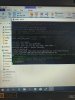
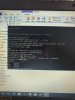
I have read the thread and others quite a few times and haven't seen anything to answer my problem. I admit i am not the best when it comes to doing this kind of stuff that's why i have come to this board hoping someone with knowledge could help me. I would not have got this far without the information from this thread. So if anyone can help please do. Thanks
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
riogrande75
Pulling my weight
Sorry, but when I look at your posts, I guess you did not even understand how it is supposed to work.
Your bootloader does not even try to download anything.
Your bootloader does not even try to download anything.
riogrande75
Pulling my weight
I see. We dont even know what device it is. There is by far too many questions open: cam type, fw you are tryin to flash, pc setup, network setup, ... Your setup is for sure not as it should be.
As I said, pls. read the tread again - I am convinced you did not understand it, sorry.
As I said, pls. read the tread again - I am convinced you did not understand it, sorry.
stsm
n3wb
Have a problem when unbricking my VTO2000.
Try to write this firmware 501655_General_Overseas_VTOXXX_Eng_P_16M_SIP_V1.000.00.0.R.20170425.
TFTP is calling. ...
Putty issue. ...
At the end comes the error message: HWID error, please set hwid first !!!!!!!!!
Try to write this firmware 501655_General_Overseas_VTOXXX_Eng_P_16M_SIP_V1.000.00.0.R.20170425.
TFTP is calling. ...
Putty issue. ...
At the end comes the error message: HWID error, please set hwid first !!!!!!!!!
Code:
Checking DDR......OK
UBL Version: 1.46t(DM365)09:30:17 Sep 2 2014
Oscillator: 24MHZ
ARM Rate: 216 MHZ
DDR Rate: 173 MHZ
BootMode: SPI
Starting SPI Memory Copy...
DONE
U-Boot 1.3.6 (jerry) (Sep 2 2014 - 09:44:01)
DRAM: 128 MB
SF: Got idcode c2 20 18 c2 20
In: serial
Out: serial
Err: serial
Ethernet PHY: GENERIC @ 0x05,id:221513
total gio 2
gio[22]=1
gio[25]=1
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'upgrade_info_7db780a713a4.txt'.
Load address: 0x80100000
Loading: #
done
Bytes transferred = 163 (a3 hex)
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'custom-x.cramfs.img'.
Load address: 0x81a00000
Loading: ##
done
Bytes transferred = 16448 (4040 hex)
## Checking Image at 0x81a00000 ...
Header CRC Checking ... OK
Image Name: custom
Image Type: ARM Linux Standalone Program (gzip compressed)
Data Size: 16384 Bytes = 16 kB
Load Address: 02060000
Entry Point: 02080000
Data CRC Checking ... OK
Programing start at: 0x00060000
write : 100%
done
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'kernel-x.cramfs.img'.
Load address: 0x81a00000
Loading: #################################################################
##################################################
done
Bytes transferred = 1682736 (19ad30 hex)
## Checking Image at 0x81a00000 ...
Header CRC Checking ... OK
Image Name: linux
Image Type: ARM Linux Kernel Image (gzip compressed)
Data Size: 1682672 Bytes = 1.6 MB
Load Address: 02080000
Entry Point: 02280000
Data CRC Checking ... OK
Programing start at: 0x00080000
write : 100%
done
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'romfs-x.cramfs.img'.
Load address: 0x81a00000
Loading: #################################################################
#################################################################
#################################################################
##################
done
Bytes transferred = 3117120 (2f9040 hex)
## Checking Image at 0x81a00000 ...
Header CRC Checking ... OK
Image Name: romfs
Image Type: ARM Linux Kernel Image (gzip compressed)
Data Size: 3117056 Bytes = 3 MB
Load Address: 02280000
Entry Point: 02580000
Data CRC Checking ... OK
Programing start at: 0x00280000
write : 100%
done
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'user-x.cramfs.img'.
Load address: 0x81a00000
Loading: #################################################################
#################################################################
#################################################################
#################################################################
#################################################################
#################################################################
#############
done
Bytes transferred = 5910592 (5a3040 hex)
## Checking Image at 0x81a00000 ...
Header CRC Checking ... OK
Image Name: user
Image Type: ARM Linux Kernel Image (gzip compressed)
Data Size: 5910528 Bytes = 5.6 MB
Load Address: 028e0000
Entry Point: 02ee0000
Data CRC Checking ... OK
Programing start at: 0x008e0000
write : 100%
done
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'web-x.cramfs.img'.
