Hello
Can someone help me, i have probably a chineese IPC-HDBW4631R-ZS, i tried to update with this FW (DH_IPC-HX5X3X-Rhea_MultiLang_PN_Stream3_V2.800.0000012.0.R.190808.zip)
But it dont let me connect to the web.
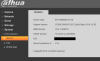
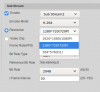
Device-Type: IPC-HDBW4631R-ZS
Firmware: 2.460.0000000.16.R, Build Date: 2017-09-04
WEB-Version: 3.2.1.491565
ONVIF Version: 16.12(V2.4.0.485616)
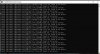
Ping is possible, i also tried with TFTP but without success. here is the log:
*******************************************************
Ncat: Version 7.40 (
Ncat - Netcat for the 21st Century )
Ncat: Listening on 192.168.254.254:5002
gBootLogPtr:00b80008.
spinor flash ID is 0x1940ef
partition file version 2
rootfstype squashfs root /dev/mtdblock5
gParameter[0]:node=bootargs, parameter=console=ttyS0,115200 mem=130M root=/dev/mtdblock5 rootfstype=squashfs init=/linuxrc.
TEXT_BASE:01000000
Net: PHY:0x001cc816,addr:0x00
s3l phy RTL8201 init
partition file version 2
rootfstype squashfs root /dev/mtdblock5
MMC: sdmmc init
Using ambarella mac device
Download Filename 'upgrade_info_7db780a713a4.txt'.Downloading: 100%
## file size: 202 Bytes, times: 0s, speed: 24.4 KiB/s
done
Bytes transferred = 202 (ca hex)
Using ambarella mac device
Download Filename 'romfs-x.squashfs.img'.Downloading: 100% 100%
## file size: 2.8 MiB, times: 2s, speed: 1 MiB/s
done
Bytes transferred = 2902264 (2c48f8 hex)
curVer:V1.4 <= newVer:V1.4,verCompare success!
[0;32mUBOOT_commonSwRsaVerify run successfully!
[0m
## Checking Image at 02000000 ...
Legacy image found
Image Name: romfs
Created: 2019-08-08 11:54:00 UTC
Image Type: ARM Linux Kernel Image (uncompressed)
Data Size: 2899968 Bytes = 2.8 MiB
Load Address: 01b80000
Entry Point: 01fd0000
Verifying Checksum ... OK
Programing start at: 0x01b80000 for romfs
SPI probe: 32768 KiB W25Q256FV at 0:1 is now current device
write : 100%
done
crc from program is :f2749777, crc from flash is :f2749777
partition file version 2
rootfstype squashfs root /dev/mtdblock5
gParameter[0]:node=bootargs, parameter=console=ttyS0,115200 mem=130M root=/dev/mtdblock5 rootfstype=squashfs init=/linuxrc.
Using ambarella mac device
Download Filename 'kernel.img'.Downloading: 100%
## file size: 1.5 MiB, times: 1s, speed: 1018.6 KiB/s
done
Bytes transferred = 1575384 (1809d8 hex)
curVer:V1.4 <= newVer:V1.4,verCompare success!
[0;32mUBOOT_commonSwRsaVerify run successfully!
[0m
## Checking Image at 02000000 ...
Legacy image found
Image Name: kernel
Created: 2019-08-08 11:52:32 UTC
Image Type: ARM Linux Firmware (uncompressed)
Data Size: 1573088 Bytes = 1.5 MiB
Load Address: 01040000
Entry Point: 01200000
Verifying Checksum ... OK
Programing start at: 0x01040000 for kernel
SPI probe: 32768 KiB W25Q256FV at 0:1 is now current device
write : 100%
done
crc from program is :67fdba11, crc from flash is :67fdba11
partition file version 2
rootfstype squashfs root /dev/mtdblock5
gParameter[0]:node=bootargs, parameter=console=ttyS0,115200 mem=130M root=/dev/mtdblock5 rootfstype=squashfs init=/linuxrc.
Using ambarella mac device
Download Filename 'user-x.squashfs.img'.Downloading: 100%
## file size: 14.8 MiB, times: 14s, speed: 1 MiB/s
done
Bytes transferred = 15554808 (ed58f8 hex)
curVer:V1.4 <= newVer:V1.4,verCompare success!
[0;32mUBOOT_commonSwRsaVerify run successfully!
[0m
## Checking Image at 02000000 ...
Legacy image found
Image Name: user
Created: 2019-08-08 11:53:28 UTC
Image Type: ARM Linux Standalone Program (uncompressed)
Data Size: 15552512 Bytes = 14.8 MiB
Load Address: 000f0000
Entry Point: 01000000
Verifying Checksum ... OK
Programing start at: 0x000f0000 for user
write : 100%
done
crc from program is :ed82b853, crc from flash is :ed82b853
partition file version 2
rootfstype squashfs root /dev/mtdblock5
gParameter[0]:node=bootargs, parameter=console=ttyS0,115200 mem=130M root=/dev/mtdblock5 rootfstype=squashfs init=/linuxrc.
