
- 7,073
Nobody here has any idea how you now have OPNsense set up so can't help you there much. But as a clean starting point you should not have anything from the outside getting through the firewall to hit the BI server. Whatever you've done to enable that as far as rules should be disabled. You must have something permitting that traffic through if you're seeing connection attempts at the BI server. Unless you have some specific need to permit traffic through for any other purpose, then you should take down all other outside -> inside rules permitting traffic through by port, etc. too. Then, as Automation Guy says above, you won't need any geoIP blocks since nothing will be getting through the outside interface of the firewall to bother sorting out by geo source. Any unsolicited traffic from outside will be blocked.
Once you have OpenVPN set up on your firewall, that will open one port (1194 by default) on the outside interface of the firewall which will require a password/key exchange to allow a connection to/through it. You'll set up the OpenVPN client on your phone to do that. Once you do that and have it working, then when you make that connection from outside of your network using your phone, it will (for most practical purposes) become a client on your local network and will work as if it were inside local to your network. i.e., If your local address space is 192.168.1.x, then the phone will end up with at 192.168.1.x IP address. (There are some more details re how that works which is why I said for most practical purposes but ignore that for now).
So at that point you don't need to do anything as far as setting up outside access to the BI server is concerned. It will work in the same way that it would if you were using it locally inside your network. In the BI app you'll point the IP of the local and remote address of the BI server to the same local IP. Don't bother with scanning any codes, etc. You don't need to have your other computers that are inside your network using the VPN since they are inside vs outside and don't have to come through the firewall. You can tell whether the firewall is working or not by trying to hit your network from outside with/without having the OpenVPN client enabled. It should not permit connection in the latter case.
Unless you have a static external IP address then you'll also need to set up DHCP in order to let the VPN client find your IP whatever it may be by hostname.
Once you have OpenVPN set up on your firewall, that will open one port (1194 by default) on the outside interface of the firewall which will require a password/key exchange to allow a connection to/through it. You'll set up the OpenVPN client on your phone to do that. Once you do that and have it working, then when you make that connection from outside of your network using your phone, it will (for most practical purposes) become a client on your local network and will work as if it were inside local to your network. i.e., If your local address space is 192.168.1.x, then the phone will end up with at 192.168.1.x IP address. (There are some more details re how that works which is why I said for most practical purposes but ignore that for now).
So at that point you don't need to do anything as far as setting up outside access to the BI server is concerned. It will work in the same way that it would if you were using it locally inside your network. In the BI app you'll point the IP of the local and remote address of the BI server to the same local IP. Don't bother with scanning any codes, etc. You don't need to have your other computers that are inside your network using the VPN since they are inside vs outside and don't have to come through the firewall. You can tell whether the firewall is working or not by trying to hit your network from outside with/without having the OpenVPN client enabled. It should not permit connection in the latter case.
Unless you have a static external IP address then you'll also need to set up DHCP in order to let the VPN client find your IP whatever it may be by hostname.