Load address: 0x81a00000
Loading: #################################################################
#####################################
done
Bytes transferred = 1491008 (16c040 hex)
## Checking Image at 0x81a00000 ...
Header CRC Checking ... OK
Image Name: web
Image Type: ARM Linux Standalone Program (gzip compressed)
Data Size: 1490944 Bytes = 1.4 MB
Load Address: 02580000
Entry Point: 02780000
Data CRC Checking ... OK
Programing start at: 0x00580000
write : 100%
done
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'data-x.cramfs.img'.
Load address: 0x81a00000
Loading: ########################################################
done
Bytes transferred = 815168 (c7040 hex)
## Checking Image at 0x81a00000 ...
Header CRC Checking ... OK
Image Name: data
Image Type: ARM Linux Kernel Image (gzip compressed)
Data Size: 815104 Bytes = 796 kB
Load Address: 02ee0000
Entry Point: 03000000
Data CRC Checking ... OK
Programing start at: 0x00ee0000
write : 100%
done
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename '.FLASHING_DONE_STOP_TFTP_NOW'.
Load address: 0x82000000
Loading: #
done
string value is The end of file
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'success.txt'.
Load address: 0x80200000
Loading: #
done
Erasing SPI flash...Writing to SPI flash...done
.......
HWID : <NULL>
HWID : ^
HWID error, please set hwid first!!!!!!!!!
DHBOOT#Hi everyone. Looking for advice my intercom VTO1220 constantly reboots.
I tried to reboot the firmware does not help what else can be done?
The web interface does not work. Under connecting writes and reboots.
Checking DDR......OK
UBL Version: 1.46t(DM365)09:30:17 Sep 2 2014
Oscillator: 24MHZ
ARM Rate: 432 MHZ
DDR Rate: 340 MHZ
BootMode: SPI
Starting SPI Memory Copy...
DONE
U-Boot 1.3.6 (jerry) (Sep 2 2014 - 09:44:01)
DRAM: 128 MB
SF: Got idcode 01 20 18 03 01
In: serial
Out: serial
Err: serial
Ethernet PHY: GENERIC @ 0x05,id:221513
total gio 2
gio[22]=1
gio[25]=1
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'upgrade_info_7db780a713a4.txt'.
Load address: 0x80100000
Loading: *
Retry count exceeded; starting again
Fail to get info file!
Init error!
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'failed.txt'.
Load address: 0x80200000
Loading: *
Retry count exceeded; starting again
==>use default images
.......
## Booting kernel from Legacy Image at 80007fc0 ...
Image Name: Linux-2.6.18_pro500-davinci_evm-
Image Type: ARM Linux Kernel Image (uncompressed)
Data Size: 1771112 Bytes = 1.7 MB
Load Address: 80008000
Entry Point: 80008000
Verifying Checksum ... OK
XIP Kernel Image ... OK
OK
Starting kernel ...
Uncompressing Linux...................................................................................................................... done, booting the kernel.
Checking DDR......OK
I tried to reboot the firmware does not help what else can be done?
The web interface does not work. Under connecting writes and reboots.
Checking DDR......OK
UBL Version: 1.46t(DM365)09:30:17 Sep 2 2014
Oscillator: 24MHZ
ARM Rate: 432 MHZ
DDR Rate: 340 MHZ
BootMode: SPI
Starting SPI Memory Copy...
DONE
U-Boot 1.3.6 (jerry) (Sep 2 2014 - 09:44:01)
DRAM: 128 MB
SF: Got idcode 01 20 18 03 01
In: serial
Out: serial
Err: serial
Ethernet PHY: GENERIC @ 0x05,id:221513
total gio 2
gio[22]=1
gio[25]=1
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'upgrade_info_7db780a713a4.txt'.
Load address: 0x80100000
Loading: *
Retry count exceeded; starting again
Fail to get info file!
Init error!
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'failed.txt'.
Load address: 0x80200000
Loading: *
Retry count exceeded; starting again
==>use default images
.......
