You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
simonchan
n3wb
Wael
Getting the hang of it
I haven't attempted any of this stuff yet. Just trying to read up and get educated before I attempt. I have a few questions if someone would be kind enough to help me out:
What TFTP Server application do you folks recommend?
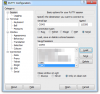
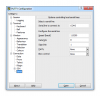
Are there any specific IP settings for that TFTP server?
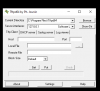
In Putty, under the "Basic Options" tab, what IP and port settings should be here?
Thanks!!
What TFTP Server application do you folks recommend?
Are there any specific IP settings for that TFTP server?
In Putty, under the "Basic Options" tab, what IP and port settings should be here?
Thanks!!
Wael
Getting the hang of it
TFTPD32 or TFTPServer (Cisco) or ...
All specific thing an 1st page
View attachment 46422View attachment 46424
Thank you!!
Wael
Getting the hang of it
Wael
Getting the hang of it
Thank you kind sir! I got it working. I just had to reboot my computer because previously I had another TFTP server running that was already binding to port 69 I think. Possibly that application caused this conflict.
Under "server interfaces", do I have to put my computer IP here or just leave it as is?
Under "server interfaces", do I have to put my computer IP here or just leave it as is?
Wael
Getting the hang of it
Ok another question. Sorry this might be a dumb question.
I take it that using this method of unbricking, there is no ethernet connection to the camera during the process. Basically all communications are via serial.
Is this correct?
I take it that using this method of unbricking, there is no ethernet connection to the camera during the process. Basically all communications are via serial.
Is this correct?
No.
You operate your ipc via serial, put command to get some data from LAN if it connected & work (of course need setup 1st adresses)
Of course you can upload some data via Serial at Hyper Terminal program, but it longer & not this time i think.
You operate your ipc via serial, put command to get some data from LAN if it connected & work (of course need setup 1st adresses)
Of course you can upload some data via Serial at Hyper Terminal program, but it longer & not this time i think.
I've done a Firmware Update to my
Dahua IPC-HUM8230P
I don't know if I took the the right firmware I'm not sure,
Since I've updatet I coudn't do any changes in the configuration.
The Cam does a reboot then.
It does also a reboot every 5 to 10 minutes.
So far I've confiigures a serial connection with a ft232rl usb to seriel conector and aftr many tries I got a connection.
I changed ip address and run a tftp server and could load files down but I got this message
I've googeled the message and found this:
Dahua IPC EASY unbricking / recovery over TFTP
I think the problem is that the new firmware installed a new bootloader that doesn't allow firmwaredowngrades.
Please tell me how do I et the older firmware to my cam
Dahua IPC-HUM8230P
I don't know if I took the the right firmware I'm not sure,
Since I've updatet I coudn't do any changes in the configuration.
The Cam does a reboot then.
It does also a reboot every 5 to 10 minutes.
So far I've confiigures a serial connection with a ft232rl usb to seriel conector and aftr many tries I got a connection.
I changed ip address and run a tftp server and could load files down but I got this message
Code:
>run dr
Using ambarella mac device
Download Filename 'romfs-x.squashfs.img'.
Downloading: #################################################################
#################################################################
#################################################################
###############################################################
## file size: 0 Bytes, times: 3s, speed: 358.4 KiB/s
done
Bytes transferred = 1310784 (140040 hex)
[ERR0002:]The img header be changed!Dahua IPC EASY unbricking / recovery over TFTP
I think the problem is that the new firmware installed a new bootloader that doesn't allow firmwaredowngrades.
Please tell me how do I et the older firmware to my cam
surv8tor
n3wb
yes, you managed to update your bootloader that now checks for signing before writing an image to the flash. I dont think you have a path forward, unless you manage to read the whole partition from another camera, upload it to a tftp server and then try to see if your bootloader still has the flash subsytem write command still enabled and go that route. Another option is to find the correct firmware for the camera which is compatible with the new signing verification (like v2.800 or something).
Need help unbricking my cam
Cam model SD52C230U-HNI,SD52C230U HNI,SD52C230UHNI,SD52C230U,SD52C230
SD52C230U-HNI
2MP 30x Starlight PTZ Network Camera
Tools used
serial UART device
settings
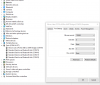
Tftpd64
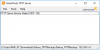
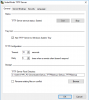
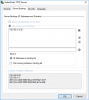
putty
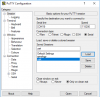
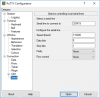
Pc network setting
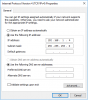
Ping pc
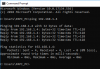
Ping camera
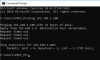
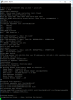
This is the putty display on boot and * key press
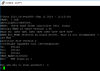
printenv
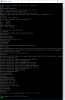
ping $serverip
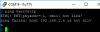
And run dr
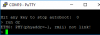
What I am missing or is my camera beyond repairs or do I need a 5-pound hammer.
Cam model SD52C230U-HNI,SD52C230U HNI,SD52C230UHNI,SD52C230U,SD52C230
SD52C230U-HNI
2MP 30x Starlight PTZ Network Camera
Tools used
serial UART device
settings