Using ambarella mac device
Download Filename 'web-x.squashfs.img'.Downloading: 100%
## file size: 4.8 MiB, times: 4s, speed: 1 MiB/s
done
Bytes transferred = 5064952 (4d48f8 hex)
curVer:V1.4 <= newVer:V1.4,verCompare success!
[0;32mUBOOT_commonSwRsaVerify run successfully!
[0m
## Checking Image at 02000000 ...
Legacy image found
Image Name: web
Created: 2019-08-08 11:53:07 UTC
Image Type: ARM Linux Standalone Program (uncompressed)
Data Size: 5062656 Bytes = 4.8 MiB
Load Address: 01200000
Entry Point: 01880000
Verifying Checksum ... OK
Programing start at: 0x01200000 for web
SPI probe: 32768 KiB W25Q256FV at 0:1 is now current device
write : 100%
done
crc from program is :35944947, crc from flash is :35944947
partition file version 2
rootfstype squashfs root /dev/mtdblock5
gParameter[0]:node=bootargs, parameter=console=ttyS0,115200 mem=130M root=/dev/mtdblock5 rootfstype=squashfs init=/linuxrc.
Using ambarella mac device
Download Filename 'partition-x.cramfs.img'.Downloading: 100%
## file size: 10.2 KiB, times: 0s, speed: 426.8 KiB/s
done
Bytes transferred = 10488 (28f8 hex)
curVer:V1.4 <= newVer:V1.4,verCompare success!
[0;32mUBOOT_commonSwRsaVerify run successfully!
[0m
## Checking Image at 02000000 ...
Legacy image found
Image Name: partition
Created: 2019-08-08 11:52:32 UTC
Image Type: ARM Linux Standalone Program (uncompressed)
Data Size: 8192 Bytes = 8 KiB
Load Address: 000e0000
Entry Point: 000f0000
Verifying Checksum ... OK
Programing start at: 0x000e0000 for partition
write : 100%
done
crc from program is :bfb829ac, crc from flash is :bfb829ac
partition file version 2
rootfstype squashfs root /dev/mtdblock5
gParameter[0]:node=bootargs, parameter=console=ttyS0,115200 mem=130M root=/dev/mtdblock5 rootfstype=squashfs init=/linuxrc.
Using ambarella mac device
Download Filename 'custom-x.squashfs.img'.Downloading: 100%
## file size: 734.2 KiB, times: 0s, speed: 987.3 KiB/s
done
Bytes transferred = 751864 (b78f8 hex)
curVer:V1.4 <= newVer:V1.4,verCompare success!
[0;32mUBOOT_commonSwRsaVerify run successfully!
[0m
## Checking Image at 02000000 ...
Legacy image found
Image Name: custom
Created: 2019-08-08 11:55:46 UTC
Image Type: ARM Linux Standalone Program (uncompressed)
Data Size: 749568 Bytes = 732 KiB
Load Address: 018a0000
Entry Point: 01970000
Verifying Checksum ... OK
Programing start at: 0x018a0000 for custom
SPI probe: 32768 KiB W25Q256FV at 0:1 is now current device
write : 100%
done
crc from program is :9276625c, crc from flash is :9276625c
partition file version 2
rootfstype squashfs root /dev/mtdblock5
gParameter[0]:node=bootargs, parameter=console=ttyS0,115200 mem=130M root=/dev/mtdblock5 rootfstype=squashfs init=/linuxrc.
Using ambarella mac device
Download Filename 'pd-x.squashfs.img'.Downloading: 100%
## file size: 82.2 KiB, times: 0s, speed: 733.4 KiB/s
done
Bytes transferred = 84216 (148f8 hex)
curVer:V1.4 <= newVer:V1.4,verCompare success!
[0;32mUBOOT_commonSwRsaVerify run successfully!
[0m
## Checking Image at 02000000 ...
Legacy image found
Image Name: pd
Created: 2019-08-08 11:55:43 UTC
Image Type: ARM Linux Standalone Program (uncompressed)
Data Size: 81920 Bytes = 80 KiB
Load Address: 01880000
Entry Point: 018a0000
Verifying Checksum ... OK
Programing start at: 0x01880000 for pd
SPI probe: 32768 KiB W25Q256FV at 0:1 is now current device
write : 100%
done
crc from program is :98e9a557, crc from flash is :98e9a557
partition file version 2
rootfstype squashfs root /dev/mtdblock5
gParameter[0]:node=bootargs, parameter=console=ttyS0,115200 mem=130M root=/dev/mtdblock5 rootfstype=squashfs init=/linuxrc.
Using ambarella mac device
Download Filename '.FLASHING_DONE_STOP_TFTP_NOW'.Downloading: ##
## file size: 0 Bytes, times: 0s, speed: 0 Bytes/s
done
partition file version 2
rootfstype squashfs root /dev/mtdblock5
fail to load bootargsParameters.txt
fail to load bootargsParameters.txt file
cmdLine console=ttyS0,115200 mem=130M root=/dev/mtdblock5 rootfstype=squashfs init=/linuxrc
*******************************************************
Thanks for your help
ZHCIP