## Booting kernel from Legacy Image at 80007fc0 ...
Image Name: Linux-2.6.18_pro500-davinci_evm-
Image Type: ARM Linux Kernel Image (uncompressed)
Data Size: 1771112 Bytes = 1.7 MB
Load Address: 80008000
Entry Point: 80008000
Verifying Checksum ... OK
XIP Kernel Image ... OK
OK
Starting kernel ...
Uncompressing Linux...................................................................................................................... done, booting the kernel.
Checking DDR......OK
Code:
Checking DDR......OK
UBL Version: 1.46t(DM365)09:30:17 Sep 2 2014
Oscillator: 24MHZ
ARM Rate: 432 MHZ
DDR Rate: 340 MHZ
BootMode: SPI
Starting SPI Memory Copy...
DONE
U-Boot 1.3.6 (jerry) (Sep 2 2014 - 09:44:01)
DRAM: 128 MB
SF: Got idcode 01 20 18 03 01
In: serial
Out: serial
Err: serial
Ethernet PHY: GENERIC @ 0x05,id:221513
total gio 2
gio[22]=1
gio[25]=1
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'upgrade_info_7db780a713a4.txt'.
Load address: 0x80100000
Loading: *
Retry count exceeded; starting again
Fail to get info file!
Init error!
TFTP from server 192.168.254.254; our IP address is 192.168.1.108; sending through gateway 192.168.1.1
Filename 'failed.txt'.
Load address: 0x80200000
Loading: *
Retry count exceeded; starting again
==>use default images
.DHBOOT# run up
TFTP from server 192.168.1.1; our IP address is 192.168.1.108
Filename 'update.img'.
Load address: 0x81a00000
Loading: #################################################################
#################################################################
#################################################################
#################################################################
#################################################################
#################################################################
#################################################################
#################################################################
#################################################################
#################################################################
#################################################################
#################################################################
#################################################################
#####################################
done
Bytes transferred = 12933288 (c558a8 hex)
## Checking Image at 0x81a00040 ...
Header CRC Checking ... OK
Image Name: linux
Image Type: ARM Linux Kernel Image (gzip compressed)
Data Size: 1771176 Bytes = 1.7 MB
Load Address: 02080000
Entry Point: 02280000
Data CRC Checking ... OK
Programing start at: 0x00080000
write : 100%
done
## Checking Image at 0x81bb0728 ...
Header CRC Checking ... OK
Image Name: romfs
Image Type: ARM Linux Kernel Image (gzip compressed)
Data Size: 3100672 Bytes = 3 MB
Load Address: 02280000
Entry Point: 02580000
Data CRC Checking ... OK
Programing start at: 0x00280000
write : 100%
done
## Checking Image at 0x81ea5768 ...
Header CRC Checking ... OK
Image Name: user
Image Type: ARM Linux Kernel Image (gzip compressed)
Data Size: 6221824 Bytes = 5.9 MB
Load Address: 028e0000
Entry Point: 02ee0000
Data CRC Checking ... OK
Programing start at: 0x008e0000
write : 100%
done
## Checking Image at 0x824947a8 ...
Header CRC Checking ... OK
Image Name: web
Image Type: ARM Linux Standalone Program (gzip compressed)
Data Size: 1409024 Bytes = 1.3 MB
Load Address: 02580000
Entry Point: 02780000
Data CRC Checking ... OK
Programing start at: 0x00580000
write : 100%
done
## Checking Image at 0x825ec7e8 ...
Header CRC Checking ... OK
Image Name: data
Image Type: ARM Linux Kernel Image (gzip compressed)
Data Size: 372736 Bytes = 364 kB
Load Address: 02ee0000
Entry Point: 03000000
Data CRC Checking ... OK
Programing start at: 0x00ee0000
write : 100%
done
## Checking Image at 0x82647828 ...
Header CRC Checking ... OK
Image Name: product
Image Type: ARM Linux Standalone Program (gzip compressed)
Data Size: 45056 Bytes = 44 kB
Load Address: 028c0000
Entry Point: 028e0000
Data CRC Checking ... OK
Programing start at: 0x008c0000
write : 100%
done
## Checking Image at 0x82652868 ...
Header CRC Checking ... OK
Image Name: custom
Image Type: ARM Linux Standalone Program (gzip compressed)
Data Size: 12288 Bytes = 12 kB
Load Address: 02060000
Entry Point: 02080000
Data CRC Checking ... OK
Programing start at: 0x00060000
write : 100%
doneJude201186
n3wb
- Jul 6, 2017
- 13
- 0
can you tell me your contact information I need your help ?That's a great post, well done and thanks for sharing!