Tftpd64



putty


Pc network setting

Ping pc

Ping camera

This is the putty display on boot and * key press

printenv

ping $serverip
And run dr
What I am missing or is my camera beyond repairs or do I need a 5-pound hammer.
Attachments
Last edited:
As an eBay Associate IPCamTalk earns from qualifying purchases.
hope__silent
n3wb
Trying to flash DH_IPC-HX5X3X-Rhea_EngSpnFrn_N_Stream3_V2_622_0000000_18_R_201711102 to a Lorex LNB8005-C (Dahua OEM, matches the Dahua IPC-HFW4830E-S from what I've read/found). @Corellon previously did this in this thread. I've followed the steps precisely and am getting the following error.
I am using TFTPD64 instead of the TFTP server provided in the original link, I kept getting failed.txt errors with the other. This one definitely transfers until it hits the "TFTP error: (0)cmd Failed run dr!" I'm using the commands.txt used in the linked post and my upgrade_info looks like this:
CRC:1720558748
MagicString:c016dcd6-cdeb-45df-9fd0-e821bf0e1e62
run dr
run dk
run du
run dw
run dp
run dc
tftp 0x2000000 pd-x.squashfs.img; flwrite
tftp 0x2000000
.FLASHING_DONE_STOP_TFTP_NOW
sleep 5
Really don't know what I'm missing and everywhere I search other people who have run into this issue never posted any solution, if there was one.
Appreciate any help,
Ryan
Code:
Ncat: Version 7.40 ( https://nmap.org/ncat )
Ncat: Listening on 192.168.254.254:5002
gBootLogPtr:00b80008.
spinor flash ID is 0x1940ef
partition file version 2
rootfstype squashfs root /dev/mtdblock5
can not search bootargs settings
fail to parse bootargsParametersV2.text info
fail to init bootargsParametersV2
TEXT_BASE:01000000
Net: Detected MACID:00:40:7f:93:ef:49
PHY:0x001cc816,addr:0x00
s3l phy RTL8201 init
MMC: sdmmc init
Using ambarella mac device
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1Download Filename 'upgrade_info_7db780a713a4.txt'.Download to address: 0x5000000
Downloading: *
done
Bytes transferred = 199 (c7 hex)
Using ambarella mac device
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1Download Filename 'romfs-x.squashfs.img'.Download to address: 0x2000000
Downloading: *
TFTP error: (0)cmd Failed run dr!
partition file version 2
rootfstype squashfs root /dev/mtdblock5
fail to load bootargsParameters.txt
fail to load bootargsParameters.txt file
get bootargs info failed
cmdLine console=ttyS0,115200 mem=118M root=/dev/mtdblock5 rootfstype=squashfs init=/linuxrcI am using TFTPD64 instead of the TFTP server provided in the original link, I kept getting failed.txt errors with the other. This one definitely transfers until it hits the "TFTP error: (0)cmd Failed run dr!" I'm using the commands.txt used in the linked post and my upgrade_info looks like this:
CRC:1720558748
MagicString:c016dcd6-cdeb-45df-9fd0-e821bf0e1e62
run dr
run dk
run du
run dw
run dp
run dc
tftp 0x2000000 pd-x.squashfs.img; flwrite
tftp 0x2000000
.FLASHING_DONE_STOP_TFTP_NOW
sleep 5
Really don't know what I'm missing and everywhere I search other people who have run into this issue never posted any solution, if there was one.
Appreciate any help,
Ryan