The fact that the difference in the sum when you compare 2 cameras isn't the same doesn't necessarily mean it's not still a checksum-16, if that makes sense. There may be other camera-specific bytes excluded or included, in the final value.
If you are prepared to experiment with a little risk, you may well be able to simply change the checksum by the same amount that you change something like the language byte, instead of a recalculate.
I was hoping to test that out on my latest purchase, but unfortunately (or not) it was a late 2014 manufacture so didn't have the new checksum, it's quite happy to be changed.
But you may be able to experiment if you give yourself a way back by taking a copy of all the of all the camera flash storage as a first step.
If you can add a NAS storage destination at the web GUI, you don't have to format it to be able to use it, even if it's very large. As long as the 'Test' button is OK.
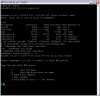
At an SSH or telnet prompt, use 'mount' to check the path used by the NAS storage. Let's say it's /mnt/nfs00 if it's an NFS share.
cd /mnt/nfs00
cat /dev/mtdblock0 > mtdblock0
And repeat up to mtdblock17, but omit block8 & 16, do them like this:
cat /dev/mtd8ro > mtd8ro
cat /dev/mtd16ro > mtd16ro
Edit your mtdblock5 & 6 for the language byte and checksum.
Put it back like so:
cat mtdblock5 > /dev/mtdblock5
cat mtdblock6 > /dev/mtdblock6
reboot
If the camera does not boot fully - it's quite likely (but not guaranteed) that it will sit on the 192.0.0.64 IP address with a telnet daemon running, in which case you can connect to it and restore the original mtdblock5 & 6
Of course your PC will need to be on the same network segment - use 192.0.0.128 which will also help with when you use
TFTP to change the firmware.
And if that doesn't work - do you have a serial TTL to USB convertor?
*edit* Just a final thought - if a camera does 'brick' but the telnet access works, you may be able to get an idea of what the problem is by using
cat /proc/kmsg
and inspecting a large cryptic log. I upgraded a 5.2.0 camera to 5.2.3, should have been perfectly safe, but it didn't start up after. kmsg complained 'not unpacking initramfs - junk in it' or some such. Somehow it had become corrupted. So I restored mtdblock11 where initrd resides and it cam back to life.
*edit2* I'm assuming that it's known that Checksum-16 is a simple sum of its parts, and not something like a CRC.