If / when I get a Dahua camera (not convinced I'll get good functionality with Hikvision NVRs) I suspect it will come in very useful.
Dahua have included / retained a lot of useful functionality in their U-boot, unlike Hikvision who strip it to an almost useless state in pursuit of their 'let's make using our products difficult for our knowledgeable customers' stupid strategy.
alastairstevenson
Staff member
Just post on the forum here - that also lets others contribute, and sharing the problem and solution publicly will also help others.can you tell me your contact information I need your help
Jude201186
n3wb
- Jul 6, 2017
- 13
- 0
NOW dahua also release new Chinese fimware DH_IPC-HX4XXX-Eos_Chn_PN_Stream3_V2.680.0000000.41.R.181212 Does anyone here can modify to English fimware ?if do please contact me :zhudeping2011@vip.163.com
Hi,NOW dahua also release new Chinese fimware DH_IPC-HX4XXX-Eos_Chn_PN_Stream3_V2.680.0000000.41.R.181212 Does anyone here can modify to English fimware ?if do please contact me :zhudeping2011@vip.163.com
You can't modify any signed firmware !
spring2017
n3wb
- Jun 4, 2017
- 6
- 0
I have a broken camera ,and I fogot where I place , so I use a good hdw4433c-a to test , but when connected with serial port , it displays more information , how I interrupt it . as follows:Easy recovery without serial: Dahua IPC EASY unbricking / recovery over TFTP
Hello,
I broke my camera by accident while messing with the firmware and had to recover it.
Since I am not the only one that this has happened to and will probably not stay the last one: Here is a simple tutorial on how to unbrick your Dahua IP camera.
Warning: The cameras serial port is 3.3 Volts, do not try to use RS232 which is 12 Volts!!
For this you need:
First of all you have to locate the RX (receive) and TX (transmit) pins on your camera:
- A broken camera with the bootloader still working - assume it is working if you don't know.
- If you know it is not working, look *here* and don't be afraid to ask
- A serial UART device, such as:
- Raspberry Pi or any other microcontroller/devboard with UART
- USB to serial converter: These can be bought for *very* cheap from china:
- For example the CP2102 USB to UART bridge worked very well for me
- Replace FT232 6Pin USB 2.0 to TTL UART Module Serial Converter CP2102 STC | eBay
- A serial terminal application such as: Putty, GtkTerm, tons of others??
- Connection Settings:
- Baud Rate: 115200
- Parity: None
- Bits: 8
- Stopbits: 1
- Flow control: None
- (CR/LF Auto)
- Working firmware.bin for your device, use the chinese one if you aren't sure!
- A TFTP server
- You should be able to figure this out by using Google.
On my IPC-HFW4431M camera (and probably all other generation 3/Eos cameras) they can be found very easily:
For other cameras this page on the Dahua wiki should prove useful: ResetIPCamera - Dahua Wiki
On most devices the serial port consists of 4 pins/pinheads which are made up of VCC,GND,RX,TX.
You can connect the GND (Ground, -) of your dongle to the metal casing of your camera.
VCC (+) should not be connected.
You can identify the TX (transmit) pin of your camera by connecting it (press wire against pin) with the RX pin of your serial device.
Though be aware that some dongles swap the labels like so:
Dongle says RX, but it is actually TX of the dongle and wants to be connected with RX of the other device.
If you power up your camera and see text scrolling down your terminal you have found the right pin, keep trying if you don't ^^
Now put a brick on your * key with your terminal window in focus.
Try to find the RX (receive) pin of the camera and connect it with the TX pin of your dongle.
Power up the camera, wait a second, if you see the following message you have succeeded:
Code:U-Boot 2010.06-svn3089 (Jul 22 2016 - 19:15:59) DRAM: 1 GiB gBootLogPtr:80b80008. Check spi flash controller v350... Found Spi(cs1) ID: 0xC8 0x40 0x18 0xC8 0x40 0x18 Spi(cs1): Block:64KB Chip:16MB Name:"GD25Q128" partition file version 2 rootfstype squashfs root /dev/mtdblock7 In: serial Out: serial Err: serial TEXT_BASE:81000000 Net: PHY found at 3 Hit any key to stop autoboot: 0 > **********************
Type help to see all available commands:
Code:> help ? - alias for 'help' base - print or set address offset boot - boot default, i.e., run 'bootcmd' bootd - boot default, i.e., run 'bootcmd' bootf - boot from flash bootm - boot application image from memory bootp - boot image via network using BOOTP/TFTP protocol cfgRestore- erase config and backup partition. cmp - memory compare cp - memory copy crc32 - checksum calculation crypt - crypt erasepart- erasepart exit - exit script false - do nothing, unsuccessfully fatinfo - print information about filesystem fatload - load binary file from a dos filesystem fatls - list files in a directory (default /) flwrite - flwrite - write data into FLASH memory fsinfo - print information about filesystems fsload - load binary file from a filesystem image go - start application at address 'addr' help - print command description/usage hwid - hwid - set hardware id and save to flash kload - kload - load uImage file from parttion lip - lip - set local ip address but not save to flash loadb - load binary file over serial line (kermit mode) loady - load binary file over serial line (ymodem mode) logsend - get log buf loop - infinite loop on address range ls - list files in a directory (default /) mac - mac - set mac address and save to flash md - memory display memsize - memsize - set mem size mii - MII utility commands mm - memory modify (auto-incrementing address) mtest - simple RAM read/write test mw - memory write (fill) nm - memory modify (constant address) partition- print partition information ping - send ICMP ECHO_REQUEST to network host printenv- print environment variables rarpboot- boot image via network using RARP/TFTP protocol rdefault- rdefault -recover default env reset - Perform RESET of the CPU run - run commands in an environment variable saveenv - save environment variables to persistent storage setenv - set environment variables sf - SPI flash sub-system showvar - print local hushshell variables sip - sip - set server ip address but not save to flash sleep - delay execution for some time smi - MII utility commands sync_uboot- sync_uboot - sync uboot to uboot-bak test - minimal test like /bin/sh tftpboot- tftpboot- boot image via network using TFTP protocol true - do nothing, successfully uartUp - uartUp- update image via uart using uart4 usleep - delay execution for some time version - print monitor version >
The guys from Dahua have done something right for once and added some helpful commands for us, type printenv to print the U-Boot Environment, you should be able to find these lines among other stuff:
Code:ipaddr=192.168.1.108 gatewayip=192.168.1.1 netmask=255.255.255.0 serverip=192.168.1.4 da=tftp 0x82000000 dhboot.bin.img;flwrite;tftp 0x82000000 dhboot-min.bin.img;flwrite; dr=tftp 0x82000000 romfs-x.squashfs.img; flwrite; dk=tftp 0x82000000 kernel.img;flwrite; du=tftp 0x82000000 user-x.squashfs.img; flwrite dw=tftp 0x82000000 web-x.squashfs.img; flwrite dp=tftp 0x82000000 partition-x.cramfs.img;flwrite; dc=tftp 0x82000000 custom-x.squashfs.img; flwrite up=tftp 0x82000000 update.img;flwrite; tk=tftp 0x82000000 uImage;bootm; dh_keyboard=1 appauto=1
Use setenv to adjust the network settings:
You can test the connection to your PC by runing ping $serverip
- ipaddr -> The IP address of the camera
- setenv ipaddr 192.168.1.108
- gatewayip -> The IP address of your networks gateway (router)
- setenv gatewayip 192.168.1.1
- netmask -> The netmask/subnet of your network
- setenv netmask 255.255.255.0
- servip -> The IP address of your computer (that runs the TFTP server)
- setenv serverip 192.168.1.4
(Okay actually I don't even know if Windows will reply to pings by default - so I guess you can ignore this for now)Code:> ping $serverip ETH0: PHY(phyaddr=-1, rmii) link UP: DUPLEX=FULL : SPEED=100M MAC: 00-12-34-56-78-91 Using gmac device host 192.168.1.4 is alive
Extract the firmware image for your camera somewhere, use some ZIP program like 7zip. It might complain about invalid ZIP file (since Dahua changes the ZIP header from PK to DH) you can either fix the ZIP with a HEX editor or use another program to unzip it.
Start the TFTP server and point it to the files you have extracted from the firmware image.
And now for the final part: Flashing the firmware!
I'll flash following partitions in order:
Do not flash the bootloader! There is no need to and when you fuck that up recovering is a lot harder.
- romfs (root linux filesystem with busybox)
- kernel (The holy Linux Kernel)
- user (Dahuas programs and kernel modules)
- web (Webinterface)
- partition ("Partition table" - text files which describe the layout on the flash chip)
- custom (Language files)
Run following commands one after eachother:
Code:run dr run dk run du run dw run dp run dc
Example output:
Code:> run dr ETH0: PHY(phyaddr=-1, rmii) link UP: DUPLEX=FULL : SPEED=100M MAC: 3C-EF-8C-FA-E7-88 Using gmac device TFTP from server 192.168.1.4; our IP address is 192.168.1.108 Download Filename 'romfs-x.squashfs.img'. Download to address: 0x82000000 Downloading: ################################################# done Bytes transferred = 909376 (de040 hex) ## Checking Image at 82000000 ... Legacy image found Image Name: romfs Image Type: ARM Linux Standalone Program (gzip compressed) Data Size: 909312 Bytes = 888 KiB Load Address: 002f0000 Entry Point: 003d0000 Verifying Checksum ... OK Programing start at: 0x002f0000 SPI probe: 16384 KiB hi_sfc at 0:0 is now current device write : 0% write : 0% write : 7% write : 14% write : 21% write : 28% write : 35% write : 42% write : 50% write : 57% write : 64% write : 71% write : 78% write : 85% write : 92% write : 100% done
You can run save if you want to save the environment variables you have set (ipaddr, servip, ..).
Run boot to boot the camera
Congratulations!
(If you just read this for fun and do not have a bricked camera I still suggest you to buy a serial UART dongle, they're cheaper than most snacks and you can save lots of devices with it!)
(If this helped you and you have some spare for a student: paypal.me/BotoX)
▒
U-Boot 2010.06-svn4537 (Dec 14 2017 - 05:06:35)
DRAM: 1 GiB
gBootLogPtr:80b80008.
Check spi flash controller v350... Found
Spi(cs1) ID: 0xC8 0x40 0x18 0xC8 0x40 0x18
Spi(cs1): Block:64KB Chip:16MB Name:"GD25Q128"
partition file version 2
rootfstype squashfs root /dev/mtdblock7
In: serial
Out: serial
Err: serial
TEXT_BASE:81000000
Net: PHY found at 3
ETH0: PHY(phyaddr=-1, rmii) not link!
Try again use backup_serverip
ETH0: PHY(phyaddr=-1, rmii) not link!
Failed to get info.txt
Fail to get info file!
Init error!
ETH0: PHY(phyaddr=-1, rmii) not link!
## Booting kernel from Legacy Image at 82000000 ...
Image Name: Linux-3.4.35
Image Type: ARM Linux Kernel Image (uncompressed)
Data Size: 1453664 Bytes = 1.4 MiB
Load Address: 80008000
Entry Point: 80008000
Loading Kernel Image ...OK
OK
partition file version 2
rootfstype squashfs root /dev/mtdblock7
fail to load bootargsParameters.txt
fail to load bootargsParameters.txt file
get bootargs info failed
cmdLine mem=85M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs
crashflasg:1, logmagic:54410011.
Starting kernel ...
Uncompressing Linux... done, booting the kernel.
U-Boot 2010.06-svn4537 (Dec 14 2017 - 05:06:35)
DRAM: 1 GiB
gBootLogPtr:80b80008.
Check spi flash controller v350... Found
Spi(cs1) ID: 0xC8 0x40 0x18 0xC8 0x40 0x18
Spi(cs1): Block:64KB Chip:16MB Name:"GD25Q128"
partition file version 2
rootfstype squashfs root /dev/mtdblock7
In: serial
Out: serial
Err: serial
TEXT_BASE:81000000
Net: PHY found at 3
ETH0: PHY(phyaddr=-1, rmii) not link!
Try again use backup_serverip
ETH0: PHY(phyaddr=-1, rmii) not link!
Failed to get info.txt
Fail to get info file!
Init error!
ETH0: PHY(phyaddr=-1, rmii) not link!
## Booting kernel from Legacy Image at 82000000 ...
Image Name: Linux-3.4.35
Image Type: ARM Linux Kernel Image (uncompressed)
Data Size: 1453664 Bytes = 1.4 MiB
Load Address: 80008000
Entry Point: 80008000
Loading Kernel Image ...OK
OK
partition file version 2
rootfstype squashfs root /dev/mtdblock7
fail to load bootargsParameters.txt
fail to load bootargsParameters.txt file
get bootargs info failed
cmdLine mem=85M console=ttyS0,115200 root=/dev/mtdblock7 rootfstype=squashfs
crashflasg:1, logmagic:54410011.
Starting kernel ...
Uncompressing Linux... done, booting the kernel.
As an eBay Associate IPCamTalk earns from qualifying purchases.
Привет родимые!
Проблема с DVR Dahua DHI-NVR2104-S2 2016 года выпуска.
Во время загрузки висит на Логотип Dahua затем через 2 минуты уходит в перезагрузку и так постоянно.
Подключение к USB-TTL, и вот что он мне дал:
U-Boot 2010,06-svn2926 (13 октября 2017 - 15:09:30)
Проверка флэш-памяти контроллера V100 ... Найдено
SPI-Нор (CS 0) ID: 0xC2 0x20 0x18
Блок: 64KB Chip: 16Мб Название: "MX25L128XX"
SPI Nor Общий размер: 16Мб
Окружающая среда SPI флэш инициализируется
В: последовательный
Выход: последовательный
Err: последовательный
Тип чипа hi3520dv300
===============================================
DPLL: 400Mhz DDR: 1600МГц
APLL: 800Mhz VPLL0: 162Mhz
===============================================
miiphy_link, 524,7849
miiphy_duplex, 416,0
miiphy_speed, 345,0
Eth0: PHY (phyaddr = 0, rgmii) связать: ДУПЛЕКСА = HALF: СКОРОСТЬ = 10M
MAC: 4C-11-BF-6F-9F-8B
PHY ID: 0x1cc816
хорошая находка PHY RTL8201 на higmac
hwid_gpio_val = 0x18
hwid_gpio_val = 0x18
hwid_gpio_val = 0x18
hwid_gpio_val = 0x18
hwid_gpio_val = 0x18
DDR: 256M
Нажмите любую клавишу, чтобы остановить AutoBoot: 0
USB-устройство не найдено
### Cramfs загрузки 'bmp_logo.bmp' в 0x81000000
BMPW: 300 BMPH: 113 бит: 16 biSizeImage: 67802 bmp_size = 67802
miiphy_link, 524,7849
miiphy_duplex, 416,0
miiphy_speed, 345,0
Eth0: PHY (phyaddr = 0, RMII) связать: ДУПЛЕКСА = HALF: СКОРОСТЬ = 10M
MAC: 4C-11-BF-6F-9F-8B
TFTP с сервера 192.168.254.254; наш IP-адрес 192.168.1.108; отправка через шлюз 192.168.1.1
Скачать файл «ID_2G02990PAZ00274.txt».
Скачать по адресу: 0x82000000
Загрузка: TTT
Превышено допустимое число попыток; начиная снова
TFTP получать не удалось, пожалуйста, проверьте чистую окружающую среду
### SquashFS загрузки '/ загрузки / uImage' для 0x82000000
## Загрузка ядра из Наследства изображения на 82000000 ...
Название изображения: Linux-3.10.0
Тип изображения: ARM Linux Kernel Image (несжатый)
Размер данных: 2193464 байт = 2,1 MiB
Нагрузка Адрес: 80008000
Точка входа: 80008000
Загрузка образа ядра ... OK
Хорошо
Запуск ядра ...
Распаковка Linux ... сделано, загрузка ядра.
Скажите мне, что вы можете делать с ним?
Проблема с DVR Dahua DHI-NVR2104-S2 2016 года выпуска.
Во время загрузки висит на Логотип Dahua затем через 2 минуты уходит в перезагрузку и так постоянно.
Подключение к USB-TTL, и вот что он мне дал:
U-Boot 2010,06-svn2926 (13 октября 2017 - 15:09:30)
Проверка флэш-памяти контроллера V100 ... Найдено
SPI-Нор (CS 0) ID: 0xC2 0x20 0x18
Блок: 64KB Chip: 16Мб Название: "MX25L128XX"
SPI Nor Общий размер: 16Мб
Окружающая среда SPI флэш инициализируется
В: последовательный
Выход: последовательный
Err: последовательный
Тип чипа hi3520dv300
===============================================
DPLL: 400Mhz DDR: 1600МГц
APLL: 800Mhz VPLL0: 162Mhz
===============================================
miiphy_link, 524,7849
miiphy_duplex, 416,0
miiphy_speed, 345,0
Eth0: PHY (phyaddr = 0, rgmii) связать: ДУПЛЕКСА = HALF: СКОРОСТЬ = 10M
MAC: 4C-11-BF-6F-9F-8B
PHY ID: 0x1cc816
хорошая находка PHY RTL8201 на higmac
hwid_gpio_val = 0x18
hwid_gpio_val = 0x18
hwid_gpio_val = 0x18
hwid_gpio_val = 0x18
hwid_gpio_val = 0x18
DDR: 256M
Нажмите любую клавишу, чтобы остановить AutoBoot: 0
USB-устройство не найдено
### Cramfs загрузки 'bmp_logo.bmp' в 0x81000000
BMPW: 300 BMPH: 113 бит: 16 biSizeImage: 67802 bmp_size = 67802
miiphy_link, 524,7849
miiphy_duplex, 416,0
miiphy_speed, 345,0
Eth0: PHY (phyaddr = 0, RMII) связать: ДУПЛЕКСА = HALF: СКОРОСТЬ = 10M
MAC: 4C-11-BF-6F-9F-8B
TFTP с сервера 192.168.254.254; наш IP-адрес 192.168.1.108; отправка через шлюз 192.168.1.1
Скачать файл «ID_2G02990PAZ00274.txt».
Скачать по адресу: 0x82000000
Загрузка: TTT
Превышено допустимое число попыток; начиная снова
TFTP получать не удалось, пожалуйста, проверьте чистую окружающую среду
### SquashFS загрузки '/ загрузки / uImage' для 0x82000000
## Загрузка ядра из Наследства изображения на 82000000 ...
Название изображения: Linux-3.10.0
Тип изображения: ARM Linux Kernel Image (несжатый)
Размер данных: 2193464 байт = 2,1 MiB
Нагрузка Адрес: 80008000
Точка входа: 80008000
Загрузка образа ядра ... OK
Хорошо
Запуск ядра ...
Распаковка Linux ... сделано, загрузка ядра.
Скажите мне, что вы можете делать с ним?
Никаких проблем нет с этим уже давно, читай форум и инструкции по восстановлению или сбросу конфигов.
Остановить загрузку
Дальше
setenv dh_keyboard 0
saveenv
reset
Увидишь причину падения и работу watchdog
А дальше помодульное восстановление или через update.img, специальный файл.
Прошивки все доступны, как и русскоязычные форумы, а то тут админы и некоторые начнут ворчать, что ты бы еще на клингонском бы написал и т.п., ..
Остановить загрузку
Дальше
setenv dh_keyboard 0
saveenv
reset
Увидишь причину падения и работу watchdog
А дальше помодульное восстановление или через update.img, специальный файл.
Прошивки все доступны, как и русскоязычные форумы, а то тут админы и некоторые начнут ворчать, что ты бы еще на клингонском бы написал и т.п., ..
Thanks friend! Tell me at least what topics to read to restore it?Никаких проблем нет с этим уже давно, читай форум и инструкции по восстановлению или сбросу конфигов.
Остановить загрузку
Дальше
setenv dh_keyboard 0
saveenv
reset
Увидишь причину падения и работу watchdog
А дальше помодульное восстановление или через update.img, специальный файл.
Прошивки все доступны, как и русскоязычные форумы, а то тут админы и некоторые начнут ворчать, что ты бы еще на клингонском бы написал и т.п., ..
Alessio831
n3wb
simonchan
n3wb
Звиняй комрад, пропустил постThanks friend! Tell me at least what topics to read to restore it?
http://itunedvr.ru/_ftp/DAHUA/config_reset.doc
http://itunedvr.ru/_ftp/DAHUA/upgrade_tools_and_users_manual.rar